📣 New Listing | Jucoin will list Token: $MIAI (MysteryIslandAI)
🌟 Open trading pair: $MIAI/USDT
💵 Open deposit/withdrawal: 2025/08/20 | 17:00 (UTC+7)
♻️ Open trading: 2025/08/21 | 17:00 (UTC+7)
👉Register for JuCoin now: https://bit.ly/3BVxlZ2
👉Details: https://support.jucoin.blog/hc/en-001/articles/49837871094041
#JuCoin #JuCoinVietnam #MIAI #MysteryIslandA I #JuCoinListing #NewListing


Lee Jucoin
2025-08-18 06:27
📣Jucoin will list Token: $MIAI (MysteryIslandAI)
Disclaimer:Contains third-party content. Not financial advice.
See Terms and Conditions.
What Are 3Commas Pricing Tiers?
Understanding the different pricing options available on 3Commas is essential for traders looking to optimize their cryptocurrency trading strategies. As a platform that caters to both beginners and seasoned professionals, 3Commas offers a tiered subscription model designed to meet varying needs and budgets. This article provides an in-depth overview of these tiers, their features, target audiences, and recent platform updates.
Overview of 3Commas as a Cryptocurrency Trading Platform
Founded in 2017 by Yuriy Serdyuk and Oleksandr Lutskevych, 3Commas has established itself as a leading tool in the crypto trading space. Its user-friendly interface combined with powerful automation tools has attracted traders worldwide. The platform supports multiple exchanges such as Binance, Coinbase Pro, Kraken, and others—allowing users to manage diverse portfolios seamlessly.
Key features include automated trading bots that execute trades based on predefined strategies, backtesting tools for strategy validation before live deployment, and social trading functionalities where users can follow or copy successful traders. These capabilities make it suitable for both novices exploring automated trading and professional traders seeking advanced algorithmic solutions.
The Three Main Pricing Tiers
As of now, 3Commas offers three primary subscription plans: Free, Premium (at $34/month), and Pro (at $99/month). Each tier is structured to provide increasing levels of access to features aligned with trader experience levels.
Free Plan: Entry-Level Access
The free plan serves as an excellent starting point for newcomers interested in exploring automated crypto trading without financial commitment. It includes basic functionalities such as limited access to simple trading bots—often one or two—and some backtesting capabilities. However, these are restricted compared to paid plans; users can only trade on select pairs with limited customization options.
This tier is ideal for those who want hands-on experience with minimal risk or cost before deciding whether more advanced tools are necessary. It also allows new traders to familiarize themselves with the platform’s interface while testing initial strategies.
Premium Plan: Intermediate Features at $34/Month
Designed for active traders seeking more control over their automation strategies without breaking the bank, the Premium plan unlocks full backtesting capabilities—a crucial feature for refining algorithms before deploying them live. Users gain access to a broader range of trading pairs and customizable bot settings that enable more sophisticated trade execution.
Priority customer support is another benefit here; this ensures quicker assistance when technical issues arise or strategic questions need addressing. Overall, this plan strikes a balance between affordability and functionality suitable for intermediate-level traders aiming to enhance their performance through automation.
Pro Plan: Advanced Tools at $99/Month
The most comprehensive offering from 3Commas targets professional or highly active crypto traders who require cutting-edge features. The Pro plan includes customizable algorithms powered by real-time data feeds—providing more accurate market insights—and dedicated account management services tailored toward high-frequency or large-volume trades.
Exclusive content such as premium signals and detailed market analysis further empowers users making complex decisions quickly within volatile markets. This tier demands higher investment but delivers tools suited for those operating at an institutional level or managing significant portfolios requiring personalized support.
Recent Platform Developments Enhancing User Experience
In recent months, 3Commas has focused heavily on expanding its ecosystem through several key updates:
Integration With Additional Exchanges: By partnering with new platforms like Bitfinex and Huobi Global recently integrated into its system—users now have access to even wider liquidity pools.
Enhanced Security Measures: Recognizing the importance of safeguarding user assets amid rising cyber threats in crypto space—the platform introduced two-factor authentication improvements along with stronger encryption protocols.
Community Engagement Initiatives: Active communication channels via social media forums allow users feedback-driven development cycles; this helps tailor future updates based on actual trader needs rather than assumptions alone.
These enhancements demonstrate how committed 3Commas remains towards providing secure yet innovative solutions tailored toward evolving market demands.
Potential Risks Associated With Subscription Tiers
While flexible pricing makes it accessible across various trader profiles—including beginners—the reliance on paid plans introduces certain risks:
Cost Considerations: For individual hobbyists or small-scale investors operating under tight budgets—especially those considering the Pro plan—the monthly expense might be prohibitive relative to expected gains.
Dependence On Technology & Data Feeds: Automated systems rely heavily on stable internet connections plus accurate real-time data feeds; any disruption could impact trade execution adversely.
Regulatory Environment Changes: As governments worldwide tighten regulations around cryptocurrencies—and some exchanges face restrictions—the integration capabilities offered by platforms like 3Commas could be affected unexpectedly.
Being aware of these factors helps ensure informed decision-making when choosing an appropriate subscription level aligned with personal risk tolerance and operational requirements.
Who Should Choose Which Tier?
Selecting the right plan depends largely on your experience level:
- Beginners should start with the free version—to learn how automated bots work without financial exposure—and upgrade later if needed.
- Intermediate traders aiming for better customization should consider upgrading to Premium ($34/month) once comfortable managing multiple pairs simultaneously.
- Professional operators executing high-frequency trades—or managing large portfolios—are best served by investing in Pro ($99/month), which offers advanced algorithms coupled with dedicated support services.
Final Thoughts: Making Informed Choices Based On Your Trading Goals
Understanding what each pricing tier offers enables you not only maximize your investment but also align your choice closely with your skill set — whether you're just starting out or already operating at an expert level within cryptocurrency markets.
By staying updated about recent developments like exchange integrations or security upgrades—as well as being mindful of potential risks—you can leverage platforms like 3Commas effectively while minimizing vulnerabilities associated with reliance solely on technology-driven solutions.
Keywords: cryptocurrency trading platforms | automated crypto bots | crypto exchange integration | backtesting tools | social trading | crypto portfolio management | beginner vs professional trader | subscription plans comparison


JCUSER-IC8sJL1q
2025-05-26 14:37
What are 3Commas pricing tiers?
What Are 3Commas Pricing Tiers?
Understanding the different pricing options available on 3Commas is essential for traders looking to optimize their cryptocurrency trading strategies. As a platform that caters to both beginners and seasoned professionals, 3Commas offers a tiered subscription model designed to meet varying needs and budgets. This article provides an in-depth overview of these tiers, their features, target audiences, and recent platform updates.
Overview of 3Commas as a Cryptocurrency Trading Platform
Founded in 2017 by Yuriy Serdyuk and Oleksandr Lutskevych, 3Commas has established itself as a leading tool in the crypto trading space. Its user-friendly interface combined with powerful automation tools has attracted traders worldwide. The platform supports multiple exchanges such as Binance, Coinbase Pro, Kraken, and others—allowing users to manage diverse portfolios seamlessly.
Key features include automated trading bots that execute trades based on predefined strategies, backtesting tools for strategy validation before live deployment, and social trading functionalities where users can follow or copy successful traders. These capabilities make it suitable for both novices exploring automated trading and professional traders seeking advanced algorithmic solutions.
The Three Main Pricing Tiers
As of now, 3Commas offers three primary subscription plans: Free, Premium (at $34/month), and Pro (at $99/month). Each tier is structured to provide increasing levels of access to features aligned with trader experience levels.
Free Plan: Entry-Level Access
The free plan serves as an excellent starting point for newcomers interested in exploring automated crypto trading without financial commitment. It includes basic functionalities such as limited access to simple trading bots—often one or two—and some backtesting capabilities. However, these are restricted compared to paid plans; users can only trade on select pairs with limited customization options.
This tier is ideal for those who want hands-on experience with minimal risk or cost before deciding whether more advanced tools are necessary. It also allows new traders to familiarize themselves with the platform’s interface while testing initial strategies.
Premium Plan: Intermediate Features at $34/Month
Designed for active traders seeking more control over their automation strategies without breaking the bank, the Premium plan unlocks full backtesting capabilities—a crucial feature for refining algorithms before deploying them live. Users gain access to a broader range of trading pairs and customizable bot settings that enable more sophisticated trade execution.
Priority customer support is another benefit here; this ensures quicker assistance when technical issues arise or strategic questions need addressing. Overall, this plan strikes a balance between affordability and functionality suitable for intermediate-level traders aiming to enhance their performance through automation.
Pro Plan: Advanced Tools at $99/Month
The most comprehensive offering from 3Commas targets professional or highly active crypto traders who require cutting-edge features. The Pro plan includes customizable algorithms powered by real-time data feeds—providing more accurate market insights—and dedicated account management services tailored toward high-frequency or large-volume trades.
Exclusive content such as premium signals and detailed market analysis further empowers users making complex decisions quickly within volatile markets. This tier demands higher investment but delivers tools suited for those operating at an institutional level or managing significant portfolios requiring personalized support.
Recent Platform Developments Enhancing User Experience
In recent months, 3Commas has focused heavily on expanding its ecosystem through several key updates:
Integration With Additional Exchanges: By partnering with new platforms like Bitfinex and Huobi Global recently integrated into its system—users now have access to even wider liquidity pools.
Enhanced Security Measures: Recognizing the importance of safeguarding user assets amid rising cyber threats in crypto space—the platform introduced two-factor authentication improvements along with stronger encryption protocols.
Community Engagement Initiatives: Active communication channels via social media forums allow users feedback-driven development cycles; this helps tailor future updates based on actual trader needs rather than assumptions alone.
These enhancements demonstrate how committed 3Commas remains towards providing secure yet innovative solutions tailored toward evolving market demands.
Potential Risks Associated With Subscription Tiers
While flexible pricing makes it accessible across various trader profiles—including beginners—the reliance on paid plans introduces certain risks:
Cost Considerations: For individual hobbyists or small-scale investors operating under tight budgets—especially those considering the Pro plan—the monthly expense might be prohibitive relative to expected gains.
Dependence On Technology & Data Feeds: Automated systems rely heavily on stable internet connections plus accurate real-time data feeds; any disruption could impact trade execution adversely.
Regulatory Environment Changes: As governments worldwide tighten regulations around cryptocurrencies—and some exchanges face restrictions—the integration capabilities offered by platforms like 3Commas could be affected unexpectedly.
Being aware of these factors helps ensure informed decision-making when choosing an appropriate subscription level aligned with personal risk tolerance and operational requirements.
Who Should Choose Which Tier?
Selecting the right plan depends largely on your experience level:
- Beginners should start with the free version—to learn how automated bots work without financial exposure—and upgrade later if needed.
- Intermediate traders aiming for better customization should consider upgrading to Premium ($34/month) once comfortable managing multiple pairs simultaneously.
- Professional operators executing high-frequency trades—or managing large portfolios—are best served by investing in Pro ($99/month), which offers advanced algorithms coupled with dedicated support services.
Final Thoughts: Making Informed Choices Based On Your Trading Goals
Understanding what each pricing tier offers enables you not only maximize your investment but also align your choice closely with your skill set — whether you're just starting out or already operating at an expert level within cryptocurrency markets.
By staying updated about recent developments like exchange integrations or security upgrades—as well as being mindful of potential risks—you can leverage platforms like 3Commas effectively while minimizing vulnerabilities associated with reliance solely on technology-driven solutions.
Keywords: cryptocurrency trading platforms | automated crypto bots | crypto exchange integration | backtesting tools | social trading | crypto portfolio management | beginner vs professional trader | subscription plans comparison
Disclaimer:Contains third-party content. Not financial advice.
See Terms and Conditions.
Proof-of-Stake (PoS) Explained: A Clear Guide for Beginners and Enthusiasts
Understanding Proof-of-Stake (PoS) is essential for anyone interested in blockchain technology, cryptocurrencies, or the future of decentralized networks. As an alternative to the traditional Proof-of-Work (PoW), PoS offers a more energy-efficient and scalable way to secure blockchain networks. This article breaks down what PoS is, how it works, its advantages and challenges, recent developments, and what it means for the future of digital currencies.
What Is Proof-of-Stake (PoS)?
Proof-of-Stake is a consensus mechanism used by blockchain networks to validate transactions and add new blocks to the chain. Unlike PoW—used by Bitcoin—that requires miners to solve complex mathematical puzzles using powerful computers, PoS relies on validators who "stake" their own cryptocurrency as collateral. This staking process helps ensure that validators act honestly because they stand to lose their staked assets if they attempt malicious activities.
In simple terms, think of PoS as a system where your chance of being chosen to create the next block depends on how much cryptocurrency you commit or "lock up" in the network. The more you stake, the higher your chances are of being selected as a validator.
How Does Proof-of-Stake Work?
The process involves several key steps:
Validator Selection: In a PoS network, validators are chosen based on their stake—the amount of cryptocurrency they have committed. Larger stakes increase their probability of being selected to propose new blocks.
Staking Cryptocurrency: Validators lock up or "stake" their coins for a specific period as collateral. This act aligns their interests with maintaining network integrity because dishonest behavior could lead them losing their staked assets.
Creating New Blocks: When selected, validators verify transactions and assemble them into new blocks before broadcasting these blocks across the network.
Earning Rewards: Successful validation results in rewards—typically newly minted coins plus transaction fees—distributed proportionally based on each validator's stake.
This system creates an economic incentive structure that promotes honesty while reducing energy consumption compared to traditional mining methods.
Advantages of Proof-of-Stake
Proof-of-Stake offers several notable benefits:
Energy Efficiency: Since PoS does not require intensive computational work like PoW mining rigs do, it consumes significantly less electricity—a critical factor amid growing environmental concerns surrounding cryptocurrencies.
Enhanced Scalability: With more validators able to participate simultaneously without heavy hardware requirements, many PoS-based networks can process transactions faster than traditional systems.
Decentralization Potential: While centralization risks exist if large stakeholders dominate voting power—which we'll discuss later—PoS allows broader participation since validating doesn't depend solely on expensive hardware.
Security Through Economic Incentives: Validators risk losing their staked coins if they behave maliciously or attempt fraud—a deterrent against attacks such as double-spending or manipulation attempts.
Recent Adoption Trends
Major blockchain projects have adopted or are transitioning toward proof-of-stake mechanisms due to these advantages:
Ethereum 2.0 Transition: Ethereum’s move from proof-of-work towards Ethereum 2.0 marks one of the most significant shifts in blockchain history aimed at improving scalability and reducing energy consumption.
Other Networks Using PoS: Platforms like Polkadot, Solana, Cosmos, Cardano—and many others—have implemented variations of proof-of-stake consensus algorithms successfully managing high transaction throughput with lower environmental impact.
These developments reflect industry confidence that PoS can support large-scale decentralized applications while addressing sustainability concerns associated with older models like Bitcoin’s proof-of-work system.
Challenges Facing Proof-of-Stake
Despite its benefits; however,
Centralization Risks: Large stakeholders may accumulate disproportionate influence over validator selection processes—a phenomenon known as "wealth concentration." If few entities control most stakes—they could potentially manipulate governance decisions or censor certain transactions—undermining decentralization principles fundamental to blockchain technology.
Security Vulnerabilities: Certain attack vectors unique to PoS systems exist—for example:
- Nothing-at-stake attacks: Validators might vote for multiple conflicting chains because there's little cost involved without physical resource expenditure.
- Long-range attacks: Attackers could try rewriting parts of historical data if initial security measures aren’t robust enough.
Regulatory Uncertainty: As governments scrutinize cryptocurrencies more closely—including staking practices—the regulatory landscape remains uncertain which could impact adoption rates and operational frameworks moving forward.
Emerging Trends & Future Outlook
The evolution within proof-of-stake protocols continues rapidly:
Innovations such as Delegated Proof-of-Stake (DPoS)—where token holders delegate validation rights—aim at further democratizing participation while enhancing efficiency.
Concepts like Proof-of-Stake Velocity seek solutions for centralization by factoring in how often tokens change hands rather than just total holdings alone.
As technological advancements address current limitations—for instance through better slashing mechanisms that penalize bad actors—the long-term outlook suggests increased adoption across various sectors beyond cryptocurrencies—including supply chain management and digital identity verification.
Implications for Investors & Users
For investors considering staking opportunities:
- Staking can generate passive income through rewards but also involves risks such as potential loss ("slashing") if validators act dishonestly or fail technically.
For everyday users:
- Understanding whether a platform uses proof-or-stakes helps assess its sustainability profile; eco-friendly blockchains tend toward broader acceptance among environmentally conscious communities.
Final Thoughts on Proof-and Stake Systems
Proof-and-stakes represent an innovative shift towards greener—and potentially more scalable—blockchain ecosystems compared with traditional mining-based models. While challenges remain around decentralization security vulnerabilities—and regulatory clarity—the ongoing development indicates strong momentum toward mainstream adoption across various industries worldwide.
Keywords: Blockchain consensus mechanisms | Cryptocurrency validation | Energy-efficient blockchains | Validator staking | Blockchain scalability | Decentralized finance (DeFi) security


JCUSER-WVMdslBw
2025-05-22 15:45
Could you explain "Proof-of-Stake" (PoS) in simple terms?
Proof-of-Stake (PoS) Explained: A Clear Guide for Beginners and Enthusiasts
Understanding Proof-of-Stake (PoS) is essential for anyone interested in blockchain technology, cryptocurrencies, or the future of decentralized networks. As an alternative to the traditional Proof-of-Work (PoW), PoS offers a more energy-efficient and scalable way to secure blockchain networks. This article breaks down what PoS is, how it works, its advantages and challenges, recent developments, and what it means for the future of digital currencies.
What Is Proof-of-Stake (PoS)?
Proof-of-Stake is a consensus mechanism used by blockchain networks to validate transactions and add new blocks to the chain. Unlike PoW—used by Bitcoin—that requires miners to solve complex mathematical puzzles using powerful computers, PoS relies on validators who "stake" their own cryptocurrency as collateral. This staking process helps ensure that validators act honestly because they stand to lose their staked assets if they attempt malicious activities.
In simple terms, think of PoS as a system where your chance of being chosen to create the next block depends on how much cryptocurrency you commit or "lock up" in the network. The more you stake, the higher your chances are of being selected as a validator.
How Does Proof-of-Stake Work?
The process involves several key steps:
Validator Selection: In a PoS network, validators are chosen based on their stake—the amount of cryptocurrency they have committed. Larger stakes increase their probability of being selected to propose new blocks.
Staking Cryptocurrency: Validators lock up or "stake" their coins for a specific period as collateral. This act aligns their interests with maintaining network integrity because dishonest behavior could lead them losing their staked assets.
Creating New Blocks: When selected, validators verify transactions and assemble them into new blocks before broadcasting these blocks across the network.
Earning Rewards: Successful validation results in rewards—typically newly minted coins plus transaction fees—distributed proportionally based on each validator's stake.
This system creates an economic incentive structure that promotes honesty while reducing energy consumption compared to traditional mining methods.
Advantages of Proof-of-Stake
Proof-of-Stake offers several notable benefits:
Energy Efficiency: Since PoS does not require intensive computational work like PoW mining rigs do, it consumes significantly less electricity—a critical factor amid growing environmental concerns surrounding cryptocurrencies.
Enhanced Scalability: With more validators able to participate simultaneously without heavy hardware requirements, many PoS-based networks can process transactions faster than traditional systems.
Decentralization Potential: While centralization risks exist if large stakeholders dominate voting power—which we'll discuss later—PoS allows broader participation since validating doesn't depend solely on expensive hardware.
Security Through Economic Incentives: Validators risk losing their staked coins if they behave maliciously or attempt fraud—a deterrent against attacks such as double-spending or manipulation attempts.
Recent Adoption Trends
Major blockchain projects have adopted or are transitioning toward proof-of-stake mechanisms due to these advantages:
Ethereum 2.0 Transition: Ethereum’s move from proof-of-work towards Ethereum 2.0 marks one of the most significant shifts in blockchain history aimed at improving scalability and reducing energy consumption.
Other Networks Using PoS: Platforms like Polkadot, Solana, Cosmos, Cardano—and many others—have implemented variations of proof-of-stake consensus algorithms successfully managing high transaction throughput with lower environmental impact.
These developments reflect industry confidence that PoS can support large-scale decentralized applications while addressing sustainability concerns associated with older models like Bitcoin’s proof-of-work system.
Challenges Facing Proof-of-Stake
Despite its benefits; however,
Centralization Risks: Large stakeholders may accumulate disproportionate influence over validator selection processes—a phenomenon known as "wealth concentration." If few entities control most stakes—they could potentially manipulate governance decisions or censor certain transactions—undermining decentralization principles fundamental to blockchain technology.
Security Vulnerabilities: Certain attack vectors unique to PoS systems exist—for example:
- Nothing-at-stake attacks: Validators might vote for multiple conflicting chains because there's little cost involved without physical resource expenditure.
- Long-range attacks: Attackers could try rewriting parts of historical data if initial security measures aren’t robust enough.
Regulatory Uncertainty: As governments scrutinize cryptocurrencies more closely—including staking practices—the regulatory landscape remains uncertain which could impact adoption rates and operational frameworks moving forward.
Emerging Trends & Future Outlook
The evolution within proof-of-stake protocols continues rapidly:
Innovations such as Delegated Proof-of-Stake (DPoS)—where token holders delegate validation rights—aim at further democratizing participation while enhancing efficiency.
Concepts like Proof-of-Stake Velocity seek solutions for centralization by factoring in how often tokens change hands rather than just total holdings alone.
As technological advancements address current limitations—for instance through better slashing mechanisms that penalize bad actors—the long-term outlook suggests increased adoption across various sectors beyond cryptocurrencies—including supply chain management and digital identity verification.
Implications for Investors & Users
For investors considering staking opportunities:
- Staking can generate passive income through rewards but also involves risks such as potential loss ("slashing") if validators act dishonestly or fail technically.
For everyday users:
- Understanding whether a platform uses proof-or-stakes helps assess its sustainability profile; eco-friendly blockchains tend toward broader acceptance among environmentally conscious communities.
Final Thoughts on Proof-and Stake Systems
Proof-and-stakes represent an innovative shift towards greener—and potentially more scalable—blockchain ecosystems compared with traditional mining-based models. While challenges remain around decentralization security vulnerabilities—and regulatory clarity—the ongoing development indicates strong momentum toward mainstream adoption across various industries worldwide.
Keywords: Blockchain consensus mechanisms | Cryptocurrency validation | Energy-efficient blockchains | Validator staking | Blockchain scalability | Decentralized finance (DeFi) security
Disclaimer:Contains third-party content. Not financial advice.
See Terms and Conditions.
📰 Circle reports Q2 revenue growth of $658 million, driven by a 90% increase in USDC circulation to $65.2 billion.
⚠️ Despite posting a net loss of $482 million due to IPO expenses, adjusted EBITDA increased 52% to $126 million, demonstrating strong operating performance.
🔎 Read more: https://blog.jucoin.com/circle-q2-earnings-usdc-analysis/
#JuCoin #JuCoinVietnam #USDC #Circle #CryptoNews #Crypto #DeFi #Web3 #Blockchain


Lee Jucoin
2025-08-19 06:39
🌟 Circle Q2 2025 Financial Report: USDC Revenue Soars 53%!
Disclaimer:Contains third-party content. Not financial advice.
See Terms and Conditions.
How to Evaluate the Sustainability of Net Income
Understanding whether a company's net income is sustainable is essential for investors, analysts, and business leaders aiming to gauge long-term financial health. Sustainable net income indicates that a company can maintain its profitability over time without depleting resources or risking environmental and social responsibilities. This article explores key factors, recent trends, and practical methods to assess the sustainability of net income effectively.
What Does Sustainability in Net Income Mean?
Sustainability in net income refers to a company's ability to generate consistent profits over an extended period while balancing economic viability with environmental stewardship and social responsibility. Unlike short-term earnings spikes driven by one-off events or market anomalies, sustainable net income reflects underlying operational strength and strategic resilience.
Achieving this balance involves evaluating not just financial metrics but also how environmental practices and societal impacts influence long-term performance. Investors increasingly prioritize companies that demonstrate responsible management of resources alongside steady profitability.
Key Financial Indicators for Assessing Sustainability
Financial health forms the foundation of sustainable net income. Several indicators help determine whether a company's profits are likely to persist:
- Profitability Trends: Consistent or growing profit margins suggest stable operations capable of weathering market fluctuations.
- Cash Flow Stability: Positive cash flow ensures ongoing liquidity necessary for investments, debt repayment, and operational needs.
- Debt Levels: Maintaining manageable debt ratios prevents financial distress; excessive leverage can threaten future earnings stability.
Regular analysis of these metrics helps identify companies with resilient financial structures capable of supporting sustained profitability.
Economic Factors Influencing Long-Term Profitability
Beyond internal finances, external economic conditions significantly impact a company's ability to sustain its net income:
- Market Position & Competitive Advantage: Firms with strong brand recognition or unique offerings are better positioned for ongoing revenue streams.
- Revenue Diversification: Relying on multiple sources reduces vulnerability; if one segment underperforms, others can offset losses.
- Regulatory Environment Compliance: Adherence to laws minimizes legal risks and potential penalties that could erode profits.
Monitoring these factors provides insight into how well-positioned a company is within its industry landscape for enduring success.
The Role of Environmental Responsibility in Financial Sustainability
Environmental considerations are increasingly integral when assessing long-term profitability. Companies investing in green initiatives—such as renewable energy adoption or waste reduction—can lower operational costs while enhancing reputation among eco-conscious consumers.
Supply chain management also plays a crucial role; environmentally responsible sourcing mitigates risks related to resource depletion or regulatory sanctions due to unsustainable practices. Incorporating sustainability into core strategies not only benefits society but also supports stable profit generation by reducing exposure to environmental liabilities.
Recent Developments Impacting Net Income Sustainability
Recent corporate reports highlight contrasting scenarios illustrating the importance of sustainability:
In early 2025, Check Point Software Technologies showcased robust financial results exceeding expectations during Q1 2025[1]. Their strong earnings reflect effective management strategies aligned with both growth objectives and sustainability principles.
Conversely, Everest Group experienced challenges during the same period[2], reporting an increased combined ratio (102.7%), signaling potential strain on their profitability margins which could threaten future earnings stability if trends persist.
These examples underscore how current performance metrics serve as vital indicators when evaluating long-term viability — emphasizing the need for continuous monitoring beyond surface-level figures.
Risks That Threaten Net Income Longevity
Several risks can undermine efforts toward maintaining sustainable profits:
Financial Distress from High Debt Levels: Excessive borrowing hampers flexibility; interest obligations may divert funds from growth initiatives.
Regulatory Penalties & Non-compliance: Failure to meet environmental standards exposes firms to fines that directly reduce profit margins.
Environmental & Reputational Risks: Environmental damage incidents can lead not only legal consequences but also loss of customer trust impacting sales longevity.
Proactively managing these risks through strategic planning enhances resilience against unforeseen disruptions affecting long-term earnings stability.
Practical Strategies for Evaluating Net Income Sustainability
To accurately assess whether a company's profits are sustainable over time:
- Analyze historical financial statements focusing on profit consistency and cash flow patterns.
- Review industry position—market share data—and diversification strategies employed by the firm.
- Examine corporate social responsibility (CSR) reports highlighting green initiatives and supply chain ethics.
- Monitor regulatory compliance records alongside any penalties incurred historically.
- Stay updated on macroeconomic trends influencing sector-specific demand cycles or resource availability.
Combining quantitative data with qualitative insights offers a comprehensive view essential for informed decision-making regarding investment or strategic planning.
Keywords:sustainable net income | financial health | economic sustainability | environmental impact | cash flow analysis | risk assessment | corporate responsibility | long-term profitability


JCUSER-F1IIaxXA
2025-05-19 17:00
How to evaluate the sustainability of net income?
How to Evaluate the Sustainability of Net Income
Understanding whether a company's net income is sustainable is essential for investors, analysts, and business leaders aiming to gauge long-term financial health. Sustainable net income indicates that a company can maintain its profitability over time without depleting resources or risking environmental and social responsibilities. This article explores key factors, recent trends, and practical methods to assess the sustainability of net income effectively.
What Does Sustainability in Net Income Mean?
Sustainability in net income refers to a company's ability to generate consistent profits over an extended period while balancing economic viability with environmental stewardship and social responsibility. Unlike short-term earnings spikes driven by one-off events or market anomalies, sustainable net income reflects underlying operational strength and strategic resilience.
Achieving this balance involves evaluating not just financial metrics but also how environmental practices and societal impacts influence long-term performance. Investors increasingly prioritize companies that demonstrate responsible management of resources alongside steady profitability.
Key Financial Indicators for Assessing Sustainability
Financial health forms the foundation of sustainable net income. Several indicators help determine whether a company's profits are likely to persist:
- Profitability Trends: Consistent or growing profit margins suggest stable operations capable of weathering market fluctuations.
- Cash Flow Stability: Positive cash flow ensures ongoing liquidity necessary for investments, debt repayment, and operational needs.
- Debt Levels: Maintaining manageable debt ratios prevents financial distress; excessive leverage can threaten future earnings stability.
Regular analysis of these metrics helps identify companies with resilient financial structures capable of supporting sustained profitability.
Economic Factors Influencing Long-Term Profitability
Beyond internal finances, external economic conditions significantly impact a company's ability to sustain its net income:
- Market Position & Competitive Advantage: Firms with strong brand recognition or unique offerings are better positioned for ongoing revenue streams.
- Revenue Diversification: Relying on multiple sources reduces vulnerability; if one segment underperforms, others can offset losses.
- Regulatory Environment Compliance: Adherence to laws minimizes legal risks and potential penalties that could erode profits.
Monitoring these factors provides insight into how well-positioned a company is within its industry landscape for enduring success.
The Role of Environmental Responsibility in Financial Sustainability
Environmental considerations are increasingly integral when assessing long-term profitability. Companies investing in green initiatives—such as renewable energy adoption or waste reduction—can lower operational costs while enhancing reputation among eco-conscious consumers.
Supply chain management also plays a crucial role; environmentally responsible sourcing mitigates risks related to resource depletion or regulatory sanctions due to unsustainable practices. Incorporating sustainability into core strategies not only benefits society but also supports stable profit generation by reducing exposure to environmental liabilities.
Recent Developments Impacting Net Income Sustainability
Recent corporate reports highlight contrasting scenarios illustrating the importance of sustainability:
In early 2025, Check Point Software Technologies showcased robust financial results exceeding expectations during Q1 2025[1]. Their strong earnings reflect effective management strategies aligned with both growth objectives and sustainability principles.
Conversely, Everest Group experienced challenges during the same period[2], reporting an increased combined ratio (102.7%), signaling potential strain on their profitability margins which could threaten future earnings stability if trends persist.
These examples underscore how current performance metrics serve as vital indicators when evaluating long-term viability — emphasizing the need for continuous monitoring beyond surface-level figures.
Risks That Threaten Net Income Longevity
Several risks can undermine efforts toward maintaining sustainable profits:
Financial Distress from High Debt Levels: Excessive borrowing hampers flexibility; interest obligations may divert funds from growth initiatives.
Regulatory Penalties & Non-compliance: Failure to meet environmental standards exposes firms to fines that directly reduce profit margins.
Environmental & Reputational Risks: Environmental damage incidents can lead not only legal consequences but also loss of customer trust impacting sales longevity.
Proactively managing these risks through strategic planning enhances resilience against unforeseen disruptions affecting long-term earnings stability.
Practical Strategies for Evaluating Net Income Sustainability
To accurately assess whether a company's profits are sustainable over time:
- Analyze historical financial statements focusing on profit consistency and cash flow patterns.
- Review industry position—market share data—and diversification strategies employed by the firm.
- Examine corporate social responsibility (CSR) reports highlighting green initiatives and supply chain ethics.
- Monitor regulatory compliance records alongside any penalties incurred historically.
- Stay updated on macroeconomic trends influencing sector-specific demand cycles or resource availability.
Combining quantitative data with qualitative insights offers a comprehensive view essential for informed decision-making regarding investment or strategic planning.
Keywords:sustainable net income | financial health | economic sustainability | environmental impact | cash flow analysis | risk assessment | corporate responsibility | long-term profitability
Disclaimer:Contains third-party content. Not financial advice.
See Terms and Conditions.
Chainlink is gaining momentum with strong whale activity and bullish technical patterns positioning LINK for significant growth in 2025. Here's what investors need to know about the price outlook:
💰 Current Market Position:
-
Current Price: ~$24.32 (13.49% daily gain)
Market Cap: $16.04 billion (Ranked #11)
24h Volume: $2.58B (+120.68%)
30-day Rally: +36% gains
🎯 2025 Price Predictions Overview:
1️⃣ Short-term Targets (August 2025): $25-$28 range with potential $30 peak
2️⃣ Conservative Forecasts: $22-$28 range by major analysts
3️⃣ Bullish Scenarios: $32-$40 targets for late 2025
4️⃣ Aggressive Predictions: VirtualBacon forecasts $100 by end-2025
🚀 Key Growth Drivers:
-
Whale Accumulation: Transactions above $100K at multi-month highs
Technical Breakout: Clear resistance break above $24.50 targeting $26-$32
Real-World Assets (RWA): Positioned for $10 trillion tokenized asset market by 2030
Strategic Partnerships: SWIFT, Google Cloud, and Bitcoin DeFi integrations
Cross-Chain Expansion: 14 new integrations across 10 blockchain platforms
🔍 Technical Analysis:
-
Immediate Resistance: $24.50-$26.50 zone
Support Levels: $22.50 (near-term), $20.03 (SMA 20)
RSI: Around 72 (overbought but strong momentum)
MACD: Bullish crossover confirms buyer confidence
📊 Long-term Outlook (2026-2030):
-
2026: $26-$33 range expected
2027-2028: Potential new ATH around $54-$66
2030: Forecasts range from $48-$110 (avg ~$80-$98)
⚠️ Risk Factors:
-
Short-term consolidation possible near overbought levels
Market correlation with broader crypto sentiment
Competition in oracle space
Regulatory developments affecting DeFi sector
💡 Investment Thesis: Chainlink's dominance in oracle services, expanding into RWA tokenization, and growing institutional adoption support bullish long-term outlook. The $24-$32 range appears realistic for 2025, with potential for higher targets if bull market conditions persist.
Most analysts agree LINK's fundamental value proposition in connecting blockchain to real-world data makes it a strong candidate for sustained growth as crypto adoption accelerates.
Read detailed technical analysis and expert forecasts: 👇 https://blog.jucoin.com/chainlink-link-token-price-potential-2025/
#Chainlink #LINK #Oracle #DeFi #RWA



JU Blog
2025-08-20 10:44
🔗 Chainlink (LINK) Eyes $32 Target by Late 2025 as Whale Accumulation Surges
Disclaimer:Contains third-party content. Not financial advice.
See Terms and Conditions.
The crypto market experienced significant losses in August 2025, with most major tokens posting notable declines. Here's what's driving the downturn and what investors need to know:
💰 Major Losses Overview:
-
Bitcoin (BTC): -8% to $113,562
Ethereum (ETH): -5.2% to $4,166
Cardano (ADA): -6.3% to $0.8526
XRP: -3.77% to $2.89
Dogecoin (DOGE): -2.21% to $0.2127
🎯 Key Market Drivers:
1️⃣ Jackson Hole Uncertainty: Fed rate cut expectations dropped from 98% to 15%, dampening institutional risk appetite
2️⃣ ETF Volatility: Ethereum ETFs saw $196.6 million outflows after a record $2.8 billion inflow the previous week
3️⃣ Regulatory Delays: Stalled altcoin ETF approvals and unclear stablecoin legislation adding market anxiety
4️⃣ Technical Liquidations: Over $1.2 billion in long positions liquidated as Bitcoin hit resistance at $124,000
🚨 Security Concerns:
-
AI-powered wallet drainers targeting developers
$2.17 billion in crypto hacks recorded in 2025
GreedyBear exploit affecting 150+ fake browser extensions
🏆 Biggest Altcoin Losers (24h):
-
Gari Network (GARI): -23.15%
Useless Coin (USELESS): -17.98%
League of Kingdoms Arena (LOKA): -10.03%
Livepeer (LPT): -9.90%
💡 What's Next:
-
All eyes on Powell's Jackson Hole speech for Fed policy signals
ETF flows remain key indicator for short-term price action
Most analysts view this as temporary correction, not trend reversal
Long-term fundamentals remain intact despite current volatility
The market correction appears driven by macro uncertainty rather than fundamental crypto weaknesses. Investors are consolidating positions ahead of key policy announcements.
Read the complete market analysis with detailed charts and expert insights: 👇 https://blog.jucoin.com/crypto-losses-recent-key-market-declines-explained/
#CryptoLosses #Bitcoin #Ethereum



JU Blog
2025-08-20 10:37
📉 Crypto Market Takes Sharp Hit: Major Tokens Down 3-8% This Week
Disclaimer:Contains third-party content. Not financial advice.
See Terms and Conditions.
🔐 Les banques ne pourront plus couper l’accès aux clients légitimes, y compris dans les **actifs numériques**.
#CryptoPolicy #DigitalAssets #Web3




Carmelita
2025-08-07 20:18
🇺🇸 Trump signe un décret interdisant le “debanking politique”.
Disclaimer:Contains third-party content. Not financial advice.
See Terms and Conditions.
InterLink introduces an innovative dual-token architecture that separates compliance from participation, creating a sustainable ecosystem where institutions and individuals thrive together. Here's the breakthrough approach:
🏛️ $ITL Token (Compliance Layer):
-
1 billion total supply for institutions and ecosystem funds
Staking required for "Human Layer" access rights
Reputation-based validation prevents malicious nodes
Institutional holders earn transaction fee shares
👥 $ITLG Token (Incentive Layer):
-
10 billion supply: 80% for human nodes, 20% for governance
Earned through facial recognition verification + referrals
Daily mining rewards based on activity and contributions
Powers DAO governance with 1 token = 1 vote
🚀 Key Innovation - Human Node Validation:
-
Facial recognition prevents bot farming
Social referral system ensures authentic users
Activity scoring rewards genuine participation
Avoids PoW/PoS centralization risks
⚖️ DAO Governance Features:
-
Linear voting prevents whale domination
Smart contract auto-execution
Full on-chain transparency
Community-driven protocol evolution
🌍 Real-World Applications:
-
Humanitarian Aid: Direct peer-to-peer payments to disaster victims
Financial Inclusion: Digital payments for unbanked populations
Data Monetization: Secure data licensing for $ITLG rewards
Social Governance: Community polls and collaborative projects
📈 2025 Roadmap:
-
50+ country expansion with regional validator nodes
Cross-chain bridges to Ethereum, Avalanche, Cosmos
Human Layer SDK for developers
InterLink Rating (IR) system for enhanced autonomy
💡 Why It Matters: This dual-token approach solves the age-old problem of balancing institutional compliance with genuine user participation. While institutions provide stability through $ITL staking, real users drive network vitality through $ITLG incentives - creating the first truly human-centered DeFi ecosystem.
The future of crypto isn't just about code - it's about people. InterLink proves that sustainable tokenomics must center on human validation and authentic participation.
Read the complete tokenomics breakdown: 👇 https://blog.jucoin.com/interlink-dual-tokenomics/
#InterLink #DualToken #DeFi #DAO #Tokenomics



JU Blog
2025-08-06 10:45
🔗 InterLink's Revolutionary Dual-Token Model: Human-Centered DeFi!
Disclaimer:Contains third-party content. Not financial advice.
See Terms and Conditions.
What is Anti-Money Laundering (AML)?
Anti-Money Laundering (AML) encompasses a set of laws, regulations, and procedures designed to prevent the process of disguising illegally obtained funds as legitimate income. Money laundering typically involves three key stages: placement, layering, and integration. During placement, illicit cash is introduced into the financial system—often through banks or other financial institutions. Layering involves complex transactions that obscure the origin of the money by moving it across various accounts or jurisdictions. Finally, in the integration stage, the laundered money re-enters the economy as seemingly legitimate funds.
The primary goal of AML measures is to detect and deter these activities before they can cause widespread harm to financial systems and economies. Criminal enterprises involved in activities like drug trafficking, terrorism financing, human trafficking, or corruption rely heavily on money laundering to legitimize their profits. Therefore, effective AML policies are essential for maintaining transparency within financial markets and safeguarding against criminal exploitation.
Regulatory Frameworks for AML
Internationally recognized standards shape AML efforts worldwide. The Financial Action Task Force (FATF), established in 1989 during a G7 summit, plays a pivotal role by setting global guidelines aimed at combating money laundering and terrorist financing. Countries adopt these standards into their national laws to create cohesive enforcement mechanisms.
In addition to FATF's recommendations, regional bodies such as the European Union have enacted directives like AMLD4 (2016) and AMLD6 (2023), which strengthen due diligence requirements and expand reporting obligations for financial institutions operating within their jurisdictions. In countries like the United States, agencies such as FinCEN enforce compliance with these regulations through monitoring reports from banks and other entities.
Financial Institutions' Responsibilities
Banks are at the forefront of implementing AML measures because they serve as primary gateways for illicit funds entering or leaving legal channels. Their responsibilities include verifying customer identities through Know Your Customer (KYC) procedures—collecting information about clients’ backgrounds—and continuously monitoring transactions for suspicious activity patterns.
When unusual transactions are detected—such as large cash deposits inconsistent with a customer’s profile—they must be reported promptly via Suspicious Activity Reports (SARs). These reports help authorities investigate potential cases of money laundering or related crimes before significant damage occurs.
Cryptocurrency Exchanges: New Frontiers in AML
The rise of cryptocurrencies has introduced both opportunities and challenges in anti-money laundering efforts. Digital assets offer anonymity features that can facilitate illegal activities if not properly regulated; hence regulators worldwide are developing specific guidelines tailored for crypto exchanges.
For example:
- The U.S Securities and Exchange Commission (SEC) has issued directives requiring cryptocurrency platforms to implement robust KYC/AML protocols.
- European regulators have also increased scrutiny over digital asset service providers under existing anti-money laundering frameworks.
Technological Innovations Enhancing Compliance
Advancements in technology play an increasingly vital role in strengthening AML compliance programs:
- Artificial Intelligence (AI) algorithms analyze transaction data rapidly to identify suspicious behavior.
- Machine Learning models adapt over time based on new data patterns.
- Automated reporting tools streamline submission processes for regulatory authorities.These innovations enable institutions not only to improve detection accuracy but also reduce operational costs associated with manual oversight.
Recent Developments Shaping Future Policies
Regulatory landscapes continue evolving amid technological progress:
- In 2022, a prominent cryptocurrency exchange faced a $50 million fine from U.S authorities due to violations related to inadequate KYC/AML practices.
- The European Union’s Sixth Anti-Money Laundering Directive (AMLD6), implemented in 2023, expanded scope by including virtual asset service providers under stricter compliance requirements.Additionally,the ongoing debate around stablecoins highlights concerns regarding their potential misuse for cross-border money laundering schemes—a topic gaining attention among policymakers like Senator Elizabeth Warren who advocate for tighter safeguards against illicit finance flows involving digital assets.
Impacts of Non-Compliance
Failure by financial institutions or crypto platforms to adhere strictly to AML regulations can lead not only to hefty fines but also severe reputational damage that may threaten long-term viability:
- Fines reaching hundreds of millions USD
- Loss of licensing privileges
- Increased scrutiny from regulatorsMoreover,non-compliance undermines public trust in financial systems overall—a critical factor considering how interconnected global markets have become today.
Historical Milestones & Ongoing Challenges
Since its inception during G7 meetings in 1970—and subsequent establishment of FATF—the fight against money laundering has seen significant milestones:
- Introduction of international standards guiding national policies
- Implementation phases across different regions
- Adoption of advanced technological solutionsDespite progress made over decades,challenges persist due mainly to evolving methods employed by criminals who exploit emerging technologies like cryptocurrencies or decentralized finance platforms—necessitating continuous updates on regulatory frameworks alongside innovative detection tools.
Why Robust Anti-Money Laundering Measures Matter?
Effective AML policies protect economies from being exploited by criminal enterprises while fostering transparency within global finance networks. They help prevent funding terrorism campaigns that threaten security worldwide; safeguard consumer interests; uphold market integrity; promote fair competition among businesses; ensure compliance with international obligations—all crucial components underpinning stable economic growth.
Key Takeaways:
Money laundering involves three stages: placement into banks/accounts → layering through complex transactions → integration into legitimate economy.
International bodies such as FATF set standards adopted globally via national legislation
Financial institutions must verify identities using KYC processes & monitor transactions actively
Emerging technologies like AI enhance detection capabilities
Cryptocurrency exchanges face increasing regulation amid concerns over anonymity features facilitating illegal activities
By understanding these core aspects—and recognizing ongoing developments—you can better appreciate why strong anti-money laundering measures remain vital components within modern financial regulation frameworks.
Semantic & LSI Keywords:
Money Laundering Prevention | Financial Crime Detection | Cryptocurrency Regulation | KYC Procedures | Suspicious Activity Reporting | Digital Asset Compliance | Global Regulatory Standards | Fintech & Anti-Money Laundering | Blockchain Transparency Measures


JCUSER-F1IIaxXA
2025-05-15 01:43
What is Anti-Money Laundering (AML)?
What is Anti-Money Laundering (AML)?
Anti-Money Laundering (AML) encompasses a set of laws, regulations, and procedures designed to prevent the process of disguising illegally obtained funds as legitimate income. Money laundering typically involves three key stages: placement, layering, and integration. During placement, illicit cash is introduced into the financial system—often through banks or other financial institutions. Layering involves complex transactions that obscure the origin of the money by moving it across various accounts or jurisdictions. Finally, in the integration stage, the laundered money re-enters the economy as seemingly legitimate funds.
The primary goal of AML measures is to detect and deter these activities before they can cause widespread harm to financial systems and economies. Criminal enterprises involved in activities like drug trafficking, terrorism financing, human trafficking, or corruption rely heavily on money laundering to legitimize their profits. Therefore, effective AML policies are essential for maintaining transparency within financial markets and safeguarding against criminal exploitation.
Regulatory Frameworks for AML
Internationally recognized standards shape AML efforts worldwide. The Financial Action Task Force (FATF), established in 1989 during a G7 summit, plays a pivotal role by setting global guidelines aimed at combating money laundering and terrorist financing. Countries adopt these standards into their national laws to create cohesive enforcement mechanisms.
In addition to FATF's recommendations, regional bodies such as the European Union have enacted directives like AMLD4 (2016) and AMLD6 (2023), which strengthen due diligence requirements and expand reporting obligations for financial institutions operating within their jurisdictions. In countries like the United States, agencies such as FinCEN enforce compliance with these regulations through monitoring reports from banks and other entities.
Financial Institutions' Responsibilities
Banks are at the forefront of implementing AML measures because they serve as primary gateways for illicit funds entering or leaving legal channels. Their responsibilities include verifying customer identities through Know Your Customer (KYC) procedures—collecting information about clients’ backgrounds—and continuously monitoring transactions for suspicious activity patterns.
When unusual transactions are detected—such as large cash deposits inconsistent with a customer’s profile—they must be reported promptly via Suspicious Activity Reports (SARs). These reports help authorities investigate potential cases of money laundering or related crimes before significant damage occurs.
Cryptocurrency Exchanges: New Frontiers in AML
The rise of cryptocurrencies has introduced both opportunities and challenges in anti-money laundering efforts. Digital assets offer anonymity features that can facilitate illegal activities if not properly regulated; hence regulators worldwide are developing specific guidelines tailored for crypto exchanges.
For example:
- The U.S Securities and Exchange Commission (SEC) has issued directives requiring cryptocurrency platforms to implement robust KYC/AML protocols.
- European regulators have also increased scrutiny over digital asset service providers under existing anti-money laundering frameworks.
Technological Innovations Enhancing Compliance
Advancements in technology play an increasingly vital role in strengthening AML compliance programs:
- Artificial Intelligence (AI) algorithms analyze transaction data rapidly to identify suspicious behavior.
- Machine Learning models adapt over time based on new data patterns.
- Automated reporting tools streamline submission processes for regulatory authorities.These innovations enable institutions not only to improve detection accuracy but also reduce operational costs associated with manual oversight.
Recent Developments Shaping Future Policies
Regulatory landscapes continue evolving amid technological progress:
- In 2022, a prominent cryptocurrency exchange faced a $50 million fine from U.S authorities due to violations related to inadequate KYC/AML practices.
- The European Union’s Sixth Anti-Money Laundering Directive (AMLD6), implemented in 2023, expanded scope by including virtual asset service providers under stricter compliance requirements.Additionally,the ongoing debate around stablecoins highlights concerns regarding their potential misuse for cross-border money laundering schemes—a topic gaining attention among policymakers like Senator Elizabeth Warren who advocate for tighter safeguards against illicit finance flows involving digital assets.
Impacts of Non-Compliance
Failure by financial institutions or crypto platforms to adhere strictly to AML regulations can lead not only to hefty fines but also severe reputational damage that may threaten long-term viability:
- Fines reaching hundreds of millions USD
- Loss of licensing privileges
- Increased scrutiny from regulatorsMoreover,non-compliance undermines public trust in financial systems overall—a critical factor considering how interconnected global markets have become today.
Historical Milestones & Ongoing Challenges
Since its inception during G7 meetings in 1970—and subsequent establishment of FATF—the fight against money laundering has seen significant milestones:
- Introduction of international standards guiding national policies
- Implementation phases across different regions
- Adoption of advanced technological solutionsDespite progress made over decades,challenges persist due mainly to evolving methods employed by criminals who exploit emerging technologies like cryptocurrencies or decentralized finance platforms—necessitating continuous updates on regulatory frameworks alongside innovative detection tools.
Why Robust Anti-Money Laundering Measures Matter?
Effective AML policies protect economies from being exploited by criminal enterprises while fostering transparency within global finance networks. They help prevent funding terrorism campaigns that threaten security worldwide; safeguard consumer interests; uphold market integrity; promote fair competition among businesses; ensure compliance with international obligations—all crucial components underpinning stable economic growth.
Key Takeaways:
Money laundering involves three stages: placement into banks/accounts → layering through complex transactions → integration into legitimate economy.
International bodies such as FATF set standards adopted globally via national legislation
Financial institutions must verify identities using KYC processes & monitor transactions actively
Emerging technologies like AI enhance detection capabilities
Cryptocurrency exchanges face increasing regulation amid concerns over anonymity features facilitating illegal activities
By understanding these core aspects—and recognizing ongoing developments—you can better appreciate why strong anti-money laundering measures remain vital components within modern financial regulation frameworks.
Semantic & LSI Keywords:
Money Laundering Prevention | Financial Crime Detection | Cryptocurrency Regulation | KYC Procedures | Suspicious Activity Reporting | Digital Asset Compliance | Global Regulatory Standards | Fintech & Anti-Money Laundering | Blockchain Transparency Measures
Disclaimer:Contains third-party content. Not financial advice.
See Terms and Conditions.
🚀 The Future of Bitcoin is closer than you think!
By 2030, Bitcoin could transform the financial world as we know it. Whether you’re a seasoned HODLer or just starting your crypto journey, the question is… how many will YOU own?


JuCoin Media
2025-08-13 14:49
The Future of Bitcoin 🚀 – How Many Will You Own by 2030?
Disclaimer:Contains third-party content. Not financial advice.
See Terms and Conditions.
✅ Just 4 simple steps to start your reward journey:
1️⃣ Open JuCoin app, go to “Discover”
2️⃣ Find JU Node & tap to enter
3️⃣ In JU Node page, select “Buy”
4️⃣ Complete payment with USDT or AIC to start receiving $JU daily
💡 Pro Tip: Higher Hashrate → Higher Rewards! 🔥
#JuCoin #JucoinVietnam #JUHashRate #Crypto #DeFi #Web3 #Blockchain


Lee Jucoin
2025-08-19 06:41
🚀 Want your $JU to keep growing? Start with JU Hashrate today! 🌟
Disclaimer:Contains third-party content. Not financial advice.
See Terms and Conditions.
Miran est connu pour son soutien affiché à $BTC, avec son désormais culte : *“#Bitcoin fixes this”*.
Un défenseur du Web3 à la table du FOMC ? Le narratif devient réalité.
#Bitcoin #CryptoPolicy #BTC

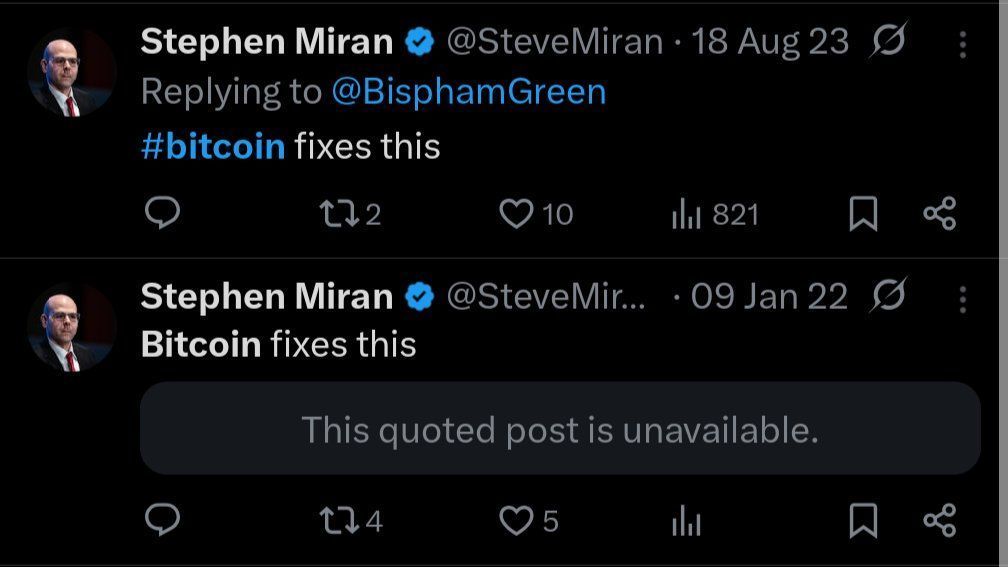


Carmelita
2025-08-07 21:15
🚨 Trump propose Stephen Miran, économiste pro-Bitcoin, pour le poste de gouverneur à la Fed.
Disclaimer:Contains third-party content. Not financial advice.
See Terms and Conditions.
How to Apply Forensic Analysis to Detect Fraud
Fraudulent activities pose a significant threat to individuals, businesses, and financial institutions worldwide. As fraud schemes become more sophisticated—especially with the rise of digital assets like cryptocurrencies—traditional detection methods often fall short. Forensic analysis has emerged as a vital approach in uncovering and preventing these crimes. This article explores how forensic analysis can be effectively applied to detect fraud, emphasizing practical techniques, recent technological advancements, and best practices.
Understanding the Role of Forensic Analysis in Fraud Detection
Forensic analysis involves applying scientific principles and investigative techniques to examine evidence related to fraudulent activities. Its primary goal is to verify the authenticity of transactions, documents, or digital footprints that may indicate deception or illegal activity. In financial contexts, forensic analysts scrutinize complex transaction data and digital artifacts to identify anomalies that suggest fraud.
This process is crucial not only for criminal investigations but also for corporate compliance efforts aimed at preventing internal misconduct or external scams. Given the increasing complexity of financial transactions—particularly with online banking, mobile payments, and cryptocurrencies—advanced forensic methods are essential for effective detection.
Key Techniques Used in Forensic Fraud Investigation
Applying forensic analysis requires a combination of specialized tools and methodologies tailored to different types of evidence:
Digital Forensics
Digital forensics involves analyzing electronic devices such as computers, smartphones, servers, emails, text messages, and online activity logs. By recovering deleted files or tracing IP addresses involved in suspicious transactions, investigators can build a timeline of events that reveal fraudulent schemes.
Data Analysis & Machine Learning
Data analytics leverages statistical models and machine learning algorithms capable of sifting through vast datasets quickly. These tools help identify patterns or outliers—such as unusual transaction volumes or irregular account behaviors—that may signal fraudulent activity.
Document Examination
Analyzing physical or digital documents is critical when verifying paperwork associated with transactions. Experts look for inconsistencies like misspellings, formatting errors (anachronisms), altered signatures—or other signs indicating forgery—that could point toward document fraud.
Applying Forensic Techniques Step-by-Step
To effectively detect fraud using forensic analysis:
- Identify Suspicious Activity: Start by monitoring transactional data for anomalies such as unexpected large transfers or irregular access patterns.
- Collect Evidence: Gather relevant digital artifacts (emails; transaction logs; metadata) while maintaining chain-of-custody protocols.
- Analyze Digital Footprints: Use specialized software like EnCase or FTK to recover deleted files; trace communication channels involved.
- Perform Data Analytics: Deploy machine learning models trained on historical data sets representing normal versus fraudulent behavior.
- Examine Documents Thoroughly: Cross-check documentation against known standards; look for discrepancies indicating tampering.
- Correlate Findings: Integrate insights from various sources—digital traces plus document reviews—to form a comprehensive picture.
- Report & Act: Summarize findings clearly; collaborate with legal teams if necessary before taking corrective actions.
Recent Technological Advancements Enhancing Fraud Detection
The landscape of forensic investigation continues evolving rapidly thanks to innovations like blockchain technology and artificial intelligence (AI). Blockchain’s transparent ledger system allows investigators to trace cryptocurrency transactions more accurately than ever before—a significant advantage given the rise in crypto-related scams such as phishing attacks or Ponzi schemes.
AI-powered tools now assist analysts by automatically flagging suspicious patterns across massive datasets without manual intervention — improving both speed and accuracy in detecting complex fraud networks.
Additionally,, companies like Google have integrated enhanced security features into their platforms (e.g., Android 16) designed specifically to combat scams involving cryptocurrencies by alerting users about potential threats proactively.
Challenges Faced When Applying Forensic Analysis
Despite technological progress,, several hurdles remain:
- The sheer volume of digital data can overwhelm traditional investigative processes unless supported by advanced analytics tools.
- Cybercriminals continually adapt their tactics—for example,, using encrypted messaging apps—which complicates evidence collection.
- Ensuring compliance with privacy laws during investigations requires careful handling so as not infringe on individual rights while gathering sufficient evidence.
- The need for highly trained professionals who stay updated on emerging technologies adds an ongoing resource challenge within organizations seeking effective detection capabilities.
Best Practices for Effective Fraud Detection Using Forensics
To maximize success rates when applying forensic analysis:
- Maintain meticulous documentation throughout investigations—including chain-of-custody records—to ensure admissibility if legal proceedings follow.
- Invest in continuous training programs so analysts stay current with latest software updates,, cyber threats,, regulatory changes—and emerging scam tactics.
- Use layered approaches combining multiple techniques: e.g., initial pattern recognition via AI followed by detailed manual review where needed..
- Foster collaboration between IT teams,, legal advisors,, auditors—and external experts when necessary—to ensure comprehensive coverage..
By integrating these practices into your organization’s risk management framework,,, you enhance your ability not onlyto detect existing fraud but also prevent future incidents through proactive monitoring strategies..
Real-Life Examples Demonstrating Effective Application
One notable case involved authorities uncovering fake art sales linked via forged documents analyzed through forensic document examination techniques.. A Miami dealer was caught selling counterfeit Warhol artworks after investigators identified inconsistencies within paperwork—a classic example illustrating how thorough document scrutiny can expose deception even amidst sophisticated schemes..
Similarly,,, cryptocurrency exchanges increasingly rely on blockchain analytics software such as Chainalysis—which tracks illicit crypto flows—to identify scammers operating across borders.. These real-world applications highlight how combining traditional investigative skills with cutting-edge technology yields tangible results against diverse formsof financial crime..
Applying forensic analysis effectively requires understanding its core principles—from examining electronic footprintsand scrutinizing documents,to leveraging modern tech innovations—all aimed at exposing hidden fraudulent activities swiftlyand accurately.. As financial landscapes evolve—with new assets emerging—the importanceof staying ahead through continuous learningand adopting best practices cannot be overstated.. Whether dealingwith conventional financial scamsor navigating complex crypto schemes,—a strategic approach rootedin scientific investigation remains your strongest assetin safeguarding assetsand maintaining trustworthiness within your organization.or community


kai
2025-05-19 17:16
How to apply forensic analysis to detect fraud?
How to Apply Forensic Analysis to Detect Fraud
Fraudulent activities pose a significant threat to individuals, businesses, and financial institutions worldwide. As fraud schemes become more sophisticated—especially with the rise of digital assets like cryptocurrencies—traditional detection methods often fall short. Forensic analysis has emerged as a vital approach in uncovering and preventing these crimes. This article explores how forensic analysis can be effectively applied to detect fraud, emphasizing practical techniques, recent technological advancements, and best practices.
Understanding the Role of Forensic Analysis in Fraud Detection
Forensic analysis involves applying scientific principles and investigative techniques to examine evidence related to fraudulent activities. Its primary goal is to verify the authenticity of transactions, documents, or digital footprints that may indicate deception or illegal activity. In financial contexts, forensic analysts scrutinize complex transaction data and digital artifacts to identify anomalies that suggest fraud.
This process is crucial not only for criminal investigations but also for corporate compliance efforts aimed at preventing internal misconduct or external scams. Given the increasing complexity of financial transactions—particularly with online banking, mobile payments, and cryptocurrencies—advanced forensic methods are essential for effective detection.
Key Techniques Used in Forensic Fraud Investigation
Applying forensic analysis requires a combination of specialized tools and methodologies tailored to different types of evidence:
Digital Forensics
Digital forensics involves analyzing electronic devices such as computers, smartphones, servers, emails, text messages, and online activity logs. By recovering deleted files or tracing IP addresses involved in suspicious transactions, investigators can build a timeline of events that reveal fraudulent schemes.
Data Analysis & Machine Learning
Data analytics leverages statistical models and machine learning algorithms capable of sifting through vast datasets quickly. These tools help identify patterns or outliers—such as unusual transaction volumes or irregular account behaviors—that may signal fraudulent activity.
Document Examination
Analyzing physical or digital documents is critical when verifying paperwork associated with transactions. Experts look for inconsistencies like misspellings, formatting errors (anachronisms), altered signatures—or other signs indicating forgery—that could point toward document fraud.
Applying Forensic Techniques Step-by-Step
To effectively detect fraud using forensic analysis:
- Identify Suspicious Activity: Start by monitoring transactional data for anomalies such as unexpected large transfers or irregular access patterns.
- Collect Evidence: Gather relevant digital artifacts (emails; transaction logs; metadata) while maintaining chain-of-custody protocols.
- Analyze Digital Footprints: Use specialized software like EnCase or FTK to recover deleted files; trace communication channels involved.
- Perform Data Analytics: Deploy machine learning models trained on historical data sets representing normal versus fraudulent behavior.
- Examine Documents Thoroughly: Cross-check documentation against known standards; look for discrepancies indicating tampering.
- Correlate Findings: Integrate insights from various sources—digital traces plus document reviews—to form a comprehensive picture.
- Report & Act: Summarize findings clearly; collaborate with legal teams if necessary before taking corrective actions.
Recent Technological Advancements Enhancing Fraud Detection
The landscape of forensic investigation continues evolving rapidly thanks to innovations like blockchain technology and artificial intelligence (AI). Blockchain’s transparent ledger system allows investigators to trace cryptocurrency transactions more accurately than ever before—a significant advantage given the rise in crypto-related scams such as phishing attacks or Ponzi schemes.
AI-powered tools now assist analysts by automatically flagging suspicious patterns across massive datasets without manual intervention — improving both speed and accuracy in detecting complex fraud networks.
Additionally,, companies like Google have integrated enhanced security features into their platforms (e.g., Android 16) designed specifically to combat scams involving cryptocurrencies by alerting users about potential threats proactively.
Challenges Faced When Applying Forensic Analysis
Despite technological progress,, several hurdles remain:
- The sheer volume of digital data can overwhelm traditional investigative processes unless supported by advanced analytics tools.
- Cybercriminals continually adapt their tactics—for example,, using encrypted messaging apps—which complicates evidence collection.
- Ensuring compliance with privacy laws during investigations requires careful handling so as not infringe on individual rights while gathering sufficient evidence.
- The need for highly trained professionals who stay updated on emerging technologies adds an ongoing resource challenge within organizations seeking effective detection capabilities.
Best Practices for Effective Fraud Detection Using Forensics
To maximize success rates when applying forensic analysis:
- Maintain meticulous documentation throughout investigations—including chain-of-custody records—to ensure admissibility if legal proceedings follow.
- Invest in continuous training programs so analysts stay current with latest software updates,, cyber threats,, regulatory changes—and emerging scam tactics.
- Use layered approaches combining multiple techniques: e.g., initial pattern recognition via AI followed by detailed manual review where needed..
- Foster collaboration between IT teams,, legal advisors,, auditors—and external experts when necessary—to ensure comprehensive coverage..
By integrating these practices into your organization’s risk management framework,,, you enhance your ability not onlyto detect existing fraud but also prevent future incidents through proactive monitoring strategies..
Real-Life Examples Demonstrating Effective Application
One notable case involved authorities uncovering fake art sales linked via forged documents analyzed through forensic document examination techniques.. A Miami dealer was caught selling counterfeit Warhol artworks after investigators identified inconsistencies within paperwork—a classic example illustrating how thorough document scrutiny can expose deception even amidst sophisticated schemes..
Similarly,,, cryptocurrency exchanges increasingly rely on blockchain analytics software such as Chainalysis—which tracks illicit crypto flows—to identify scammers operating across borders.. These real-world applications highlight how combining traditional investigative skills with cutting-edge technology yields tangible results against diverse formsof financial crime..
Applying forensic analysis effectively requires understanding its core principles—from examining electronic footprintsand scrutinizing documents,to leveraging modern tech innovations—all aimed at exposing hidden fraudulent activities swiftlyand accurately.. As financial landscapes evolve—with new assets emerging—the importanceof staying ahead through continuous learningand adopting best practices cannot be overstated.. Whether dealingwith conventional financial scamsor navigating complex crypto schemes,—a strategic approach rootedin scientific investigation remains your strongest assetin safeguarding assetsand maintaining trustworthiness within your organization.or community
Disclaimer:Contains third-party content. Not financial advice.
See Terms and Conditions.
How Opening Range Defines Intraday Support and Resistance Levels
Understanding how to identify support and resistance levels is fundamental for successful intraday trading. One of the most effective tools traders use for this purpose is the opening range (OR). By analyzing the initial price action during the first few minutes of trading, traders can gain valuable insights into potential market direction and key levels that may influence future price movements. This article explores how opening range helps define intraday support and resistance, backed by recent developments and practical strategies.
What Is Opening Range in Intraday Trading?
The opening range refers to the high and low prices established during a specific initial period after a security's market opens—typically within the first 30 to 60 minutes of trading. During this window, traders observe how prices fluctuate before committing to larger positions. The highest price reached during this period marks one boundary, while the lowest sets another. These two points create a "range" that serves as a benchmark for subsequent trading activity.
This initial phase captures early market sentiment—whether buyers or sellers dominate—and provides clues about potential trends or consolidations throughout the day. Because markets often react strongly at open due to overnight news or economic releases, analyzing this early data offers an edge in predicting intraday support and resistance levels.
How Does Opening Range Help Identify Support & Resistance?
Support and resistance are critical concepts in technical analysis—they represent price levels where buying or selling pressure tends to halt or reverse trends. The opening range plays a pivotal role here because it establishes immediate reference points based on real-time market behavior.
- Support Level: If prices decline toward the lower boundary of the opening range but fail to break below it, that level may act as support—a floor preventing further declines.
- Resistance Level: Conversely, if prices rise toward the upper boundary but struggle to surpass it, that level can serve as resistance—a ceiling limiting upward movement.
When prices break above or below these boundaries with significant volume, it often signals a shift in momentum—either confirming continuation beyond these levels or indicating reversal opportunities.
For example:
- A breakout above the opening high suggests bullish strength; traders might see this as an entry point for long positions.
- A breakdown below the opening low could signal bearish sentiment; traders might consider shorting or exiting longs.
By monitoring whether prices respect these boundaries within their respective ranges—or break through them—traders can make more informed decisions about entry and exit points during active hours.
Practical Strategies Using Opening Range
Traders employ various strategies centered around opening range analysis:
Range Trading:
- Buy near support (opening low)
- Sell near resistance (opening high)
- Use tight stop-loss orders just outside these boundaries
Breakout Trading:
- Enter trades when price breaks above resistance or below support with increased volume
- Confirm breakout validity with other indicators like RSI or moving averages
Fade Strategy:
- Trade against false breakouts by betting on reversals when price quickly re-enters previous ranges
Adjusting Stops & Targets:
- Use openings' high/low as dynamic stop-loss points
- Set profit targets based on measured distance between open-range boundaries
These approaches help manage risk effectively while capitalizing on predictable intraday patterns derived from early market activity.
Recent Advances Enhancing Opening Range Analysis
Technological progress has significantly improved how traders utilize opening ranges:
- Modern trading platforms provide real-time data feeds enabling precise calculation of initial highs/lows.
- Algorithmic tools now automatically identify key breakout moments based on predefined criteria.
- Integration with other technical indicators such as Bollinger Bands, RSI (Relative Strength Index), MACD (Moving Average Convergence Divergence), enhances confirmation signals.
- Increased adoption in volatile markets like cryptocurrencies demonstrates its versatility; crypto's rapid moves make early-range analysis particularly valuable for quick decision-making.
Furthermore, machine learning models are being developed to analyze historical patterns related to open-range behavior across different assets—adding predictive power beyond traditional methods.
Risks & Limitations of Relying Solely on Opening Range
While powerful, relying exclusively on opening range analysis carries risks:
- Overdependence may lead traders astray if unexpected news causes sudden volatility outside established ranges.
- Market manipulation tactics such as "spoofing" can artificially influence perceived support/resistance levels at open.
- False breakouts are common; not all breaches result in sustained moves—requiring confirmation from additional indicators.
Therefore, it's crucial always to combine OR-based insights with broader technical frameworks—including trend analysis and volume studies—to improve accuracy while managing risk effectively.
Applying Support & Resistance Levels Derived from Opening Range
In practice:
- Observe initial trade activity closely during first hour after market opens.
- Mark highest (resistance) and lowest (support) points reached within this period.
- Watch for signs of breakout beyond these bounds — confirmed by increased volume — which could signal strong directional moves.
- Use these levels dynamically throughout your trading session—for setting stops/limits—and adapt quickly if new information emerges.
Final Thoughts: Enhancing Intraday Strategies With Opening Range Insights
The ability of closing-in-time data from an asset’s first few minutes offers invaluable guidance for defining intraday support/resistance zones through its establishing of key thresholds reflective of current market sentiment—not just historical averages but real-time reactions at open sessions enable more responsive decision-making processes than static chart patterns alone would permit.
By integrating modern technological tools alongside traditional technical principles—including careful validation via multiple indicators—you elevate your capacity not only to recognize potential turning points but also craft disciplined strategies aligned with evolving conditions—all essential elements underpinning sustainable success in active day-trading environments.


JCUSER-IC8sJL1q
2025-05-14 04:46
How can opening range define intraday support/resistance levels?
How Opening Range Defines Intraday Support and Resistance Levels
Understanding how to identify support and resistance levels is fundamental for successful intraday trading. One of the most effective tools traders use for this purpose is the opening range (OR). By analyzing the initial price action during the first few minutes of trading, traders can gain valuable insights into potential market direction and key levels that may influence future price movements. This article explores how opening range helps define intraday support and resistance, backed by recent developments and practical strategies.
What Is Opening Range in Intraday Trading?
The opening range refers to the high and low prices established during a specific initial period after a security's market opens—typically within the first 30 to 60 minutes of trading. During this window, traders observe how prices fluctuate before committing to larger positions. The highest price reached during this period marks one boundary, while the lowest sets another. These two points create a "range" that serves as a benchmark for subsequent trading activity.
This initial phase captures early market sentiment—whether buyers or sellers dominate—and provides clues about potential trends or consolidations throughout the day. Because markets often react strongly at open due to overnight news or economic releases, analyzing this early data offers an edge in predicting intraday support and resistance levels.
How Does Opening Range Help Identify Support & Resistance?
Support and resistance are critical concepts in technical analysis—they represent price levels where buying or selling pressure tends to halt or reverse trends. The opening range plays a pivotal role here because it establishes immediate reference points based on real-time market behavior.
- Support Level: If prices decline toward the lower boundary of the opening range but fail to break below it, that level may act as support—a floor preventing further declines.
- Resistance Level: Conversely, if prices rise toward the upper boundary but struggle to surpass it, that level can serve as resistance—a ceiling limiting upward movement.
When prices break above or below these boundaries with significant volume, it often signals a shift in momentum—either confirming continuation beyond these levels or indicating reversal opportunities.
For example:
- A breakout above the opening high suggests bullish strength; traders might see this as an entry point for long positions.
- A breakdown below the opening low could signal bearish sentiment; traders might consider shorting or exiting longs.
By monitoring whether prices respect these boundaries within their respective ranges—or break through them—traders can make more informed decisions about entry and exit points during active hours.
Practical Strategies Using Opening Range
Traders employ various strategies centered around opening range analysis:
Range Trading:
- Buy near support (opening low)
- Sell near resistance (opening high)
- Use tight stop-loss orders just outside these boundaries
Breakout Trading:
- Enter trades when price breaks above resistance or below support with increased volume
- Confirm breakout validity with other indicators like RSI or moving averages
Fade Strategy:
- Trade against false breakouts by betting on reversals when price quickly re-enters previous ranges
Adjusting Stops & Targets:
- Use openings' high/low as dynamic stop-loss points
- Set profit targets based on measured distance between open-range boundaries
These approaches help manage risk effectively while capitalizing on predictable intraday patterns derived from early market activity.
Recent Advances Enhancing Opening Range Analysis
Technological progress has significantly improved how traders utilize opening ranges:
- Modern trading platforms provide real-time data feeds enabling precise calculation of initial highs/lows.
- Algorithmic tools now automatically identify key breakout moments based on predefined criteria.
- Integration with other technical indicators such as Bollinger Bands, RSI (Relative Strength Index), MACD (Moving Average Convergence Divergence), enhances confirmation signals.
- Increased adoption in volatile markets like cryptocurrencies demonstrates its versatility; crypto's rapid moves make early-range analysis particularly valuable for quick decision-making.
Furthermore, machine learning models are being developed to analyze historical patterns related to open-range behavior across different assets—adding predictive power beyond traditional methods.
Risks & Limitations of Relying Solely on Opening Range
While powerful, relying exclusively on opening range analysis carries risks:
- Overdependence may lead traders astray if unexpected news causes sudden volatility outside established ranges.
- Market manipulation tactics such as "spoofing" can artificially influence perceived support/resistance levels at open.
- False breakouts are common; not all breaches result in sustained moves—requiring confirmation from additional indicators.
Therefore, it's crucial always to combine OR-based insights with broader technical frameworks—including trend analysis and volume studies—to improve accuracy while managing risk effectively.
Applying Support & Resistance Levels Derived from Opening Range
In practice:
- Observe initial trade activity closely during first hour after market opens.
- Mark highest (resistance) and lowest (support) points reached within this period.
- Watch for signs of breakout beyond these bounds — confirmed by increased volume — which could signal strong directional moves.
- Use these levels dynamically throughout your trading session—for setting stops/limits—and adapt quickly if new information emerges.
Final Thoughts: Enhancing Intraday Strategies With Opening Range Insights
The ability of closing-in-time data from an asset’s first few minutes offers invaluable guidance for defining intraday support/resistance zones through its establishing of key thresholds reflective of current market sentiment—not just historical averages but real-time reactions at open sessions enable more responsive decision-making processes than static chart patterns alone would permit.
By integrating modern technological tools alongside traditional technical principles—including careful validation via multiple indicators—you elevate your capacity not only to recognize potential turning points but also craft disciplined strategies aligned with evolving conditions—all essential elements underpinning sustainable success in active day-trading environments.
Disclaimer:Contains third-party content. Not financial advice.
See Terms and Conditions.
⏳Countdown: 4 Days! The JuCoin Million Airdrop Invitation Boost is on!
Open the event page, click “Share” to quickly invite friends, and accelerate your reward growth.
This is your last chance to overtake — don’t miss it!
👉 Quick Share: https://bit.ly/40NWXjH
👉 Đăng ký Jucoin ngay: https://www.jucoin.com/pro/PARTNER
#JuCoin #JucoinVietnam #Airdrop


Lee Jucoin
2025-08-12 11:14
JuCoin Million Airdrop Plan🚀
Disclaimer:Contains third-party content. Not financial advice.
See Terms and Conditions.
The Golden Rule for Investing in Cryptocurrency: How Much Money Should You Allocate?
Understanding the appropriate amount of money to invest in cryptocurrency is crucial for managing risk and building a resilient investment portfolio. The "golden rule" offers a practical guideline that helps investors navigate this volatile market while maintaining financial stability.
What Is the Golden Rule for Cryptocurrency Investment?
The golden rule suggests that investors should allocate only a small percentage of their total investment portfolio to cryptocurrencies. Typically, financial advisors recommend no more than 5-10%. This approach aims to balance potential gains from the high-growth opportunities in digital assets with the inherent risks associated with their volatility and regulatory uncertainties.
Why Limit Your Cryptocurrency Exposure?
Cryptocurrencies are known for their rapid price swings, which can lead to significant gains or devastating losses within short periods. By limiting exposure, investors can participate in potential upside without jeopardizing their overall financial health. For example, if Bitcoin or other cryptocurrencies experience a sharp decline, having only a small portion of your portfolio invested ensures that your core finances remain protected.
Diversification as a Risk Management Strategy
Diversification remains one of the most effective strategies for reducing investment risk. The golden rule emphasizes spreading investments across various asset classes—stocks, bonds, real estate—and including cryptocurrencies at a modest level. This diversification helps cushion against market downturns specific to any single asset class and enhances long-term stability.
Recent Market Trends Supporting Limited Investment
In recent months, notable developments have fueled interest in cryptocurrencies:
Bitcoin Price Surge: Bitcoin has experienced significant upward momentum recently, with forecasts suggesting it could reach $200,000 or higher by 2025[1]. While promising growth prospects exist, such surges also attract speculative behavior.
ETF Inflows: The introduction of Bitcoin and gold ETFs has attracted substantial investor inflows[2][3], indicating increased institutional interest but also highlighting market volatility driven by speculation.
These trends underscore why cautious allocation—adhering to the golden rule—is essential; it allows investors to benefit from growth opportunities without exposing themselves excessively during volatile periods.
Financial Advice on Cryptocurrency Allocation
Most financial experts agree on setting clear boundaries when investing in digital assets:
Maximum Allocation: Generally recommended not to exceed 10% of your total investment portfolio.
Personal Financial Goals: Investors should assess their individual goals and risk tolerance before committing funds. For instance:
- Young investors with high-risk appetite might consider slightly higher allocations.
- Those nearing retirement should prioritize stability over aggressive growth.
Additionally, ensuring sufficient liquidity and emergency funds is vital before venturing into high-volatility markets like crypto.
Risks Associated With Overexposure
Investing more than recommended can expose you to severe consequences:
Market Volatility: Sudden price drops can wipe out large portions of an over-concentrated crypto holding.
Regulatory Changes: Lack of clear regulations means sudden policy shifts could impact prices dramatically.
Speculative Bubbles: Rapid surges driven by hype may lead to bubbles that burst unexpectedly.
Sticking within advised limits helps mitigate these risks while still allowing participation in potential upside scenarios.
Recent Developments Impacting Crypto Investments
The ongoing inflow into gold and Bitcoin ETFs reflects broader investor confidence but also signals heightened market speculation[2][3]. Investor sentiment remains positive due to factors like lower interest rates and increasing adoption; however, rapid shifts are possible if regulatory environments change or macroeconomic conditions deteriorate. Staying within prudent allocation limits ensures you’re prepared regardless of these fluctuations.
How To Apply the Golden Rule Effectively
To implement this guideline effectively:
- Assess your total investment portfolio value.
- Decide on an appropriate percentage (commonly between 5%–10%) based on your risk tolerance.
- Choose reputable exchanges or platforms for purchasing cryptocurrencies.
- Diversify within your crypto holdings—consider different coins rather than concentrating solely on Bitcoin or Ethereum.
- Regularly review your investments relative to market changes and personal circumstances.
By following these steps alongside sound financial advice—and keeping allocations modest—you position yourself better for long-term success while avoiding unnecessary exposure during turbulent times.
Balancing Growth Potential With Financial Security
While recent developments suggest promising growth prospects—such as Bitcoin’s forecasted surge—the importance lies in balancing opportunity with caution. Allocating too much capital exposes you not only to potential losses but also undermines overall financial security if markets turn unfavorable overnight.
Building Trust Through Knowledge & Caution
Investors aiming at sustainable wealth accumulation must prioritize education about cryptocurrency markets’ dynamics—including understanding volatility patterns and regulatory landscapes—to make informed decisions aligned with best practices like adhering strictly to the golden rule.
Staying Updated With Market Trends & Regulatory Changes
Given how rapidly digital asset markets evolve—with new ETFs launching or regulations shifting—it’s essential always stay informed through reputable sources such as industry reports or expert analyses[1][2][3]. This ongoing awareness supports disciplined investing aligned with sound principles rather than impulsive reactions.
Summary
Investing responsibly in cryptocurrency involves understanding how much exposure aligns with your overall financial plan—a principle encapsulated by what’s commonly called "the golden rule." Limiting investments typically between 5%–10%, diversifying holdings wisely, assessing personal risk tolerance carefully—all contribute toward harnessing crypto's growth potential without compromising long-term stability.
References[1] Perplexity AI. Bitcoin Price Nears $95,000 Amid ETF Inflows and Volatility. 2025-04-27.
[2] Perplexity AI.. Perplexity Finance.. 2025-05-22.
[3] Perplexity AI.. JPMorgan International Research Enhanced Equity ETF.. 2025-05-16.


Lo
2025-05-22 19:02
What is the golden rule about how much money to invest in cryptocurrency?
The Golden Rule for Investing in Cryptocurrency: How Much Money Should You Allocate?
Understanding the appropriate amount of money to invest in cryptocurrency is crucial for managing risk and building a resilient investment portfolio. The "golden rule" offers a practical guideline that helps investors navigate this volatile market while maintaining financial stability.
What Is the Golden Rule for Cryptocurrency Investment?
The golden rule suggests that investors should allocate only a small percentage of their total investment portfolio to cryptocurrencies. Typically, financial advisors recommend no more than 5-10%. This approach aims to balance potential gains from the high-growth opportunities in digital assets with the inherent risks associated with their volatility and regulatory uncertainties.
Why Limit Your Cryptocurrency Exposure?
Cryptocurrencies are known for their rapid price swings, which can lead to significant gains or devastating losses within short periods. By limiting exposure, investors can participate in potential upside without jeopardizing their overall financial health. For example, if Bitcoin or other cryptocurrencies experience a sharp decline, having only a small portion of your portfolio invested ensures that your core finances remain protected.
Diversification as a Risk Management Strategy
Diversification remains one of the most effective strategies for reducing investment risk. The golden rule emphasizes spreading investments across various asset classes—stocks, bonds, real estate—and including cryptocurrencies at a modest level. This diversification helps cushion against market downturns specific to any single asset class and enhances long-term stability.
Recent Market Trends Supporting Limited Investment
In recent months, notable developments have fueled interest in cryptocurrencies:
Bitcoin Price Surge: Bitcoin has experienced significant upward momentum recently, with forecasts suggesting it could reach $200,000 or higher by 2025[1]. While promising growth prospects exist, such surges also attract speculative behavior.
ETF Inflows: The introduction of Bitcoin and gold ETFs has attracted substantial investor inflows[2][3], indicating increased institutional interest but also highlighting market volatility driven by speculation.
These trends underscore why cautious allocation—adhering to the golden rule—is essential; it allows investors to benefit from growth opportunities without exposing themselves excessively during volatile periods.
Financial Advice on Cryptocurrency Allocation
Most financial experts agree on setting clear boundaries when investing in digital assets:
Maximum Allocation: Generally recommended not to exceed 10% of your total investment portfolio.
Personal Financial Goals: Investors should assess their individual goals and risk tolerance before committing funds. For instance:
- Young investors with high-risk appetite might consider slightly higher allocations.
- Those nearing retirement should prioritize stability over aggressive growth.
Additionally, ensuring sufficient liquidity and emergency funds is vital before venturing into high-volatility markets like crypto.
Risks Associated With Overexposure
Investing more than recommended can expose you to severe consequences:
Market Volatility: Sudden price drops can wipe out large portions of an over-concentrated crypto holding.
Regulatory Changes: Lack of clear regulations means sudden policy shifts could impact prices dramatically.
Speculative Bubbles: Rapid surges driven by hype may lead to bubbles that burst unexpectedly.
Sticking within advised limits helps mitigate these risks while still allowing participation in potential upside scenarios.
Recent Developments Impacting Crypto Investments
The ongoing inflow into gold and Bitcoin ETFs reflects broader investor confidence but also signals heightened market speculation[2][3]. Investor sentiment remains positive due to factors like lower interest rates and increasing adoption; however, rapid shifts are possible if regulatory environments change or macroeconomic conditions deteriorate. Staying within prudent allocation limits ensures you’re prepared regardless of these fluctuations.
How To Apply the Golden Rule Effectively
To implement this guideline effectively:
- Assess your total investment portfolio value.
- Decide on an appropriate percentage (commonly between 5%–10%) based on your risk tolerance.
- Choose reputable exchanges or platforms for purchasing cryptocurrencies.
- Diversify within your crypto holdings—consider different coins rather than concentrating solely on Bitcoin or Ethereum.
- Regularly review your investments relative to market changes and personal circumstances.
By following these steps alongside sound financial advice—and keeping allocations modest—you position yourself better for long-term success while avoiding unnecessary exposure during turbulent times.
Balancing Growth Potential With Financial Security
While recent developments suggest promising growth prospects—such as Bitcoin’s forecasted surge—the importance lies in balancing opportunity with caution. Allocating too much capital exposes you not only to potential losses but also undermines overall financial security if markets turn unfavorable overnight.
Building Trust Through Knowledge & Caution
Investors aiming at sustainable wealth accumulation must prioritize education about cryptocurrency markets’ dynamics—including understanding volatility patterns and regulatory landscapes—to make informed decisions aligned with best practices like adhering strictly to the golden rule.
Staying Updated With Market Trends & Regulatory Changes
Given how rapidly digital asset markets evolve—with new ETFs launching or regulations shifting—it’s essential always stay informed through reputable sources such as industry reports or expert analyses[1][2][3]. This ongoing awareness supports disciplined investing aligned with sound principles rather than impulsive reactions.
Summary
Investing responsibly in cryptocurrency involves understanding how much exposure aligns with your overall financial plan—a principle encapsulated by what’s commonly called "the golden rule." Limiting investments typically between 5%–10%, diversifying holdings wisely, assessing personal risk tolerance carefully—all contribute toward harnessing crypto's growth potential without compromising long-term stability.
References[1] Perplexity AI. Bitcoin Price Nears $95,000 Amid ETF Inflows and Volatility. 2025-04-27.
[2] Perplexity AI.. Perplexity Finance.. 2025-05-22.
[3] Perplexity AI.. JPMorgan International Research Enhanced Equity ETF.. 2025-05-16.
Disclaimer:Contains third-party content. Not financial advice.
See Terms and Conditions.
Understanding Beta: A Key Measure of Market Sensitivity
Beta is a fundamental concept in finance that helps investors understand how sensitive a security or portfolio is to movements in the overall market. It quantifies the degree to which an asset's price fluctuates relative to market changes, providing insight into its systematic risk. This metric is integral to modern portfolio theory (MPT), enabling investors to assess potential risks and returns more accurately.
In essence, beta acts as a gauge of volatility compared to the broader market index, such as the S&P 500. A beta value of 1 indicates that the security tends to move in tandem with the market—if the market rises or falls by 10%, so does this asset. A beta greater than 1 suggests higher volatility; for example, a beta of 1.5 implies that when the market increases by 10%, this security might increase by approximately 15%. Conversely, a beta less than 1 indicates lower sensitivity; for instance, a beta of 0.5 means it moves only half as much as the overall market.
Understanding what beta represents allows investors and financial analysts to evaluate how individual securities contribute to overall portfolio risk and performance. It also plays an essential role in constructing diversified portfolios aimed at balancing risk exposure against expected returns.
How Is Beta Calculated?
The calculation of beta involves statistical measures derived from historical return data:
- Covariance between an asset’s returns and those of the overall market.
- Variance of the market’s returns.
Mathematically, it is expressed as:
Beta = Covariance (Asset Returns, Market Returns) / Variance (Market Returns)This formula captures how closely an asset's price movements are linked with broader economic trends represented by benchmark indices like stocks or cryptocurrencies markets.
Financial platforms often provide pre-calculated betas based on extensive historical data analysis. However, it's important for investors and analysts to recognize that past performance does not always predict future behavior—especially in highly volatile markets like cryptocurrencies where rapid shifts can occur due to external factors such as regulatory news or technological developments.
The Role of Market Sensitivity in Investment Strategies
Market sensitivity directly influences investment decisions because it reflects how much an asset's value responds during different phases of economic cycles:
- Risk Assessment: High-beta assets tend to be more volatile but offer higher potential returns during bullish periods.
- Diversification: Combining low-beta assets with high-beta ones can help balance risk within a portfolio.
- Performance Benchmarking: Comparing an investment’s actual return against its expected movement based on its beta provides insights into managerial skill or mispricing.
Investors aiming for aggressive growth may prefer high-beta securities because they amplify gains when markets perform well but come with increased downside risks during downturns. Conversely, conservative investors might favor low-beta investments that tend not to fluctuate wildly even amid turbulent markets.
By understanding these dynamics through beta analysis, investors can tailor their strategies according to their risk tolerance levels while aligning with long-term financial goals.
Beta Beyond Traditional Markets: Focus on Cryptocurrencies
While initially developed for traditional stock markets, recent years have seen increasing application of beta analysis within cryptocurrency investing—a sector characterized by extreme volatility and rapid innovation. Cryptocurrencies like Bitcoin and Ethereum exhibit significant price swings driven by factors such as technological updates (e.g., network upgrades), regulatory developments across jurisdictions, macroeconomic trends affecting fiat currencies’ strength—and speculative trading behaviors fueled by social media hype.
In this context:
- Cryptocurrencies often display higher betas compared with traditional assets due primarily to their unpredictable nature.
- Regulatory uncertainty can cause sudden spikes or drops in prices—impacting their measured sensitivity.
- Technological advancements may either increase adoption (potentially lowering perceived risk) or introduce new vulnerabilities affecting stability metrics like beta.
As crypto markets mature further—with increased institutional participation—the relevance and accuracy of using measures like beta will improve but must be interpreted carefully given their unique characteristics compared with conventional equities or bonds.
Recent Trends Impacting Cryptocurrency Betas
The cryptocurrency landscape has experienced notable fluctuations over recent years:
The bull run from late 2020 through early 2021 saw Bitcoin reach all-time highs amid widespread institutional interest.
Subsequent corrections throughout late 2021 into early 2022 reflected heightened volatility driven partly by regulatory crackdowns globally and macroeconomic shifts such as rising interest rates.
These events underscore why understanding crypto-specific betas is crucial—they help quantify how sensitive digital assets are relative not just historically but also under evolving conditions influencing future performance expectations.
Risks Associated With Using Beta for Crypto Market Analysis
Applying traditional financial metrics like beta within cryptocurrency markets involves certain limitations:
Potential Pitfalls Include:
High Volatility & Manipulation: Crypto prices are susceptible not only due to genuine supply-demand dynamics but also through manipulation tactics such as pump-and-dump schemes which distort true sensitivities.
Regulatory Uncertainty: Sudden policy changes can drastically alter perceived risks—leading cryptos' betas astray from underlying fundamentals temporarily.
Limited Historical Data: Many newer cryptocurrencies lack extensive historical records necessary for reliable statistical calculations; thus estimates may be less accurate than those available for established stocks.
Despite these challenges, incorporating crypto-specific adjustments—such as shorter look-back periods or alternative measures—can improve insights derived frombeta analyses.
Managing Risks When Using Beta Metrics
To mitigate issues associated with high crypto-market volatility:
Combine multiple indicators alongsidebeta—for example , volume trends , sentiment analysis ,and macroeconomic factors .
Regularly update your calculations reflecting recent data rather than relying solely on long-term averages .
Use scenario analysis — assessing potential outcomes under different hypothetical conditions—to better understand possible sensitivities .
How Investors Can Use Beta Effectively
For both traditional equity portfolios and emerging digital assets strategies , understanding each security’sbeta helps craft balanced approaches aligned with personal risk appetite . Here are some practical tips :
Assess Risk Tolerance: Determine whether you prefer investments that amplify gains during bullish phases but also expose you more significantly during downturns—or if you favor steadier options less affected by broad-market swings .
Construct Diversified Portfolios: Mix high-betasecuritieswith lower-betasecuritiesto achieve desired exposure levels without overconcentrating on volatile segments .
Monitor Changes Over Time: Keep trackofbetavalues regularly sincemarketconditionsandassetvolatilities evolve . Adjust your holdings accordinglyto maintain alignmentwith your strategic objectives .
By integrating these practices into your investment process—including awareness about specific nuances relatedtocryptocurrencybetastakeholderscan make informed decisions rootedin soundrisk management principles .
Future Outlook: The Evolving Significance Of Beta
As financial markets continue evolving—with increasing integration between traditional finance sectorsand digital currencies—the importanceof measuringmarket sensitivity via metricslikebeta will grow stronger . Advances include :
Improved models incorporating real-time data analytics
– Enhanced tools leveraging machine learning algorithms
– Greater transparency around blockchain activity influencing valuation models
Furthermore,the ongoing maturationofcryptocurrencymarketswill likely leadto more standardized methodsfor calculatingand interpretingbetas,increasingtheir reliabilityfor both retailandinstitutionalinvestors alike.
Final Thoughts
Understanding whatbeta signifies—andhow it evaluatesa strategy’smarket sensitivity—is vitalfor making informedinvestment choices across diverseasset classes.In particular,the unique characteristicsofcryptocurrencies demand carefulapplicationand interpretationofthis metric.To navigate today’s complexfinancial landscape successfully requires combining quantitative toolslikebetawith qualitative insights aboutregulatory,trends,and technological developments.This holistic approach empowersinvestors tomaximizereturnswhilemanagingrisks effectivelyin bothtraditionalandin emergingmarkets.


JCUSER-F1IIaxXA
2025-05-10 00:27
What is Beta and how does it evaluate a strategy’s market sensitivity?
Understanding Beta: A Key Measure of Market Sensitivity
Beta is a fundamental concept in finance that helps investors understand how sensitive a security or portfolio is to movements in the overall market. It quantifies the degree to which an asset's price fluctuates relative to market changes, providing insight into its systematic risk. This metric is integral to modern portfolio theory (MPT), enabling investors to assess potential risks and returns more accurately.
In essence, beta acts as a gauge of volatility compared to the broader market index, such as the S&P 500. A beta value of 1 indicates that the security tends to move in tandem with the market—if the market rises or falls by 10%, so does this asset. A beta greater than 1 suggests higher volatility; for example, a beta of 1.5 implies that when the market increases by 10%, this security might increase by approximately 15%. Conversely, a beta less than 1 indicates lower sensitivity; for instance, a beta of 0.5 means it moves only half as much as the overall market.
Understanding what beta represents allows investors and financial analysts to evaluate how individual securities contribute to overall portfolio risk and performance. It also plays an essential role in constructing diversified portfolios aimed at balancing risk exposure against expected returns.
How Is Beta Calculated?
The calculation of beta involves statistical measures derived from historical return data:
- Covariance between an asset’s returns and those of the overall market.
- Variance of the market’s returns.
Mathematically, it is expressed as:
Beta = Covariance (Asset Returns, Market Returns) / Variance (Market Returns)This formula captures how closely an asset's price movements are linked with broader economic trends represented by benchmark indices like stocks or cryptocurrencies markets.
Financial platforms often provide pre-calculated betas based on extensive historical data analysis. However, it's important for investors and analysts to recognize that past performance does not always predict future behavior—especially in highly volatile markets like cryptocurrencies where rapid shifts can occur due to external factors such as regulatory news or technological developments.
The Role of Market Sensitivity in Investment Strategies
Market sensitivity directly influences investment decisions because it reflects how much an asset's value responds during different phases of economic cycles:
- Risk Assessment: High-beta assets tend to be more volatile but offer higher potential returns during bullish periods.
- Diversification: Combining low-beta assets with high-beta ones can help balance risk within a portfolio.
- Performance Benchmarking: Comparing an investment’s actual return against its expected movement based on its beta provides insights into managerial skill or mispricing.
Investors aiming for aggressive growth may prefer high-beta securities because they amplify gains when markets perform well but come with increased downside risks during downturns. Conversely, conservative investors might favor low-beta investments that tend not to fluctuate wildly even amid turbulent markets.
By understanding these dynamics through beta analysis, investors can tailor their strategies according to their risk tolerance levels while aligning with long-term financial goals.
Beta Beyond Traditional Markets: Focus on Cryptocurrencies
While initially developed for traditional stock markets, recent years have seen increasing application of beta analysis within cryptocurrency investing—a sector characterized by extreme volatility and rapid innovation. Cryptocurrencies like Bitcoin and Ethereum exhibit significant price swings driven by factors such as technological updates (e.g., network upgrades), regulatory developments across jurisdictions, macroeconomic trends affecting fiat currencies’ strength—and speculative trading behaviors fueled by social media hype.
In this context:
- Cryptocurrencies often display higher betas compared with traditional assets due primarily to their unpredictable nature.
- Regulatory uncertainty can cause sudden spikes or drops in prices—impacting their measured sensitivity.
- Technological advancements may either increase adoption (potentially lowering perceived risk) or introduce new vulnerabilities affecting stability metrics like beta.
As crypto markets mature further—with increased institutional participation—the relevance and accuracy of using measures like beta will improve but must be interpreted carefully given their unique characteristics compared with conventional equities or bonds.
Recent Trends Impacting Cryptocurrency Betas
The cryptocurrency landscape has experienced notable fluctuations over recent years:
The bull run from late 2020 through early 2021 saw Bitcoin reach all-time highs amid widespread institutional interest.
Subsequent corrections throughout late 2021 into early 2022 reflected heightened volatility driven partly by regulatory crackdowns globally and macroeconomic shifts such as rising interest rates.
These events underscore why understanding crypto-specific betas is crucial—they help quantify how sensitive digital assets are relative not just historically but also under evolving conditions influencing future performance expectations.
Risks Associated With Using Beta for Crypto Market Analysis
Applying traditional financial metrics like beta within cryptocurrency markets involves certain limitations:
Potential Pitfalls Include:
High Volatility & Manipulation: Crypto prices are susceptible not only due to genuine supply-demand dynamics but also through manipulation tactics such as pump-and-dump schemes which distort true sensitivities.
Regulatory Uncertainty: Sudden policy changes can drastically alter perceived risks—leading cryptos' betas astray from underlying fundamentals temporarily.
Limited Historical Data: Many newer cryptocurrencies lack extensive historical records necessary for reliable statistical calculations; thus estimates may be less accurate than those available for established stocks.
Despite these challenges, incorporating crypto-specific adjustments—such as shorter look-back periods or alternative measures—can improve insights derived frombeta analyses.
Managing Risks When Using Beta Metrics
To mitigate issues associated with high crypto-market volatility:
Combine multiple indicators alongsidebeta—for example , volume trends , sentiment analysis ,and macroeconomic factors .
Regularly update your calculations reflecting recent data rather than relying solely on long-term averages .
Use scenario analysis — assessing potential outcomes under different hypothetical conditions—to better understand possible sensitivities .
How Investors Can Use Beta Effectively
For both traditional equity portfolios and emerging digital assets strategies , understanding each security’sbeta helps craft balanced approaches aligned with personal risk appetite . Here are some practical tips :
Assess Risk Tolerance: Determine whether you prefer investments that amplify gains during bullish phases but also expose you more significantly during downturns—or if you favor steadier options less affected by broad-market swings .
Construct Diversified Portfolios: Mix high-betasecuritieswith lower-betasecuritiesto achieve desired exposure levels without overconcentrating on volatile segments .
Monitor Changes Over Time: Keep trackofbetavalues regularly sincemarketconditionsandassetvolatilities evolve . Adjust your holdings accordinglyto maintain alignmentwith your strategic objectives .
By integrating these practices into your investment process—including awareness about specific nuances relatedtocryptocurrencybetastakeholderscan make informed decisions rootedin soundrisk management principles .
Future Outlook: The Evolving Significance Of Beta
As financial markets continue evolving—with increasing integration between traditional finance sectorsand digital currencies—the importanceof measuringmarket sensitivity via metricslikebeta will grow stronger . Advances include :
Improved models incorporating real-time data analytics
– Enhanced tools leveraging machine learning algorithms
– Greater transparency around blockchain activity influencing valuation models
Furthermore,the ongoing maturationofcryptocurrencymarketswill likely leadto more standardized methodsfor calculatingand interpretingbetas,increasingtheir reliabilityfor both retailandinstitutionalinvestors alike.
Final Thoughts
Understanding whatbeta signifies—andhow it evaluatesa strategy’smarket sensitivity—is vitalfor making informedinvestment choices across diverseasset classes.In particular,the unique characteristicsofcryptocurrencies demand carefulapplicationand interpretationofthis metric.To navigate today’s complexfinancial landscape successfully requires combining quantitative toolslikebetawith qualitative insights aboutregulatory,trends,and technological developments.This holistic approach empowersinvestors tomaximizereturnswhilemanagingrisks effectivelyin bothtraditionalandin emergingmarkets.
Disclaimer:Contains third-party content. Not financial advice.
See Terms and Conditions.
👉 Invite, Deposit, Trade to get Hash Power & share $50,000 Prize Pool! 🚀
⏰ Time: 19:00 19/08/2025 – 19:00 28/08/2025 (UTC+7)
✅ Event 1: Invite friends, get Hash Power and reward up to 100 JU!
✅ Event 2: Exclusive for Newbies – 100% Deposit Cashback!
✅ Event 3: Trade to share $50,000 Prize Pool!
🔸 Register for JuCoin now: https://bit.ly/3BVxlZ2
🔸 Join now: https://www.jucoin.com/en/landing-page/SpotEvent0818
👉 Details: https://support.jucoin.blog/hc/en-001/articles/49891489208729
#JuCoin #JuCoinVietnam #CryptoRewards #Airdrop #Crypto #DeFi #Web3 #Blockchain


Lee Jucoin
2025-08-19 06:42
📣 "JuCoin Triple Rewards" event is officially launched! 🎉
Disclaimer:Contains third-party content. Not financial advice.
See Terms and Conditions.
Best Practices for Ensuring Safe Use of Decentralized Applications (dApps)
Decentralized applications, or dApps, are transforming how we interact with digital services by leveraging blockchain technology. They promise transparency, security, and community-driven control but also come with unique risks that users and developers must navigate carefully. Understanding the best practices for safe use is essential to protect assets, maintain trust, and foster sustainable growth in this innovative space.
Understanding Decentralized Applications and Their Security Challenges
Decentralized applications operate on blockchain networks using smart contracts—self-executing code that automates transactions based on predefined rules. Unlike traditional apps hosted on centralized servers, dApps distribute data across multiple nodes worldwide. This architecture reduces single points of failure but introduces specific vulnerabilities such as smart contract bugs, phishing scams, and reentrancy attacks.
Smart contract vulnerabilities are among the most critical risks because once deployed without proper auditing, they can be exploited to drain funds or manipulate outcomes. Phishing remains a common threat where malicious actors impersonate legitimate dApps or wallets to steal private keys or credentials. Reentrancy attacks exploit recursive calls within smart contracts to drain assets unexpectedly.
Given these challenges, adopting comprehensive safety measures is vital for both users engaging with dApps and developers building them.
Conduct Regular Smart Contract Audits
One of the foundational best practices is conducting thorough audits of smart contracts before deployment. These audits involve analyzing code for vulnerabilities using specialized tools like Etherscan’s security features or open-source frameworks such as OpenZeppelin’s security libraries. Engaging reputable cybersecurity firms specializing in blockchain ensures an independent review that can identify hidden flaws not apparent during initial development.
Regular audits should also be part of ongoing maintenance—especially after updates or feature additions—to ensure new code doesn’t introduce vulnerabilities. Transparent audit reports build user confidence by demonstrating a commitment to security standards.
Educate Users About Risks and Safe Practices
User education plays a crucial role in maintaining safety within the decentralized ecosystem. Many incidents stem from simple mistakes like falling victim to phishing scams or mishandling private keys. Providing clear guidance on recognizing authentic dApp links versus malicious sites helps prevent credential theft.
Encouraging users to verify URLs carefully before connecting wallets minimizes exposure to impersonation attempts. Additionally, promoting awareness about common attack vectors—such as social engineering tactics—empowers users to make informed decisions when interacting with decentralized platforms.
Educational resources should include tutorials on setting up hardware wallets securely (e.g., Ledger or Trezor), understanding transaction confirmations, and avoiding sharing sensitive information online.
Implement Multi-Signature Wallets for Enhanced Security
Multi-signature (multi-sig) wallets require multiple private keys before executing transactions—a significant upgrade over single-key setups prone to theft if compromised. For organizations managing large funds via dApps or communities participating in governance tokens, multi-sig arrangements add an extra layer of protection against unauthorized access.
This approach ensures no single individual can unilaterally move assets without consensus from designated signatories—a critical safeguard against internal threats and external hacking attempts alike.
Keep Software Up-to-Date With Latest Security Patches
The rapidly evolving nature of blockchain technology means software updates often include important security patches addressing newly discovered vulnerabilities. Users should regularly update their wallet applications—including browser extensions—and ensure their operating systems are current with latest patches from vendors like Apple or Microsoft.
Developers must also prioritize deploying updates promptly after fixing bugs identified through audits or bug bounty programs; delaying these updates leaves systems exposed unnecessarily.
Protect Against Phishing Attacks Through Vigilance
Phishing remains one of the most prevalent threats targeting dApp users due to its simplicity yet high impact potential when successful. Attackers craft convincing fake websites mimicking legitimate platforms aiming to steal login credentials or seed phrases used for wallet recovery.
To mitigate this risk:
- Always verify website URLs carefully.
- Avoid clicking links received via unsolicited emails.
- Use bookmarks for trusted sites.
- Enable two-factor authentication where possible.
Educating your community about these precautions significantly reduces susceptibility toward phishing schemes.
Backup Wallet Data Securely
In case of hardware failure thefts—or accidental loss—having secure backups ensures asset recovery without catastrophic loss. Hardware wallets like Ledger Nano S/Trezor provide seed phrases that allow restoring access across devices if needed.
Best practices include:
- Storing backup seed phrases offline in secure locations.
- Using encrypted storage solutions.
- Avoiding cloud-based backups susceptible to hacking.
Regularly updating backup copies guarantees they remain valid even after software changes over time.
Engage With Community & Participate in Bug Bounty Programs
Active engagement within developer communities enhances overall ecosystem safety by fostering transparency around potential issues early on rather than waiting until exploits occur publicly.
Many projects now run bug bounty programs incentivizing white-hat hackers worldwide who discover vulnerabilities responsibly before malicious actors do — leading directly toward more resilient systems.
Participating actively helps you stay informed about emerging threats while contributing positively toward collective cybersecurity efforts.
Recent Developments Improving Safety Standards
The landscape surrounding decentralized application safety continues improving thanks largely due to recent innovations:
Regulatory Clarity: Governments increasingly clarify legal frameworks around cryptocurrencies which encourages responsible development practices while reducing uncertainty that could lead developers astray into risky behaviors.
Advanced Security Tools: Companies such as Chainalysis offer sophisticated analytics solutions capable of monitoring illicit activities—including money laundering—in real-time across blockchain networks enhancing compliance efforts globally.
Bug Bounty Initiatives: The proliferation of bug bounty programs incentivizes proactive vulnerability discovery; some projects have rewarded millions USD worth of bounties leading directly toward safer deployments.
Enhanced Risk Management Strategies: DeFi protocols now incorporate collateralization safeguards alongside insurance options designed specifically against flash loan exploits—a common attack vector recently gaining prominence.
Risks That Still Loom Large
Despite progress made through best practices and technological advancements several risks persist:
- User errors resulting in lost funds remain prevalent if individuals neglect recommended precautions such as backups & verification steps
- Regulatory crackdowns could impose restrictions hindering innovation if compliance isn’t prioritized
- Major breaches could tarnish entire ecosystems’ reputation causing widespread distrust among new adopters
Staying vigilant by continuously applying updated best practices is essential for mitigating these dangers effectively.
Staying Ahead: The Path Forward
As decentralization continues expanding into mainstream finance (DeFi), gaming NFTs, DAOs—and beyond—the importance placed upon robust security measures grows exponentially.. Developers must prioritize transparent auditing processes; educate their communities proactively; implement multi-signature controls; keep all software current; monitor emerging threats vigilantly—and participate actively within ecosystems through bug bounty initiatives.
By doing so not only protects individual assets but also fosters trust necessary for broader adoption—all while contributing meaningfully towards a safer decentralized future.
This article aims at providing clarity around practical steps everyone involved with dApps can take today.


JCUSER-WVMdslBw
2025-05-23 01:42
What best practices ensure safe use of decentralized applications?
Best Practices for Ensuring Safe Use of Decentralized Applications (dApps)
Decentralized applications, or dApps, are transforming how we interact with digital services by leveraging blockchain technology. They promise transparency, security, and community-driven control but also come with unique risks that users and developers must navigate carefully. Understanding the best practices for safe use is essential to protect assets, maintain trust, and foster sustainable growth in this innovative space.
Understanding Decentralized Applications and Their Security Challenges
Decentralized applications operate on blockchain networks using smart contracts—self-executing code that automates transactions based on predefined rules. Unlike traditional apps hosted on centralized servers, dApps distribute data across multiple nodes worldwide. This architecture reduces single points of failure but introduces specific vulnerabilities such as smart contract bugs, phishing scams, and reentrancy attacks.
Smart contract vulnerabilities are among the most critical risks because once deployed without proper auditing, they can be exploited to drain funds or manipulate outcomes. Phishing remains a common threat where malicious actors impersonate legitimate dApps or wallets to steal private keys or credentials. Reentrancy attacks exploit recursive calls within smart contracts to drain assets unexpectedly.
Given these challenges, adopting comprehensive safety measures is vital for both users engaging with dApps and developers building them.
Conduct Regular Smart Contract Audits
One of the foundational best practices is conducting thorough audits of smart contracts before deployment. These audits involve analyzing code for vulnerabilities using specialized tools like Etherscan’s security features or open-source frameworks such as OpenZeppelin’s security libraries. Engaging reputable cybersecurity firms specializing in blockchain ensures an independent review that can identify hidden flaws not apparent during initial development.
Regular audits should also be part of ongoing maintenance—especially after updates or feature additions—to ensure new code doesn’t introduce vulnerabilities. Transparent audit reports build user confidence by demonstrating a commitment to security standards.
Educate Users About Risks and Safe Practices
User education plays a crucial role in maintaining safety within the decentralized ecosystem. Many incidents stem from simple mistakes like falling victim to phishing scams or mishandling private keys. Providing clear guidance on recognizing authentic dApp links versus malicious sites helps prevent credential theft.
Encouraging users to verify URLs carefully before connecting wallets minimizes exposure to impersonation attempts. Additionally, promoting awareness about common attack vectors—such as social engineering tactics—empowers users to make informed decisions when interacting with decentralized platforms.
Educational resources should include tutorials on setting up hardware wallets securely (e.g., Ledger or Trezor), understanding transaction confirmations, and avoiding sharing sensitive information online.
Implement Multi-Signature Wallets for Enhanced Security
Multi-signature (multi-sig) wallets require multiple private keys before executing transactions—a significant upgrade over single-key setups prone to theft if compromised. For organizations managing large funds via dApps or communities participating in governance tokens, multi-sig arrangements add an extra layer of protection against unauthorized access.
This approach ensures no single individual can unilaterally move assets without consensus from designated signatories—a critical safeguard against internal threats and external hacking attempts alike.
Keep Software Up-to-Date With Latest Security Patches
The rapidly evolving nature of blockchain technology means software updates often include important security patches addressing newly discovered vulnerabilities. Users should regularly update their wallet applications—including browser extensions—and ensure their operating systems are current with latest patches from vendors like Apple or Microsoft.
Developers must also prioritize deploying updates promptly after fixing bugs identified through audits or bug bounty programs; delaying these updates leaves systems exposed unnecessarily.
Protect Against Phishing Attacks Through Vigilance
Phishing remains one of the most prevalent threats targeting dApp users due to its simplicity yet high impact potential when successful. Attackers craft convincing fake websites mimicking legitimate platforms aiming to steal login credentials or seed phrases used for wallet recovery.
To mitigate this risk:
- Always verify website URLs carefully.
- Avoid clicking links received via unsolicited emails.
- Use bookmarks for trusted sites.
- Enable two-factor authentication where possible.
Educating your community about these precautions significantly reduces susceptibility toward phishing schemes.
Backup Wallet Data Securely
In case of hardware failure thefts—or accidental loss—having secure backups ensures asset recovery without catastrophic loss. Hardware wallets like Ledger Nano S/Trezor provide seed phrases that allow restoring access across devices if needed.
Best practices include:
- Storing backup seed phrases offline in secure locations.
- Using encrypted storage solutions.
- Avoiding cloud-based backups susceptible to hacking.
Regularly updating backup copies guarantees they remain valid even after software changes over time.
Engage With Community & Participate in Bug Bounty Programs
Active engagement within developer communities enhances overall ecosystem safety by fostering transparency around potential issues early on rather than waiting until exploits occur publicly.
Many projects now run bug bounty programs incentivizing white-hat hackers worldwide who discover vulnerabilities responsibly before malicious actors do — leading directly toward more resilient systems.
Participating actively helps you stay informed about emerging threats while contributing positively toward collective cybersecurity efforts.
Recent Developments Improving Safety Standards
The landscape surrounding decentralized application safety continues improving thanks largely due to recent innovations:
Regulatory Clarity: Governments increasingly clarify legal frameworks around cryptocurrencies which encourages responsible development practices while reducing uncertainty that could lead developers astray into risky behaviors.
Advanced Security Tools: Companies such as Chainalysis offer sophisticated analytics solutions capable of monitoring illicit activities—including money laundering—in real-time across blockchain networks enhancing compliance efforts globally.
Bug Bounty Initiatives: The proliferation of bug bounty programs incentivizes proactive vulnerability discovery; some projects have rewarded millions USD worth of bounties leading directly toward safer deployments.
Enhanced Risk Management Strategies: DeFi protocols now incorporate collateralization safeguards alongside insurance options designed specifically against flash loan exploits—a common attack vector recently gaining prominence.
Risks That Still Loom Large
Despite progress made through best practices and technological advancements several risks persist:
- User errors resulting in lost funds remain prevalent if individuals neglect recommended precautions such as backups & verification steps
- Regulatory crackdowns could impose restrictions hindering innovation if compliance isn’t prioritized
- Major breaches could tarnish entire ecosystems’ reputation causing widespread distrust among new adopters
Staying vigilant by continuously applying updated best practices is essential for mitigating these dangers effectively.
Staying Ahead: The Path Forward
As decentralization continues expanding into mainstream finance (DeFi), gaming NFTs, DAOs—and beyond—the importance placed upon robust security measures grows exponentially.. Developers must prioritize transparent auditing processes; educate their communities proactively; implement multi-signature controls; keep all software current; monitor emerging threats vigilantly—and participate actively within ecosystems through bug bounty initiatives.
By doing so not only protects individual assets but also fosters trust necessary for broader adoption—all while contributing meaningfully towards a safer decentralized future.
This article aims at providing clarity around practical steps everyone involved with dApps can take today.
Disclaimer:Contains third-party content. Not financial advice.
See Terms and Conditions.
