How Can Machine Learning Algorithms Classify Chart Patterns?
Machine learning has transformed many industries, and financial markets are no exception. One of the most promising applications is in classifying chart patterns—visual representations of price movements that traders rely on for decision-making. Understanding how machine learning algorithms can identify and categorize these patterns offers insights into the future of automated trading and technical analysis.
What Are Chart Pattern Classifications?
Chart pattern classification involves using advanced algorithms to analyze financial charts—such as candlestick or line graphs—and automatically recognize specific formations like head and shoulders, double tops/bottoms, flags, or triangles. These patterns often signal potential trend reversals or continuations, guiding traders on when to buy or sell assets.
Traditionally, human analysts interpret these visual cues based on experience. However, manual analysis can be subjective and time-consuming. Machine learning automates this process by training models to detect subtle features within chart data rapidly and with high accuracy.
The Role of Machine Learning in Financial Market Analysis
The integration of machine learning into finance isn't new but has gained momentum due to increased computational power and data availability. Early efforts focused on simple models; today’s deep learning techniques enable complex pattern recognition akin to image processing tasks.
In cryptocurrency markets—characterized by high volatility and rapid price changes—the need for real-time analysis makes machine learning especially valuable. Automated systems can process vast amounts of historical data quickly, providing timely signals that might be missed through manual analysis.
Types of Machine Learning Algorithms Used in Chart Pattern Recognition
Different types of machine learning approaches serve various purposes in pattern classification:
Supervised Learning: This method trains models using labeled datasets where each chart is tagged with its corresponding pattern type (e.g., bullish flag). Once trained, the model can classify new charts based on learned features.
Unsupervised Learning: Here, algorithms like clustering group similar patterns without predefined labels. This approach helps discover new or rare formations that may not fit traditional categories.
Reinforcement Learning: Models learn optimal trading strategies through trial-and-error interactions with market environments rather than static datasets. They adapt over time to maximize profits based on feedback signals.
Popular Techniques & Architectures
Convolutional Neural Networks (CNNs): Originally designed for image recognition tasks, CNNs excel at analyzing visual data such as chart images—they identify edges, shapes, and textures indicative of specific patterns.
Recurrent Neural Networks (RNNs): Suitable for sequential data like time series; RNNs analyze the order-dependent nature of price movements over time.
Gradient Boosting Machines (GBMs): Ensemble methods combining multiple weak classifiers; effective for structured tabular data derived from technical indicators alongside raw chart images.
Challenges Faced by Machine Learning Models
Despite their advantages, deploying machine learning for chart pattern classification comes with hurdles:
Data Quality & Noise: Financial market data often contains noise due to random fluctuations or incomplete records which can mislead models if not properly preprocessed.
Overfitting Risks: Complex models might memorize training examples rather than generalize well across unseen data—a problem known as overfitting—which reduces predictive reliability during live trading.
Regulatory Considerations: As automated strategies become more prevalent, compliance with legal frameworks becomes critical—especially regarding transparency and fairness in algorithmic decision-making.
Recent Advances Enhancing Pattern Recognition Accuracy
Recent developments have significantly improved how effectively machines classify chart patterns:
Deep neural networks incorporating attention mechanisms allow models to focus selectively on relevant parts of a chart image or sequence.
Transformer architectures—originally popularized in natural language processing—are now being adapted for financial time-series analysis due to their ability to capture long-term dependencies within market data.
Combining multiple analytical tools such as sentiment analysis from news feeds alongside technical indicators creates more holistic trading signals driven by comprehensive AI systems.
Open-source frameworks like TensorFlow and PyTorch have democratized access so researchers worldwide can develop sophisticated models without starting from scratch—all contributing toward faster innovation cycles in this domain.
Impact & Future Outlook
The widespread adoption of machine learning-based classification could influence overall market efficiency by reducing information asymmetry among traders who leverage these tools extensively. While this democratization enhances transparency overall—it also raises concerns about potential market manipulation if used irresponsibly.
Automation may lead some roles traditionally performed manually by analysts becoming obsolete; however—as with any technological shift—it also opens opportunities for professionals skilled at developing advanced AI-driven strategies.
Regulators are increasingly scrutinizing algorithmic trading practices; ensuring ethical standards remain vital as AI's role expands within financial ecosystems.
Key Takeaways:
- Machine learning automates identification/classification of complex chart formations
- Deep architectures like CNNs/RNNs improve detection accuracy
- Challenges include noisy datasets & overfitting risks
- Recent innovations involve attention mechanisms & transformer-based models
- Widespread use impacts market dynamics & regulatory landscape
By understanding how these intelligent systems work behind the scenes—from training neural networks on historical charts to deploying them live—you gain a clearer picture of modern technical analysis's future trajectory—and how it continues transforming investment strategies worldwide.
Semantic Keywords:
machine learning finance | stock/chart pattern recognition | deep neural networks trading | automated technical analysis | AI cryptocurrency markets | supervised vs unsupervised ML | reinforcement learning trading strategies


kai
2025-05-09 21:30
How can machine learning algorithms classify chart patterns?
How Can Machine Learning Algorithms Classify Chart Patterns?
Machine learning has transformed many industries, and financial markets are no exception. One of the most promising applications is in classifying chart patterns—visual representations of price movements that traders rely on for decision-making. Understanding how machine learning algorithms can identify and categorize these patterns offers insights into the future of automated trading and technical analysis.
What Are Chart Pattern Classifications?
Chart pattern classification involves using advanced algorithms to analyze financial charts—such as candlestick or line graphs—and automatically recognize specific formations like head and shoulders, double tops/bottoms, flags, or triangles. These patterns often signal potential trend reversals or continuations, guiding traders on when to buy or sell assets.
Traditionally, human analysts interpret these visual cues based on experience. However, manual analysis can be subjective and time-consuming. Machine learning automates this process by training models to detect subtle features within chart data rapidly and with high accuracy.
The Role of Machine Learning in Financial Market Analysis
The integration of machine learning into finance isn't new but has gained momentum due to increased computational power and data availability. Early efforts focused on simple models; today’s deep learning techniques enable complex pattern recognition akin to image processing tasks.
In cryptocurrency markets—characterized by high volatility and rapid price changes—the need for real-time analysis makes machine learning especially valuable. Automated systems can process vast amounts of historical data quickly, providing timely signals that might be missed through manual analysis.
Types of Machine Learning Algorithms Used in Chart Pattern Recognition
Different types of machine learning approaches serve various purposes in pattern classification:
Supervised Learning: This method trains models using labeled datasets where each chart is tagged with its corresponding pattern type (e.g., bullish flag). Once trained, the model can classify new charts based on learned features.
Unsupervised Learning: Here, algorithms like clustering group similar patterns without predefined labels. This approach helps discover new or rare formations that may not fit traditional categories.
Reinforcement Learning: Models learn optimal trading strategies through trial-and-error interactions with market environments rather than static datasets. They adapt over time to maximize profits based on feedback signals.
Popular Techniques & Architectures
Convolutional Neural Networks (CNNs): Originally designed for image recognition tasks, CNNs excel at analyzing visual data such as chart images—they identify edges, shapes, and textures indicative of specific patterns.
Recurrent Neural Networks (RNNs): Suitable for sequential data like time series; RNNs analyze the order-dependent nature of price movements over time.
Gradient Boosting Machines (GBMs): Ensemble methods combining multiple weak classifiers; effective for structured tabular data derived from technical indicators alongside raw chart images.
Challenges Faced by Machine Learning Models
Despite their advantages, deploying machine learning for chart pattern classification comes with hurdles:
Data Quality & Noise: Financial market data often contains noise due to random fluctuations or incomplete records which can mislead models if not properly preprocessed.
Overfitting Risks: Complex models might memorize training examples rather than generalize well across unseen data—a problem known as overfitting—which reduces predictive reliability during live trading.
Regulatory Considerations: As automated strategies become more prevalent, compliance with legal frameworks becomes critical—especially regarding transparency and fairness in algorithmic decision-making.
Recent Advances Enhancing Pattern Recognition Accuracy
Recent developments have significantly improved how effectively machines classify chart patterns:
Deep neural networks incorporating attention mechanisms allow models to focus selectively on relevant parts of a chart image or sequence.
Transformer architectures—originally popularized in natural language processing—are now being adapted for financial time-series analysis due to their ability to capture long-term dependencies within market data.
Combining multiple analytical tools such as sentiment analysis from news feeds alongside technical indicators creates more holistic trading signals driven by comprehensive AI systems.
Open-source frameworks like TensorFlow and PyTorch have democratized access so researchers worldwide can develop sophisticated models without starting from scratch—all contributing toward faster innovation cycles in this domain.
Impact & Future Outlook
The widespread adoption of machine learning-based classification could influence overall market efficiency by reducing information asymmetry among traders who leverage these tools extensively. While this democratization enhances transparency overall—it also raises concerns about potential market manipulation if used irresponsibly.
Automation may lead some roles traditionally performed manually by analysts becoming obsolete; however—as with any technological shift—it also opens opportunities for professionals skilled at developing advanced AI-driven strategies.
Regulators are increasingly scrutinizing algorithmic trading practices; ensuring ethical standards remain vital as AI's role expands within financial ecosystems.
Key Takeaways:
- Machine learning automates identification/classification of complex chart formations
- Deep architectures like CNNs/RNNs improve detection accuracy
- Challenges include noisy datasets & overfitting risks
- Recent innovations involve attention mechanisms & transformer-based models
- Widespread use impacts market dynamics & regulatory landscape
By understanding how these intelligent systems work behind the scenes—from training neural networks on historical charts to deploying them live—you gain a clearer picture of modern technical analysis's future trajectory—and how it continues transforming investment strategies worldwide.
Semantic Keywords:
machine learning finance | stock/chart pattern recognition | deep neural networks trading | automated technical analysis | AI cryptocurrency markets | supervised vs unsupervised ML | reinforcement learning trading strategies
Disclaimer:Contains third-party content. Not financial advice.
See Terms and Conditions.
What Are Common Crypto Scams? An In-Depth Overview
Cryptocurrency has revolutionized the financial landscape, offering new opportunities for investment and innovation. However, this rapidly evolving market also attracts scammers who exploit investors’ lack of awareness or security measures. Understanding the most common crypto scams—such as rug pulls, phishing attacks, and Ponzi schemes—is essential for anyone involved in digital assets. This article provides a comprehensive overview of these scams, their mechanisms, recent developments, and how to protect yourself.
Rug Pulls: The Sudden Disappearance of Promising Projects
A rug pull is a type of scam where developers create a new cryptocurrency project or token with attractive features but then abruptly abandon it after attracting investor funds. Typically, scammers will hype up their project through social media or online communities to generate interest and investment. Once enough capital is gathered—often from unsuspecting retail investors—the developers withdraw all liquidity or sell off their holdings en masse, causing the token’s value to crash.
This scam often targets lesser-known cryptocurrencies that lack rigorous security audits or active community oversight. The allure lies in promises of high returns with minimal risk; however, once the developers disappear with investor funds—sometimes amounting to hundreds of millions—they leave behind worthless tokens.
Recent high-profile incidents include the infamous Poly Network hack in 2022 where over $600 million was stolen by hackers exploiting vulnerabilities rather than traditional rug pull tactics. While not always classified strictly as rug pulls, such exploits highlight how malicious actors can cause significant financial damage within crypto ecosystems.
Investors should exercise caution by researching projects thoroughly before investing and avoiding tokens without transparent development teams or clear use cases.
Phishing Attacks: Deceiving Users into Revealing Sensitive Data
Phishing remains one of the most prevalent threats in cryptocurrency security today. It involves cybercriminals masquerading as legitimate entities—such as exchanges like Coinbase or popular wallet providers—to trick users into revealing private keys, login credentials, or seed phrases.
These scams often take place via fake websites that mimic official platforms closely enough to deceive even experienced users. Attackers may send convincing emails containing links directing victims to these counterfeit sites or use social media messages that appear trustworthy but are designed solely for data theft.
In recent years—including 2023—the sophistication level of phishing attacks has increased significantly with AI-generated content and deepfake videos making scams more convincing than ever before. Cybercriminals also leverage fake apps on app stores that look identical to genuine ones but are designed solely for stealing user information upon installation.
The consequences can be severe: stolen cryptocurrencies can be transferred instantly once attackers gain access; additionally, compromised accounts may lead to further identity theft issues beyond just financial loss.
To mitigate risks:
- Always verify URLs before entering sensitive information.
- Enable two-factor authentication (2FA) on your accounts.
- Be cautious about unsolicited messages requesting personal data.
- Use reputable security tools like password managers and anti-phishing extensions.
Ponzi Schemes: Unsustainable Investment Promises
Ponzi schemes are fraudulent investment operations promising high returns over short periods without actual profit-generating activities backing those promises. Instead of earning profits from legitimate business ventures—or blockchain-based innovations—these schemes pay existing investors using funds contributed by new participants until they inevitably collapse when recruitment slows down.
In the context of cryptocurrencies:
- Many Ponzi schemes promise unrealistic gains through trading bots or “guaranteed” investments.
- Some have been disguised as NFT projects promising rapid appreciation.
Recent examples include several uncovered schemes in 2024 involving NFT collections claiming extraordinary returns which proved unsustainable upon investigation by authorities and industry watchdogs alike.
The fallout from Ponzi schemes extends beyond individual losses; they erode trust within the broader crypto ecosystem and discourage genuine innovation due to skepticism among potential investors who have been burned previously.
Key Indicators That Might Signal a Scam
To avoid falling victim:
- Be wary if an investment guarantees unusually high returns with little risk.
- Check whether there’s transparency about how profits are generated.
- Investigate whether there’s an active community discussing legitimacy.
Understanding these warning signs helps safeguard your investments against falling prey to fraudulent operations posing as legitimate opportunities.
Recent Developments Highlighting Crypto Scam Risks
The landscape continues evolving rapidly amid increasing sophistication among cybercriminals:
Major Data Breaches
In May 2025—a significant event involved Coinbase disclosing a data breach where cybercriminals bribed overseas support agents into stealing sensitive customer information[1]. Such breaches expose vulnerabilities even within reputable exchanges known for robust security measures emphasizing industry-wide risks associated with centralized platforms handling vast amounts of user data.
Industry Response & Security Enhancements
Recognizing these threats:
- Google released Android 16 updates featuring advanced security protocols aimed at combating cryptocurrency fraud[2].
These developments reflect ongoing efforts across sectors—from tech giants like Google implementing enhanced protections—to better defend users against emerging threats such as phishing campaigns and malware targeting digital wallets.
The Importance Of Vigilance
As scams become more sophisticated—with AI-driven tactics becoming commonplace—it’s crucial for users not only rely on technological safeguards but also stay informed about current scam trends through trusted sources like cybersecurity advisories issued by industry leaders.
How To Protect Yourself From Crypto Scams
Being proactive is key when navigating the volatile world of cryptocurrencies:
Educate Yourself: Stay updated on common scam techniques via reputable sources such as official exchange blogs or cybersecurity organizations’ reports.
Use Secure Platforms: Only transact through well-known exchanges with strong reputations for security practices—including regular audits—and enable all available safety features (e.g., two-factor authentication).
Verify Before Acting: Always double-check website URLs; avoid clicking links from unsolicited emails; confirm authenticity directly via official channels rather than third-party messages unless verified independently .
Secure Your Private Keys: Never share seed phrases nor store them insecurely—in physical form if possible—and consider hardware wallets for long-term storage instead of keeping assets online vulnerable to hacking attempts .
Stay Alert For Red Flags: Be suspicious if an offer sounds too good-to-be-real; watch out for urgent language pressuring quick decisions; scrutinize project backgrounds thoroughly before investing.
By understanding common crypto scams such as rug pulls, phishing attacks,and Ponzi schemes—and recognizing recent developments—you can better navigate this dynamic environment safely while contributing positively toward building trustworthiness within blockchain communities.
References
- Coinbase offers bounty after data breach exposes sensitive customer information.
- Google showcases Android 16 with enhanced security features.
Note: Always consult multiple sources when researching specific incidents related to cybersecurity threats in cryptocurrency markets since threat landscapes evolve rapidly.*


Lo
2025-05-23 00:44
What are common crypto scams—rug pulls, phishing, Ponzi schemes?
What Are Common Crypto Scams? An In-Depth Overview
Cryptocurrency has revolutionized the financial landscape, offering new opportunities for investment and innovation. However, this rapidly evolving market also attracts scammers who exploit investors’ lack of awareness or security measures. Understanding the most common crypto scams—such as rug pulls, phishing attacks, and Ponzi schemes—is essential for anyone involved in digital assets. This article provides a comprehensive overview of these scams, their mechanisms, recent developments, and how to protect yourself.
Rug Pulls: The Sudden Disappearance of Promising Projects
A rug pull is a type of scam where developers create a new cryptocurrency project or token with attractive features but then abruptly abandon it after attracting investor funds. Typically, scammers will hype up their project through social media or online communities to generate interest and investment. Once enough capital is gathered—often from unsuspecting retail investors—the developers withdraw all liquidity or sell off their holdings en masse, causing the token’s value to crash.
This scam often targets lesser-known cryptocurrencies that lack rigorous security audits or active community oversight. The allure lies in promises of high returns with minimal risk; however, once the developers disappear with investor funds—sometimes amounting to hundreds of millions—they leave behind worthless tokens.
Recent high-profile incidents include the infamous Poly Network hack in 2022 where over $600 million was stolen by hackers exploiting vulnerabilities rather than traditional rug pull tactics. While not always classified strictly as rug pulls, such exploits highlight how malicious actors can cause significant financial damage within crypto ecosystems.
Investors should exercise caution by researching projects thoroughly before investing and avoiding tokens without transparent development teams or clear use cases.
Phishing Attacks: Deceiving Users into Revealing Sensitive Data
Phishing remains one of the most prevalent threats in cryptocurrency security today. It involves cybercriminals masquerading as legitimate entities—such as exchanges like Coinbase or popular wallet providers—to trick users into revealing private keys, login credentials, or seed phrases.
These scams often take place via fake websites that mimic official platforms closely enough to deceive even experienced users. Attackers may send convincing emails containing links directing victims to these counterfeit sites or use social media messages that appear trustworthy but are designed solely for data theft.
In recent years—including 2023—the sophistication level of phishing attacks has increased significantly with AI-generated content and deepfake videos making scams more convincing than ever before. Cybercriminals also leverage fake apps on app stores that look identical to genuine ones but are designed solely for stealing user information upon installation.
The consequences can be severe: stolen cryptocurrencies can be transferred instantly once attackers gain access; additionally, compromised accounts may lead to further identity theft issues beyond just financial loss.
To mitigate risks:
- Always verify URLs before entering sensitive information.
- Enable two-factor authentication (2FA) on your accounts.
- Be cautious about unsolicited messages requesting personal data.
- Use reputable security tools like password managers and anti-phishing extensions.
Ponzi Schemes: Unsustainable Investment Promises
Ponzi schemes are fraudulent investment operations promising high returns over short periods without actual profit-generating activities backing those promises. Instead of earning profits from legitimate business ventures—or blockchain-based innovations—these schemes pay existing investors using funds contributed by new participants until they inevitably collapse when recruitment slows down.
In the context of cryptocurrencies:
- Many Ponzi schemes promise unrealistic gains through trading bots or “guaranteed” investments.
- Some have been disguised as NFT projects promising rapid appreciation.
Recent examples include several uncovered schemes in 2024 involving NFT collections claiming extraordinary returns which proved unsustainable upon investigation by authorities and industry watchdogs alike.
The fallout from Ponzi schemes extends beyond individual losses; they erode trust within the broader crypto ecosystem and discourage genuine innovation due to skepticism among potential investors who have been burned previously.
Key Indicators That Might Signal a Scam
To avoid falling victim:
- Be wary if an investment guarantees unusually high returns with little risk.
- Check whether there’s transparency about how profits are generated.
- Investigate whether there’s an active community discussing legitimacy.
Understanding these warning signs helps safeguard your investments against falling prey to fraudulent operations posing as legitimate opportunities.
Recent Developments Highlighting Crypto Scam Risks
The landscape continues evolving rapidly amid increasing sophistication among cybercriminals:
Major Data Breaches
In May 2025—a significant event involved Coinbase disclosing a data breach where cybercriminals bribed overseas support agents into stealing sensitive customer information[1]. Such breaches expose vulnerabilities even within reputable exchanges known for robust security measures emphasizing industry-wide risks associated with centralized platforms handling vast amounts of user data.
Industry Response & Security Enhancements
Recognizing these threats:
- Google released Android 16 updates featuring advanced security protocols aimed at combating cryptocurrency fraud[2].
These developments reflect ongoing efforts across sectors—from tech giants like Google implementing enhanced protections—to better defend users against emerging threats such as phishing campaigns and malware targeting digital wallets.
The Importance Of Vigilance
As scams become more sophisticated—with AI-driven tactics becoming commonplace—it’s crucial for users not only rely on technological safeguards but also stay informed about current scam trends through trusted sources like cybersecurity advisories issued by industry leaders.
How To Protect Yourself From Crypto Scams
Being proactive is key when navigating the volatile world of cryptocurrencies:
Educate Yourself: Stay updated on common scam techniques via reputable sources such as official exchange blogs or cybersecurity organizations’ reports.
Use Secure Platforms: Only transact through well-known exchanges with strong reputations for security practices—including regular audits—and enable all available safety features (e.g., two-factor authentication).
Verify Before Acting: Always double-check website URLs; avoid clicking links from unsolicited emails; confirm authenticity directly via official channels rather than third-party messages unless verified independently .
Secure Your Private Keys: Never share seed phrases nor store them insecurely—in physical form if possible—and consider hardware wallets for long-term storage instead of keeping assets online vulnerable to hacking attempts .
Stay Alert For Red Flags: Be suspicious if an offer sounds too good-to-be-real; watch out for urgent language pressuring quick decisions; scrutinize project backgrounds thoroughly before investing.
By understanding common crypto scams such as rug pulls, phishing attacks,and Ponzi schemes—and recognizing recent developments—you can better navigate this dynamic environment safely while contributing positively toward building trustworthiness within blockchain communities.
References
- Coinbase offers bounty after data breach exposes sensitive customer information.
- Google showcases Android 16 with enhanced security features.
Note: Always consult multiple sources when researching specific incidents related to cybersecurity threats in cryptocurrency markets since threat landscapes evolve rapidly.*
Disclaimer:Contains third-party content. Not financial advice.
See Terms and Conditions.
📣 Limited benefit for new trading pair! Listing $DAM/USDT Futures trading with 50% off trading fees for 10 days! 🎉
🔥 To celebrate the official launch of $DAM-USDT futures, #JuCoin offers a special promotion: Users who trade $DAM/USDT Futures during the event will enjoy a 50% off trading fee for 10 days!
⏰ Time: 19:30 18/08/2025 – 19:30 28/08/2025 (UTC+7)
👉 Register for JuCoin now: https://bit.ly/3BVxlZ2
👉 Details: https://support.jucoin.blog/hc/en-001/articles/49893231322009
#JuCoin #JuCoinVietnam #DAM #JuCoinTrading #TradingFutures #JuCoinFutures #JuCoinListing #NewListing


Lee Jucoin
2025-08-19 06:43
📣 Limited benefit for new trading pair! 🎉
Disclaimer:Contains third-party content. Not financial advice.
See Terms and Conditions.
How Do Ecosystem Grants and Incentives Drive Project Growth?
Ecosystem grants and incentives have become essential tools for fostering innovation and sustainable development within the crypto and investment sectors. As blockchain technology, decentralized finance (DeFi), and emerging tech continue to evolve rapidly, these financial supports help projects overcome early-stage funding hurdles while encouraging community participation. Understanding how these grants influence project growth is key for entrepreneurs, investors, and community members alike.
What Are Ecosystem Grants in Crypto and Investment?
Ecosystem grants are financial awards provided by organizations—such as blockchain foundations, venture capital firms, or community groups—to support promising projects. These grants serve as catalysts for development by offering resources that enable teams to focus on building their solutions without the immediate pressure of fundraising. In the crypto space especially, these funds often target specific areas like blockchain infrastructure, decentralized applications (dApps), or innovative protocols.
There are generally three types of ecosystem grants:
- Crypto-specific Grants: Focused on blockchain development, smart contract creation, security audits, or DeFi innovations.
- General Ecosystem Grants: Broader in scope; they may support AI integration with fintech platforms or other emerging technologies.
- Community-driven Grants: Funded directly by user communities or organizations aligned with specific values; they emphasize social impact or grassroots initiatives.
These varied grant types reflect a strategic approach to nurturing diverse technological advancements while fostering inclusive growth within ecosystems.
How Do Ecosystem Incentives Promote Project Development?
The primary goal of ecosystem incentives is to accelerate project growth through targeted funding coupled with non-financial benefits such as mentorships, technical support, networking opportunities, and visibility within the community. These incentives motivate developers to innovate confidently because they reduce initial financial risks—a critical factor during early stages when securing traditional funding can be challenging.
By providing clear pathways for project validation—through milestones like product launches or user adoption—ecosystem incentives also encourage accountability among recipients. This structured approach ensures that funded projects align with broader ecosystem goals such as decentralization principles or interoperability standards.
Furthermore,these programs often foster collaboration among startups,established companies,and academic institutions,creating a vibrant environment conducive to knowledge sharingand joint innovation efforts.
The Impact of Funding Growth on Project Success
Recent years have seen a surge in funds allocated toward ecosystem grants globally. This increase correlates strongly with the expansion of DeFi platforms and enterprise-grade blockchain solutions seeking mainstream adoption. Larger grant pools mean more ambitious projects can get off the ground—ranging from scalable Layer 2 solutions to privacy-preserving protocols—and contribute significantly toward industry evolution.
Moreover,diversification in grant programs has broadened access across various sectors beyond pure cryptocurrency applications.For instance:
- Fintech startups integrating blockchain
- AI-powered analytics tools
- Sustainability-focused crypto initiatives
This diversification not only fuels technological progress but also attracts a wider range of talent into ecosystems previously dominated solely by core crypto developers.
Community Engagement: A Key Driver
Community-driven grants have gained prominence because they leverage collective enthusiasm around particular projects or causes. When users invest their time and resources into supporting initiatives aligned with their values—such as environmental sustainability through green tokens—they create organic momentum that sustains long-term project viability.
In addition,community engagement enhances transparencyand accountability since stakeholders directly influence decision-making processes related to fund allocation.This participatory model fosters trust between developers and users—a crucial element amid increasing regulatory scrutiny worldwide.
Challenges Facing Ecosystem Grant Programs
Despite their benefits,ecosystem grants face several challenges that could impede long-term success:
Regulatory Uncertainty: As governments tighten regulations around cryptocurrencies and token offerings,compliance becomes complex.Grant providers must ensure programs adhere to legal frameworks to avoid reputational damage or legal repercussions.
Market Volatility: Cryptocurrency markets are highly volatile;the value of granted tokens can fluctuate dramatically.This volatility impacts project sustainability if revenue models depend heavily on token appreciation rather than real-world utility.
Over-reliance on External Funding: Projects overly dependent on continuous grant inflows risk stagnation once funding diminishes unless diversified revenue streams develop over time.
Navigating Future Trends in Ecosystem Incentives
Looking ahead,
the landscape will likely see increased emphasis on compliance mechanisms,
more sophisticated evaluation criteria,
and greater integration between public-private partnerships.
Additionally,
regulators may introduce clearer guidelines tailored specifically for grant programs,
ensuring transparency while protecting investor interests.
Projects should focus not only on securing initial funding but also establishing sustainable business models that leverage ecosystem support effectively over time.
Final Thoughts: Supporting Sustainable Innovation Through Strategic Incentives
Ecosystem grants play an instrumental role in shaping the future trajectory of crypto innovations by lowering barriers for new entrants while promoting collaborative growth environments. They act as accelerators—not just providing capital but also fostering community involvement vital for long-term success.
However,
stakeholders must remain vigilant about regulatory developments
and market dynamics
to maximize benefits from these incentive structures without exposing themselves unnecessarily to risks.
As this field continues evolving rapidly,
a balanced approach combining strategic funding with compliance awareness will be essential
for ensuring resilient growth across all facets of the digital economy.
Keywords: ecosystem grants crypto | investment incentives | blockchain project funding | DeFi development support | community-driven crypto projects | startup incubation crypto | regulatory challenges in crypto financing


JCUSER-F1IIaxXA
2025-05-22 02:51
How do ecosystem grants and incentives drive project growth?
How Do Ecosystem Grants and Incentives Drive Project Growth?
Ecosystem grants and incentives have become essential tools for fostering innovation and sustainable development within the crypto and investment sectors. As blockchain technology, decentralized finance (DeFi), and emerging tech continue to evolve rapidly, these financial supports help projects overcome early-stage funding hurdles while encouraging community participation. Understanding how these grants influence project growth is key for entrepreneurs, investors, and community members alike.
What Are Ecosystem Grants in Crypto and Investment?
Ecosystem grants are financial awards provided by organizations—such as blockchain foundations, venture capital firms, or community groups—to support promising projects. These grants serve as catalysts for development by offering resources that enable teams to focus on building their solutions without the immediate pressure of fundraising. In the crypto space especially, these funds often target specific areas like blockchain infrastructure, decentralized applications (dApps), or innovative protocols.
There are generally three types of ecosystem grants:
- Crypto-specific Grants: Focused on blockchain development, smart contract creation, security audits, or DeFi innovations.
- General Ecosystem Grants: Broader in scope; they may support AI integration with fintech platforms or other emerging technologies.
- Community-driven Grants: Funded directly by user communities or organizations aligned with specific values; they emphasize social impact or grassroots initiatives.
These varied grant types reflect a strategic approach to nurturing diverse technological advancements while fostering inclusive growth within ecosystems.
How Do Ecosystem Incentives Promote Project Development?
The primary goal of ecosystem incentives is to accelerate project growth through targeted funding coupled with non-financial benefits such as mentorships, technical support, networking opportunities, and visibility within the community. These incentives motivate developers to innovate confidently because they reduce initial financial risks—a critical factor during early stages when securing traditional funding can be challenging.
By providing clear pathways for project validation—through milestones like product launches or user adoption—ecosystem incentives also encourage accountability among recipients. This structured approach ensures that funded projects align with broader ecosystem goals such as decentralization principles or interoperability standards.
Furthermore,these programs often foster collaboration among startups,established companies,and academic institutions,creating a vibrant environment conducive to knowledge sharingand joint innovation efforts.
The Impact of Funding Growth on Project Success
Recent years have seen a surge in funds allocated toward ecosystem grants globally. This increase correlates strongly with the expansion of DeFi platforms and enterprise-grade blockchain solutions seeking mainstream adoption. Larger grant pools mean more ambitious projects can get off the ground—ranging from scalable Layer 2 solutions to privacy-preserving protocols—and contribute significantly toward industry evolution.
Moreover,diversification in grant programs has broadened access across various sectors beyond pure cryptocurrency applications.For instance:
- Fintech startups integrating blockchain
- AI-powered analytics tools
- Sustainability-focused crypto initiatives
This diversification not only fuels technological progress but also attracts a wider range of talent into ecosystems previously dominated solely by core crypto developers.
Community Engagement: A Key Driver
Community-driven grants have gained prominence because they leverage collective enthusiasm around particular projects or causes. When users invest their time and resources into supporting initiatives aligned with their values—such as environmental sustainability through green tokens—they create organic momentum that sustains long-term project viability.
In addition,community engagement enhances transparencyand accountability since stakeholders directly influence decision-making processes related to fund allocation.This participatory model fosters trust between developers and users—a crucial element amid increasing regulatory scrutiny worldwide.
Challenges Facing Ecosystem Grant Programs
Despite their benefits,ecosystem grants face several challenges that could impede long-term success:
Regulatory Uncertainty: As governments tighten regulations around cryptocurrencies and token offerings,compliance becomes complex.Grant providers must ensure programs adhere to legal frameworks to avoid reputational damage or legal repercussions.
Market Volatility: Cryptocurrency markets are highly volatile;the value of granted tokens can fluctuate dramatically.This volatility impacts project sustainability if revenue models depend heavily on token appreciation rather than real-world utility.
Over-reliance on External Funding: Projects overly dependent on continuous grant inflows risk stagnation once funding diminishes unless diversified revenue streams develop over time.
Navigating Future Trends in Ecosystem Incentives
Looking ahead,
the landscape will likely see increased emphasis on compliance mechanisms,
more sophisticated evaluation criteria,
and greater integration between public-private partnerships.
Additionally,
regulators may introduce clearer guidelines tailored specifically for grant programs,
ensuring transparency while protecting investor interests.
Projects should focus not only on securing initial funding but also establishing sustainable business models that leverage ecosystem support effectively over time.
Final Thoughts: Supporting Sustainable Innovation Through Strategic Incentives
Ecosystem grants play an instrumental role in shaping the future trajectory of crypto innovations by lowering barriers for new entrants while promoting collaborative growth environments. They act as accelerators—not just providing capital but also fostering community involvement vital for long-term success.
However,
stakeholders must remain vigilant about regulatory developments
and market dynamics
to maximize benefits from these incentive structures without exposing themselves unnecessarily to risks.
As this field continues evolving rapidly,
a balanced approach combining strategic funding with compliance awareness will be essential
for ensuring resilient growth across all facets of the digital economy.
Keywords: ecosystem grants crypto | investment incentives | blockchain project funding | DeFi development support | community-driven crypto projects | startup incubation crypto | regulatory challenges in crypto financing
Disclaimer:Contains third-party content. Not financial advice.
See Terms and Conditions.
What Is Sharding in Blockchain?
Sharding is a transformative scalability solution designed to enhance the performance and efficiency of blockchain networks. As blockchain technology gains widespread adoption, the need to process increasing numbers of transactions quickly and securely becomes critical. Sharding addresses this challenge by dividing the entire network into smaller, manageable segments called shards, each capable of processing transactions independently. This division allows multiple transactions to be processed simultaneously, significantly reducing congestion and improving overall throughput.
In essence, sharding enables a blockchain network to operate more like a distributed database rather than a single monolithic ledger. Each shard functions as its own mini-blockchain with its unique state and transaction history but remains interconnected within the larger network framework. This structure not only boosts transaction speeds but also helps in scaling blockchain solutions for real-world applications such as decentralized finance (DeFi), supply chain management, and enterprise solutions.
How Does Sharding Work in Blockchain Networks?
The core idea behind sharding involves splitting the workload across various smaller components—shards—that work concurrently. Each shard processes a subset of all transactions based on specific criteria such as user accounts or data types. For example, one shard might handle payment transactions while another manages smart contract interactions.
To maintain consistency across these independent shards, mechanisms like cross-shard communication are implemented. These protocols ensure that when users perform transactions involving multiple shards—say transferring assets from one account managed by one shard to another managed by different shards—the system can verify and record these operations accurately without compromising security or integrity.
Shards typically operate as separate blockchains known as "shard chains." They maintain their own states—such as account balances or smart contract data—and process their designated set of transactions independently before periodically syncing with other shards through consensus protocols designed for cross-shard validation.
Types of Sharding
There are primarily two types of sharding used in blockchain systems:
Horizontal Sharding: This approach divides the network based on transaction types or user groups—for instance, separating payment processing from smart contract execution.
Vertical Sharding: Here, data is partitioned based on storage needs or data categories—for example, storing different kinds of information (user profiles vs transactional logs) separately across various shards.
Both methods aim to optimize resource utilization while maintaining security and decentralization principles inherent in blockchain technology.
Benefits of Implementing Sharding
Implementing sharding offers several significant advantages:
Enhanced Scalability: By distributing transaction loads across multiple shards, networks can handle many more operations per second compared to traditional single-chain architectures.
Reduced Transaction Fees: Faster processing times mean less congestion; consequently, users often experience lower fees during peak usage periods.
Improved Network Efficiency: Smaller nodes manage fewer tasks within each shard—they require less computational power and storage capacity—making participation easier for more validators.
Parallel Processing: Multiple parts of the network work simultaneously rather than sequentially; this parallelism accelerates overall throughput significantly.
These benefits make sharded blockchains suitable for large-scale applications where high speed and low latency are essential requirements.
Challenges Associated With Blockchain Sharding
Despite its promising potential, implementing sharding introduces complex technical challenges that must be addressed:
Inter-Shard Communication
Ensuring seamless communication between different shards is vital yet difficult. Transactions involving multiple shards require secure protocols that prevent double-spending or inconsistencies—a problem known as cross-shard communication complexity.
Consensus Mechanisms Across Multiple Shards
Traditional consensus algorithms like Proof-of-Work (PoW) are not inherently designed for multi-shard environments. Developing efficient consensus models that work reliably across numerous independent chains remains an ongoing research area within blockchain development communities.
Security Concerns
Dividing a network into smaller segments increases vulnerability risks; if one shard becomes compromised due to an attack or bug exploitation—a scenario called "shard takeover"—it could threaten the entire ecosystem's security integrity unless robust safeguards are implemented effectively throughout all parts of the system.
Standardization & Adoption Barriers
For widespread adoption beyond experimental phases requires industry-wide standards governing how sharded networks communicate and interoperate seamlessly. Without standardization efforts among developers and stakeholders worldwide—including major platforms like Ethereum—the risk exists that fragmentation could hinder progress rather than accelerate it.
Recent Developments in Blockchain Sharding Technology
Major projects have made notable strides toward integrating sharding into their ecosystems:
Ethereum 2.0 has been at the forefront with plans for scalable upgrades through its phased rollout strategy involving beacon chains (launched December 2020). The next steps include deploying dedicated shard chains alongside cross-shard communication protocols aimed at enabling Ethereum’s massive ecosystem to scale efficiently without sacrificing decentralization or security standards.
Polkadot employs relay chains connecting parachains—independent blockchains optimized for specific use cases—that communicate via shared security models facilitating interoperability among diverse networks.
Cosmos, utilizing Tendermint Core consensus algorithm architecture allows developers to create zones (independent blockchains) capable of interoperation within an overarching hub-and-spoke model similar to Polkadot’s relay chain approach.
Research continues globally exploring innovative techniques such as state sharding, which aims at optimizing how state information is stored across nodes—a crucial factor influencing scalability limits further improvements.
Potential Risks Impacting Future Adoption
While promising solutions exist today—and ongoing research promises even better approaches—the path forward faces hurdles related mainly to:
Security Risks: Smaller individual shards may become targets due to reduced validation power compared with full nodes operating on entire networks.
Interoperability Challenges: Achieving flawless interaction between diverse systems requires standardized protocols; otherwise fragmentation may occur leading toward isolated ecosystems instead of unified platforms.
Adoption Hurdles & Industry Standardization
Without broad agreement on technical standards governing cross-shard communications—as well as regulatory considerations—widespread deployment might slow down considerably despite technological readiness.
Understanding How Blockchain Scaling Evolves Through Sharding
As demand grows exponentially—from DeFi applications demanding rapid trades versus enterprise-level integrations requiring high throughput—the importance lies not just in creating faster blockchains but ensuring they remain secure against evolving threats while interoperable enough for global adoption.
By addressing current limitations through continuous innovation—in protocol design improvements like state sharing techniques—and fostering collaboration among industry leaders worldwide who develop open standards —the future landscape looks promising: scalable yet secure decentralized systems capable enough for mainstream use.
This comprehensive overview provides clarity about what sharding entails within blockchain technology: how it works technically; why it matters; what benefits it offers; what challenges lie ahead; along with recent advancements shaping its future trajectory—all aligned towards helping users understand both foundational concepts and cutting-edge developments effectively.


Lo
2025-05-15 02:38
What is sharding in blockchain?
What Is Sharding in Blockchain?
Sharding is a transformative scalability solution designed to enhance the performance and efficiency of blockchain networks. As blockchain technology gains widespread adoption, the need to process increasing numbers of transactions quickly and securely becomes critical. Sharding addresses this challenge by dividing the entire network into smaller, manageable segments called shards, each capable of processing transactions independently. This division allows multiple transactions to be processed simultaneously, significantly reducing congestion and improving overall throughput.
In essence, sharding enables a blockchain network to operate more like a distributed database rather than a single monolithic ledger. Each shard functions as its own mini-blockchain with its unique state and transaction history but remains interconnected within the larger network framework. This structure not only boosts transaction speeds but also helps in scaling blockchain solutions for real-world applications such as decentralized finance (DeFi), supply chain management, and enterprise solutions.
How Does Sharding Work in Blockchain Networks?
The core idea behind sharding involves splitting the workload across various smaller components—shards—that work concurrently. Each shard processes a subset of all transactions based on specific criteria such as user accounts or data types. For example, one shard might handle payment transactions while another manages smart contract interactions.
To maintain consistency across these independent shards, mechanisms like cross-shard communication are implemented. These protocols ensure that when users perform transactions involving multiple shards—say transferring assets from one account managed by one shard to another managed by different shards—the system can verify and record these operations accurately without compromising security or integrity.
Shards typically operate as separate blockchains known as "shard chains." They maintain their own states—such as account balances or smart contract data—and process their designated set of transactions independently before periodically syncing with other shards through consensus protocols designed for cross-shard validation.
Types of Sharding
There are primarily two types of sharding used in blockchain systems:
Horizontal Sharding: This approach divides the network based on transaction types or user groups—for instance, separating payment processing from smart contract execution.
Vertical Sharding: Here, data is partitioned based on storage needs or data categories—for example, storing different kinds of information (user profiles vs transactional logs) separately across various shards.
Both methods aim to optimize resource utilization while maintaining security and decentralization principles inherent in blockchain technology.
Benefits of Implementing Sharding
Implementing sharding offers several significant advantages:
Enhanced Scalability: By distributing transaction loads across multiple shards, networks can handle many more operations per second compared to traditional single-chain architectures.
Reduced Transaction Fees: Faster processing times mean less congestion; consequently, users often experience lower fees during peak usage periods.
Improved Network Efficiency: Smaller nodes manage fewer tasks within each shard—they require less computational power and storage capacity—making participation easier for more validators.
Parallel Processing: Multiple parts of the network work simultaneously rather than sequentially; this parallelism accelerates overall throughput significantly.
These benefits make sharded blockchains suitable for large-scale applications where high speed and low latency are essential requirements.
Challenges Associated With Blockchain Sharding
Despite its promising potential, implementing sharding introduces complex technical challenges that must be addressed:
Inter-Shard Communication
Ensuring seamless communication between different shards is vital yet difficult. Transactions involving multiple shards require secure protocols that prevent double-spending or inconsistencies—a problem known as cross-shard communication complexity.
Consensus Mechanisms Across Multiple Shards
Traditional consensus algorithms like Proof-of-Work (PoW) are not inherently designed for multi-shard environments. Developing efficient consensus models that work reliably across numerous independent chains remains an ongoing research area within blockchain development communities.
Security Concerns
Dividing a network into smaller segments increases vulnerability risks; if one shard becomes compromised due to an attack or bug exploitation—a scenario called "shard takeover"—it could threaten the entire ecosystem's security integrity unless robust safeguards are implemented effectively throughout all parts of the system.
Standardization & Adoption Barriers
For widespread adoption beyond experimental phases requires industry-wide standards governing how sharded networks communicate and interoperate seamlessly. Without standardization efforts among developers and stakeholders worldwide—including major platforms like Ethereum—the risk exists that fragmentation could hinder progress rather than accelerate it.
Recent Developments in Blockchain Sharding Technology
Major projects have made notable strides toward integrating sharding into their ecosystems:
Ethereum 2.0 has been at the forefront with plans for scalable upgrades through its phased rollout strategy involving beacon chains (launched December 2020). The next steps include deploying dedicated shard chains alongside cross-shard communication protocols aimed at enabling Ethereum’s massive ecosystem to scale efficiently without sacrificing decentralization or security standards.
Polkadot employs relay chains connecting parachains—independent blockchains optimized for specific use cases—that communicate via shared security models facilitating interoperability among diverse networks.
Cosmos, utilizing Tendermint Core consensus algorithm architecture allows developers to create zones (independent blockchains) capable of interoperation within an overarching hub-and-spoke model similar to Polkadot’s relay chain approach.
Research continues globally exploring innovative techniques such as state sharding, which aims at optimizing how state information is stored across nodes—a crucial factor influencing scalability limits further improvements.
Potential Risks Impacting Future Adoption
While promising solutions exist today—and ongoing research promises even better approaches—the path forward faces hurdles related mainly to:
Security Risks: Smaller individual shards may become targets due to reduced validation power compared with full nodes operating on entire networks.
Interoperability Challenges: Achieving flawless interaction between diverse systems requires standardized protocols; otherwise fragmentation may occur leading toward isolated ecosystems instead of unified platforms.
Adoption Hurdles & Industry Standardization
Without broad agreement on technical standards governing cross-shard communications—as well as regulatory considerations—widespread deployment might slow down considerably despite technological readiness.
Understanding How Blockchain Scaling Evolves Through Sharding
As demand grows exponentially—from DeFi applications demanding rapid trades versus enterprise-level integrations requiring high throughput—the importance lies not just in creating faster blockchains but ensuring they remain secure against evolving threats while interoperable enough for global adoption.
By addressing current limitations through continuous innovation—in protocol design improvements like state sharing techniques—and fostering collaboration among industry leaders worldwide who develop open standards —the future landscape looks promising: scalable yet secure decentralized systems capable enough for mainstream use.
This comprehensive overview provides clarity about what sharding entails within blockchain technology: how it works technically; why it matters; what benefits it offers; what challenges lie ahead; along with recent advancements shaping its future trajectory—all aligned towards helping users understand both foundational concepts and cutting-edge developments effectively.
Disclaimer:Contains third-party content. Not financial advice.
See Terms and Conditions.
🔍 David Schwartz (CTO) rappelle que :
• Ripple opère moins de **1% des validateurs**
• Les évolutions de XRPL dépendent du **consensus communautaire**
• Les milliards en escrow sont **verrouillés par smart contracts**, sans accès direct
👉 Une piqûre de rappel importante sur la gouvernance réelle des protocoles.
#XRP #crypto #cryptocurrency



Carmelita
2025-08-07 14:15
🚨 Fin des fantasmes : Ripple ne contrôle pas le $XRP Ledger.
Disclaimer:Contains third-party content. Not financial advice.
See Terms and Conditions.
What Is DBSCAN and How Does It Detect Unusual Market Conditions?
Understanding how financial markets, especially volatile ones like cryptocurrencies, can be monitored for anomalies is crucial for traders, analysts, and regulators alike. One powerful tool gaining traction in this space is DBSCAN—short for Density-Based Spatial Clustering of Applications with Noise. This clustering algorithm helps identify unusual patterns or outliers in complex datasets by grouping similar data points together based on their density.
How Does DBSCAN Work?
At its core, DBSCAN analyzes data points—such as price movements or trading volumes—and groups them into clusters where points are densely packed. It operates based on two key parameters: Eps (epsilon), which defines the radius around a point to consider neighboring points, and MinPts (minimum points), the minimum number of neighboring points needed to form a cluster.
The process begins by selecting an unvisited data point. If this point has at least MinPts within its Eps-neighborhood, it becomes a core point and initiates a new cluster. The algorithm then expands this cluster by recursively including all neighboring core points and their neighbors that meet the density criteria. Points that do not belong to any cluster are labeled as noise or outliers—potential indicators of anomalies.
This approach makes DBSCAN particularly effective at handling noisy financial data because it naturally distinguishes between normal market fluctuations and genuine anomalies without requiring prior knowledge about the number of clusters.
Why Is Detecting Anomalies Important in Cryptocurrency Markets?
Cryptocurrency markets are known for their high volatility and rapid price swings. Identifying abnormal market conditions early can provide traders with critical insights into potential risks or opportunities. For example:
- Market Manipulation: Sudden spikes or drops might indicate pump-and-dump schemes.
- Systemic Risks: Unusual trading volumes could signal systemic issues or impending crashes.
- Fraud Detection: Outlier transactions may reveal fraudulent activities such as wash trading.
By applying algorithms like DBSCAN to historical price data, traders can detect these irregularities more effectively than traditional methods that might overlook subtle but significant deviations.
Recent Advances in Using DBSCAN for Market Analysis
Recent research highlights several innovative applications of DBSCAN within financial analytics:
Cryptocurrency Anomaly Detection: Studies have demonstrated how applying DBSCAN to Bitcoin's price movements helps identify unusual patterns preceding market downturns [1]. These insights enable better risk management strategies.
Real-Time Monitoring Systems: With advancements in computational power, integrating DBSCAN into live monitoring tools allows instant detection of anomalies as they occur [2]. Traders receive timely alerts that inform decision-making processes.
Combining Machine Learning Techniques: Combining density-based clustering with neural networks enhances anomaly detection accuracy [3]. This hybrid approach leverages both pattern recognition capabilities and statistical robustness.
These developments underscore how machine learning integrations make anomaly detection more precise while enabling real-time analysis—a vital feature given cryptocurrency markets' speed and unpredictability.
Key Factors Influencing Effective Use of DBSCAN
While powerful, deploying DBSCAN effectively requires attention to several factors:
Parameter Tuning: Selecting appropriate values for Eps and MinPts is critical; too small Eps may fragment genuine clusters into noise, while too large could merge distinct patterns incorrectly [4][5].
Handling Noisy Data: Financial datasets often contain significant noise due to random fluctuations; thus, understanding how well the algorithm manages false positives is essential [6].
Computational Efficiency: Although generally efficient with O(n log n) complexity [4], large-scale datasets demand optimized implementations for real-time applications.
Validation & Testing: Regular validation ensures that detected anomalies genuinely reflect abnormal conditions rather than false alarms caused by parameter misconfiguration [7].
Challenges & Considerations When Using Density-Based Clustering
Despite its strengths, practitioners should be aware of potential pitfalls:
False Positives: Incorrectly flagging normal market behavior as anomalous can lead to unnecessary trades or panic selling.
Market Volatility: Cryptocurrency prices are inherently volatile; distinguishing between regular swings and true anomalies requires careful calibration.
Regulatory Implications: As anomaly detection influences trading decisions significantly—sometimes automatically—it’s vital these systems comply with relevant regulations concerning transparency and fairness [8][9].
Incorporating robust validation procedures alongside advanced algorithms like DBSCAN helps mitigate these issues while enhancing trustworthiness in automated analysis systems.
By leveraging density-based clustering techniques such as DBSCAN within cryptocurrency markets’ dynamic environment—and combining them with machine learning enhancements—traders gain a sophisticated method for detecting early signs of abnormal activity. Proper parameter tuning combined with ongoing validation ensures reliable performance amid high volatility levels typical of digital assets today.
References
- "Anomaly Detection in Bitcoin Price Movements Using DBSCAN" (2023) - Journal of Financial Data Science
- "Real-Time Anomaly Detection in Cryptocurrency Markets Using Dbscan" (2024) - International Journal of Financial Engineering
- "Enhancing Anomaly Detection in Cryptocurrency Markets with Dbscan and Neural Networks" (2024) - IEEE Transactions on Neural Networks & Learning Systems
4."Time Complexity Analysis of Dbscan" (2019) - Journal Of Algorithms
5."Optimal Parameter Selection For Dbscan In Financial Data" (2022) - Journal Of Data Science
6."Noise Handling In Dbscan For Financial Data Analysis" (2021) - International Journal Of Data Mining And Bioinformatics
7."False Positive Reduction In Anomaly Detection Using Dbscan" (2023) - Journal Of Artificial Intelligence Research
8."Regulatory Compliance For Anomaly Detection Systems In Financial Markets" (2023) - Journal Of Financial Regulation


JCUSER-IC8sJL1q
2025-05-09 23:09
What is DBSCAN and how does it identify unusual market conditions?
What Is DBSCAN and How Does It Detect Unusual Market Conditions?
Understanding how financial markets, especially volatile ones like cryptocurrencies, can be monitored for anomalies is crucial for traders, analysts, and regulators alike. One powerful tool gaining traction in this space is DBSCAN—short for Density-Based Spatial Clustering of Applications with Noise. This clustering algorithm helps identify unusual patterns or outliers in complex datasets by grouping similar data points together based on their density.
How Does DBSCAN Work?
At its core, DBSCAN analyzes data points—such as price movements or trading volumes—and groups them into clusters where points are densely packed. It operates based on two key parameters: Eps (epsilon), which defines the radius around a point to consider neighboring points, and MinPts (minimum points), the minimum number of neighboring points needed to form a cluster.
The process begins by selecting an unvisited data point. If this point has at least MinPts within its Eps-neighborhood, it becomes a core point and initiates a new cluster. The algorithm then expands this cluster by recursively including all neighboring core points and their neighbors that meet the density criteria. Points that do not belong to any cluster are labeled as noise or outliers—potential indicators of anomalies.
This approach makes DBSCAN particularly effective at handling noisy financial data because it naturally distinguishes between normal market fluctuations and genuine anomalies without requiring prior knowledge about the number of clusters.
Why Is Detecting Anomalies Important in Cryptocurrency Markets?
Cryptocurrency markets are known for their high volatility and rapid price swings. Identifying abnormal market conditions early can provide traders with critical insights into potential risks or opportunities. For example:
- Market Manipulation: Sudden spikes or drops might indicate pump-and-dump schemes.
- Systemic Risks: Unusual trading volumes could signal systemic issues or impending crashes.
- Fraud Detection: Outlier transactions may reveal fraudulent activities such as wash trading.
By applying algorithms like DBSCAN to historical price data, traders can detect these irregularities more effectively than traditional methods that might overlook subtle but significant deviations.
Recent Advances in Using DBSCAN for Market Analysis
Recent research highlights several innovative applications of DBSCAN within financial analytics:
Cryptocurrency Anomaly Detection: Studies have demonstrated how applying DBSCAN to Bitcoin's price movements helps identify unusual patterns preceding market downturns [1]. These insights enable better risk management strategies.
Real-Time Monitoring Systems: With advancements in computational power, integrating DBSCAN into live monitoring tools allows instant detection of anomalies as they occur [2]. Traders receive timely alerts that inform decision-making processes.
Combining Machine Learning Techniques: Combining density-based clustering with neural networks enhances anomaly detection accuracy [3]. This hybrid approach leverages both pattern recognition capabilities and statistical robustness.
These developments underscore how machine learning integrations make anomaly detection more precise while enabling real-time analysis—a vital feature given cryptocurrency markets' speed and unpredictability.
Key Factors Influencing Effective Use of DBSCAN
While powerful, deploying DBSCAN effectively requires attention to several factors:
Parameter Tuning: Selecting appropriate values for Eps and MinPts is critical; too small Eps may fragment genuine clusters into noise, while too large could merge distinct patterns incorrectly [4][5].
Handling Noisy Data: Financial datasets often contain significant noise due to random fluctuations; thus, understanding how well the algorithm manages false positives is essential [6].
Computational Efficiency: Although generally efficient with O(n log n) complexity [4], large-scale datasets demand optimized implementations for real-time applications.
Validation & Testing: Regular validation ensures that detected anomalies genuinely reflect abnormal conditions rather than false alarms caused by parameter misconfiguration [7].
Challenges & Considerations When Using Density-Based Clustering
Despite its strengths, practitioners should be aware of potential pitfalls:
False Positives: Incorrectly flagging normal market behavior as anomalous can lead to unnecessary trades or panic selling.
Market Volatility: Cryptocurrency prices are inherently volatile; distinguishing between regular swings and true anomalies requires careful calibration.
Regulatory Implications: As anomaly detection influences trading decisions significantly—sometimes automatically—it’s vital these systems comply with relevant regulations concerning transparency and fairness [8][9].
Incorporating robust validation procedures alongside advanced algorithms like DBSCAN helps mitigate these issues while enhancing trustworthiness in automated analysis systems.
By leveraging density-based clustering techniques such as DBSCAN within cryptocurrency markets’ dynamic environment—and combining them with machine learning enhancements—traders gain a sophisticated method for detecting early signs of abnormal activity. Proper parameter tuning combined with ongoing validation ensures reliable performance amid high volatility levels typical of digital assets today.
References
- "Anomaly Detection in Bitcoin Price Movements Using DBSCAN" (2023) - Journal of Financial Data Science
- "Real-Time Anomaly Detection in Cryptocurrency Markets Using Dbscan" (2024) - International Journal of Financial Engineering
- "Enhancing Anomaly Detection in Cryptocurrency Markets with Dbscan and Neural Networks" (2024) - IEEE Transactions on Neural Networks & Learning Systems
4."Time Complexity Analysis of Dbscan" (2019) - Journal Of Algorithms
5."Optimal Parameter Selection For Dbscan In Financial Data" (2022) - Journal Of Data Science
6."Noise Handling In Dbscan For Financial Data Analysis" (2021) - International Journal Of Data Mining And Bioinformatics
7."False Positive Reduction In Anomaly Detection Using Dbscan" (2023) - Journal Of Artificial Intelligence Research
8."Regulatory Compliance For Anomaly Detection Systems In Financial Markets" (2023) - Journal Of Financial Regulation
Disclaimer:Contains third-party content. Not financial advice.
See Terms and Conditions.
🚀 Want to grab the opportunity early? Try #JuCoinOnChain!
✅ Faster order matching
✅ More flexibility
✅ Focus on new projects & assets early
✅ Trade directly with JuCoin account – no external wallet needed
👉 Discover now: https://jucoin.com/en/onchain
👉 Register for JuCoin now: https://bit.ly/3BVxlZ2
#JuCoin #JuCoinVietnam #JuCoinOnChain #Crypto #Blockchain #DeFi #Web3 #CryptoCommunity


Lee Jucoin
2025-08-21 07:56
🚀 Want to grab the opportunity early?
Disclaimer:Contains third-party content. Not financial advice.
See Terms and Conditions.
It's never been easy to crack how to become a millionaire, but it seems like there's finally a way... Check out our YouTube Channel 👉


JuCoin Media
2025-08-11 13:20
How to Become A Millionaire - Dump First, Dance Later 💰
Disclaimer:Contains third-party content. Not financial advice.
See Terms and Conditions.
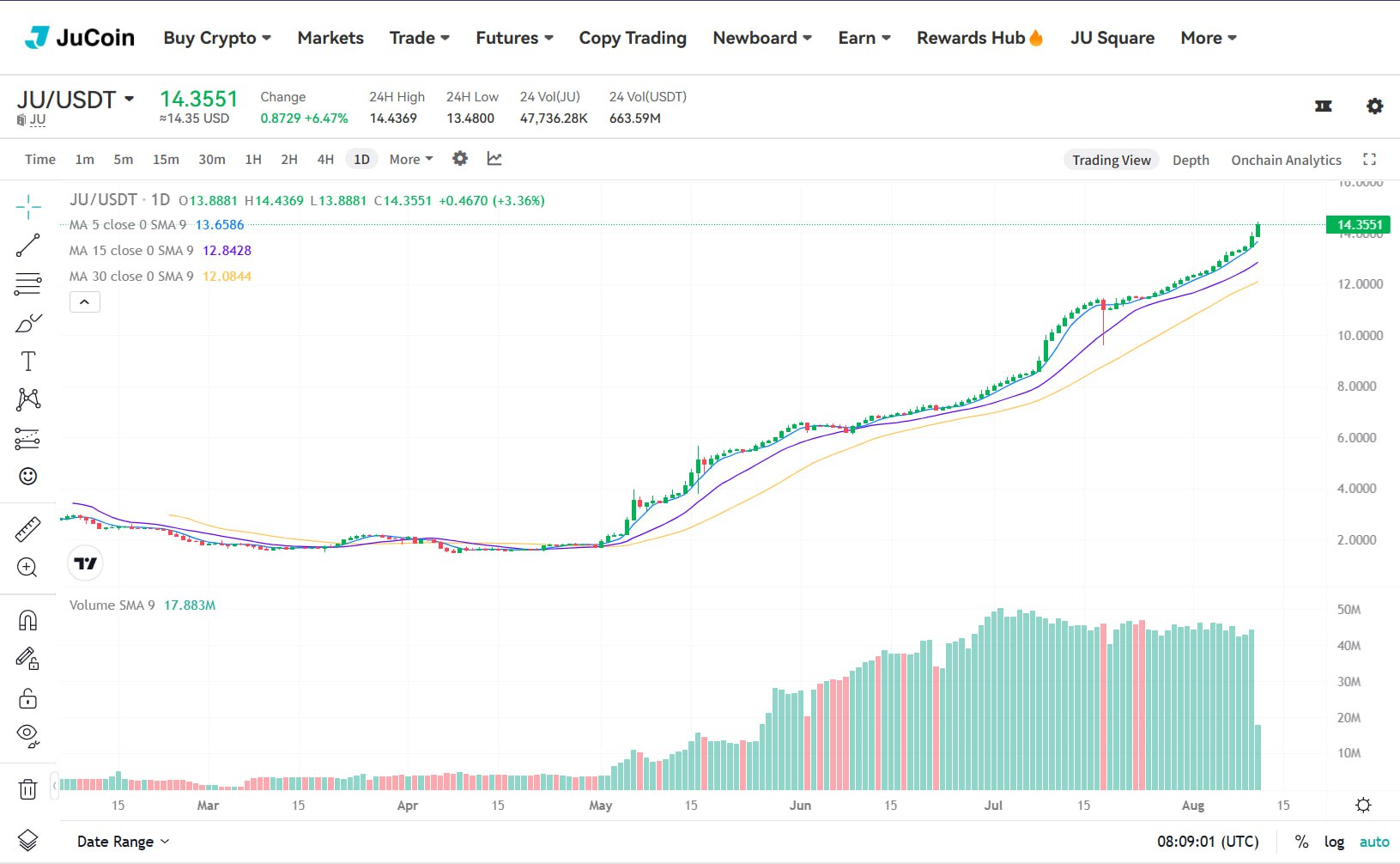
+140x ROI depuis le lancement — du jamais vu dans le marché actuel. Merci à tous les builders, holders & believers Le sommet ? Ce n’est que le départ. Jusqu’au 12 août, 19h00 (UTC+8)


Carmelita
2025-08-11 21:33
$JU explose un nouveau record : 14 $ franchis !
Disclaimer:Contains third-party content. Not financial advice.
See Terms and Conditions.
Environmental Concerns Surrounding NFT Minting and Trading
NFTs, or Non-Fungible Tokens, have revolutionized the digital landscape by enabling artists, collectors, and gamers to buy, sell, and showcase unique digital assets. While their popularity continues to soar, growing awareness of their environmental impact has sparked significant concern among industry stakeholders and consumers alike. This article explores the key environmental issues associated with NFT minting and trading, recent developments addressing these challenges, and what the future might hold for sustainable digital assets.
What Are NFTs and How Are They Created?
NFTs are blockchain-based tokens that certify ownership of a specific digital item—be it artwork, music, in-game items, or even real-world assets. Unlike cryptocurrencies such as Bitcoin or Ethereum that are interchangeable (fungible), NFTs are unique (non-fungible), making them ideal for representing scarce or one-of-a-kind items.
The process of creating an NFT is called minting. It involves recording a new token on a blockchain network through complex computational processes that validate ownership rights. Most NFTs are minted on platforms using blockchain protocols like Ethereum’s Proof of Work (PoW) consensus algorithm—a method requiring substantial computational power to verify transactions.
The Environmental Impact of NFT Minting
One of the primary concerns surrounding NFTs is their high energy consumption during minting and trading activities. Blockchain networks utilizing PoW require miners to solve intricate mathematical puzzles—an activity that demands significant electricity input. For example:
- Energy-intensive validation: Each transaction on Ethereum can consume as much energy as powering an average household for several days.
- Carbon footprint: Studies estimate that a single Ethereum transaction can produce approximately 1.3 kilograms of CO2 emissions—a figure comparable to driving a car over several miles.
Given the frequency of transactions in popular markets—often thousands daily—the cumulative environmental impact becomes substantial. This extensive energy use predominantly relies on non-renewable sources such as coal-fired power plants in regions where electricity generation depends heavily on fossil fuels.
Resource Depletion from Fossil Fuel Extraction
The reliance on fossil fuels not only contributes directly to greenhouse gas emissions but also leads to resource depletion through extraction activities like mining coal or natural gas drilling. These processes cause habitat destruction and pollution while accelerating climate change.
Efforts Toward Sustainable NFT Practices
Recognizing these issues has prompted various initiatives aimed at reducing the ecological footprint associated with NFTs:
Transition from Proof of Work to Proof of Stake
Many blockchain networks are shifting away from PoW toward more sustainable consensus mechanisms like Proof of Stake (PoS). Unlike PoW miners who compete using computational power—and thus high energy consumption—PoS validators are chosen based on how many tokens they stake as collateral:
- Ethereum's transition: The Ethereum network announced plans in 2022 to migrate from PoW to PoS via its upgrade known as "Ethereum 2.0." This move aims for up to 99% reduction in energy use.
Adoption of Eco-Friendly Blockchains
Newer platforms such as Solana and Polkadot employ alternative consensus algorithms like Proof of Capacity (PoC) or other innovative methods requiring less electrical power:
- Solana: Uses proof-of-history combined with proof-of-stake for fast transactions with minimal energy requirements.
- Polkadot: Implements Nominated Proof-of-Stake (NPoS), which is designed for scalability while maintaining sustainability.
Carbon Offset Initiatives by Marketplaces & Creators
Some marketplaces actively promote carbon neutrality by investing in renewable energy projects or reforestation programs aimed at offsetting emissions generated during minting:
- Platforms may purchase carbon credits equivalent to their transaction volume.
- Artists sometimes choose eco-friendly blockchains intentionally when creating NFTs.
Regulatory Developments Addressing Environmental Concerns
Governments worldwide have started paying closer attention due to mounting evidence about crypto-related environmental impacts:
- The European Union proposed regulations targeting transparency around crypto mining’s carbon footprint.
- Some jurisdictions consider taxing high-energy-consuming activities related to blockchain operations.
These regulatory efforts aim not only at curbing excessive emissions but also at encouraging innovation toward greener solutions within the industry.
Industry Response: Moving Toward Sustainability
The NFT ecosystem is increasingly embracing sustainability practices driven by consumer demand for environmentally responsible options:
- Marketplaces now highlight “green” NFTs minted via eco-friendly blockchains.
- Creators are encouraged—or required—to disclose information about their project's environmental impact.
This shift fosters greater accountability among participants while promoting technological advancements focused on reducing ecological damage linked with digital asset creation.
Public Awareness & Consumer Behavior Changes
Educational campaigns play an essential role in informing users about how certain popular NFTs contribute significantly toward climate change due to high-energy consumption involved during minting processes:
- Highlighted cases show some high-profile sales generating large amounts of CO2 emissions.
- Consumers increasingly prefer supporting projects committed explicitly toward sustainability goals.
As awareness grows globally regarding climate issues tied directly—or indirectly—to digital asset markets—including NFTs—it influences buying decisions favorably towards more environmentally conscious options.
Future Outlook: Navigating Sustainability Challenges
While technological innovations offer promising pathways forward—including greener blockchains—the full transition remains complex:
Continued development will be necessary across all layers—from hardware efficiency improvements used by miners/validators—to broader systemic shifts involving policy changes incentivizing low-impact practices.
Increased adoption could lead market demand favoring “eco-friendly” NFTs over traditional ones—potentially transforming industry standards altogether.
Stricter regulations might impose penalties or taxes related specifically targeting high-energy-consuming activities within crypto ecosystems; this could accelerate innovation towards sustainable alternatives.
Final Thoughts: Balancing Innovation With Responsibility
NFTs symbolize remarkable progress within digital ownership realms but come with notable environmental costs if unaddressed properly. Industry stakeholders—including developers, creators, investors—and consumers must prioritize sustainable practices alongside technological advancement if they aim for long-term growth without compromising planetary health.
By fostering transparency around ecological impacts—and supporting innovations geared toward reducing carbon footprints—the community can help ensure that this exciting frontier evolves responsibly while minimizing its adverse effects on our environment.
Key Takeaways
- Energy-intensive processes underpin most current NFT minting methods due primarily to reliance on PoW-based blockchains like Ethereum.*
- Transition efforts such as moving towards proof-of-stake models significantly reduce associated carbon footprints.*
- Emerging eco-friendly platforms demonstrate promising alternatives capable of supporting scalable NFT markets sustainably.*
- Regulatory measures coupled with increased public awareness will likely shape future industry standards.*


JCUSER-WVMdslBw
2025-05-22 23:31
What environmental concerns surround NFT minting and trading?
Environmental Concerns Surrounding NFT Minting and Trading
NFTs, or Non-Fungible Tokens, have revolutionized the digital landscape by enabling artists, collectors, and gamers to buy, sell, and showcase unique digital assets. While their popularity continues to soar, growing awareness of their environmental impact has sparked significant concern among industry stakeholders and consumers alike. This article explores the key environmental issues associated with NFT minting and trading, recent developments addressing these challenges, and what the future might hold for sustainable digital assets.
What Are NFTs and How Are They Created?
NFTs are blockchain-based tokens that certify ownership of a specific digital item—be it artwork, music, in-game items, or even real-world assets. Unlike cryptocurrencies such as Bitcoin or Ethereum that are interchangeable (fungible), NFTs are unique (non-fungible), making them ideal for representing scarce or one-of-a-kind items.
The process of creating an NFT is called minting. It involves recording a new token on a blockchain network through complex computational processes that validate ownership rights. Most NFTs are minted on platforms using blockchain protocols like Ethereum’s Proof of Work (PoW) consensus algorithm—a method requiring substantial computational power to verify transactions.
The Environmental Impact of NFT Minting
One of the primary concerns surrounding NFTs is their high energy consumption during minting and trading activities. Blockchain networks utilizing PoW require miners to solve intricate mathematical puzzles—an activity that demands significant electricity input. For example:
- Energy-intensive validation: Each transaction on Ethereum can consume as much energy as powering an average household for several days.
- Carbon footprint: Studies estimate that a single Ethereum transaction can produce approximately 1.3 kilograms of CO2 emissions—a figure comparable to driving a car over several miles.
Given the frequency of transactions in popular markets—often thousands daily—the cumulative environmental impact becomes substantial. This extensive energy use predominantly relies on non-renewable sources such as coal-fired power plants in regions where electricity generation depends heavily on fossil fuels.
Resource Depletion from Fossil Fuel Extraction
The reliance on fossil fuels not only contributes directly to greenhouse gas emissions but also leads to resource depletion through extraction activities like mining coal or natural gas drilling. These processes cause habitat destruction and pollution while accelerating climate change.
Efforts Toward Sustainable NFT Practices
Recognizing these issues has prompted various initiatives aimed at reducing the ecological footprint associated with NFTs:
Transition from Proof of Work to Proof of Stake
Many blockchain networks are shifting away from PoW toward more sustainable consensus mechanisms like Proof of Stake (PoS). Unlike PoW miners who compete using computational power—and thus high energy consumption—PoS validators are chosen based on how many tokens they stake as collateral:
- Ethereum's transition: The Ethereum network announced plans in 2022 to migrate from PoW to PoS via its upgrade known as "Ethereum 2.0." This move aims for up to 99% reduction in energy use.
Adoption of Eco-Friendly Blockchains
Newer platforms such as Solana and Polkadot employ alternative consensus algorithms like Proof of Capacity (PoC) or other innovative methods requiring less electrical power:
- Solana: Uses proof-of-history combined with proof-of-stake for fast transactions with minimal energy requirements.
- Polkadot: Implements Nominated Proof-of-Stake (NPoS), which is designed for scalability while maintaining sustainability.
Carbon Offset Initiatives by Marketplaces & Creators
Some marketplaces actively promote carbon neutrality by investing in renewable energy projects or reforestation programs aimed at offsetting emissions generated during minting:
- Platforms may purchase carbon credits equivalent to their transaction volume.
- Artists sometimes choose eco-friendly blockchains intentionally when creating NFTs.
Regulatory Developments Addressing Environmental Concerns
Governments worldwide have started paying closer attention due to mounting evidence about crypto-related environmental impacts:
- The European Union proposed regulations targeting transparency around crypto mining’s carbon footprint.
- Some jurisdictions consider taxing high-energy-consuming activities related to blockchain operations.
These regulatory efforts aim not only at curbing excessive emissions but also at encouraging innovation toward greener solutions within the industry.
Industry Response: Moving Toward Sustainability
The NFT ecosystem is increasingly embracing sustainability practices driven by consumer demand for environmentally responsible options:
- Marketplaces now highlight “green” NFTs minted via eco-friendly blockchains.
- Creators are encouraged—or required—to disclose information about their project's environmental impact.
This shift fosters greater accountability among participants while promoting technological advancements focused on reducing ecological damage linked with digital asset creation.
Public Awareness & Consumer Behavior Changes
Educational campaigns play an essential role in informing users about how certain popular NFTs contribute significantly toward climate change due to high-energy consumption involved during minting processes:
- Highlighted cases show some high-profile sales generating large amounts of CO2 emissions.
- Consumers increasingly prefer supporting projects committed explicitly toward sustainability goals.
As awareness grows globally regarding climate issues tied directly—or indirectly—to digital asset markets—including NFTs—it influences buying decisions favorably towards more environmentally conscious options.
Future Outlook: Navigating Sustainability Challenges
While technological innovations offer promising pathways forward—including greener blockchains—the full transition remains complex:
Continued development will be necessary across all layers—from hardware efficiency improvements used by miners/validators—to broader systemic shifts involving policy changes incentivizing low-impact practices.
Increased adoption could lead market demand favoring “eco-friendly” NFTs over traditional ones—potentially transforming industry standards altogether.
Stricter regulations might impose penalties or taxes related specifically targeting high-energy-consuming activities within crypto ecosystems; this could accelerate innovation towards sustainable alternatives.
Final Thoughts: Balancing Innovation With Responsibility
NFTs symbolize remarkable progress within digital ownership realms but come with notable environmental costs if unaddressed properly. Industry stakeholders—including developers, creators, investors—and consumers must prioritize sustainable practices alongside technological advancement if they aim for long-term growth without compromising planetary health.
By fostering transparency around ecological impacts—and supporting innovations geared toward reducing carbon footprints—the community can help ensure that this exciting frontier evolves responsibly while minimizing its adverse effects on our environment.
Key Takeaways
- Energy-intensive processes underpin most current NFT minting methods due primarily to reliance on PoW-based blockchains like Ethereum.*
- Transition efforts such as moving towards proof-of-stake models significantly reduce associated carbon footprints.*
- Emerging eco-friendly platforms demonstrate promising alternatives capable of supporting scalable NFT markets sustainably.*
- Regulatory measures coupled with increased public awareness will likely shape future industry standards.*
Disclaimer:Contains third-party content. Not financial advice.
See Terms and Conditions.
What Is Proof-of-Stake (PoS)?
Proof-of-Stake (PoS) is a consensus mechanism used in blockchain technology to validate transactions and secure the network. Unlike the traditional Proof-of-Work (PoW), which relies on miners solving complex mathematical puzzles through energy-intensive computations, PoS selects validators based on the amount of cryptocurrency they "stake" or lock up as collateral. This approach aims to create a more efficient, scalable, and environmentally friendly way of maintaining blockchain integrity.
How Does Proof-of-Stake Work?
In a PoS system, participants known as validators are chosen to create new blocks based on their stake in the network. The more coins a validator commits, the higher their chances of being selected to validate transactions and add new blocks to the chain. This process involves several key steps:
- Staking: Validators lock up a specific amount of cryptocurrency as collateral.
- Validator Selection: The network randomly or deterministically selects validators based on factors like stake size and sometimes other criteria such as coin age.
- Validation: Selected validators verify transactions within proposed blocks.
- Reward & Penalties: Successful validation earns rewards; misbehavior results in penalties like slashing—where part or all of their staked coins are forfeited.
This method ensures that those with more at stake have greater incentive to act honestly since malicious activity can lead to significant financial loss.
Advantages of Proof-of-Stake
Proof-of-Stake offers several benefits over traditional PoW systems:
Energy Efficiency
One of PoS's most significant advantages is its lower energy consumption. Since it eliminates the need for computationally intensive mining operations, it reduces electricity usage drastically—making blockchain networks more sustainable and environmentally friendly.
Scalability
PoS allows for faster transaction processing times and higher throughput compared to PoW networks. This scalability makes it suitable for applications requiring high-speed data validation without compromising security.
Security Features
While no system is entirely immune from attacks, well-designed PoS protocols incorporate mechanisms like slashing penalties that discourage malicious behavior. Additionally, because validators risk losing their staked assets if they act dishonestly, this creates economic incentives aligned with honest participation.
Challenges & Risks Associated With Proof-of-Stake
Despite its advantages, PoS faces certain challenges that developers and stakeholders must address:
Nothing-at-Stake Problem
In some early implementations of PoS, validators could vote for multiple conflicting chains without penalty—a situation called "nothing-at-stake." To mitigate this risk, modern protocols implement slashing conditions where misbehavior leads to penalties severe enough to deter such actions.
Centralization Concerns
Since larger stakeholders have increased influence over block creation probabilities, there's potential for wealth concentration leading to centralization risks—where power becomes concentrated among few large holders rather than distributed evenly across participants.
Security Considerations
Although generally considered secure when properly implemented, emerging attack vectors specific to staking systems require ongoing research and protocol improvements. Continuous updates help maintain resilience against threats like long-range attacks or validator collusion.
Ethereum’s Transition From Proof-of-Work To Proof-of-Stake
Ethereum’s move from proof-of-work (PoW) toward proof-of-stake (PoS) represents one of the most prominent real-world applications demonstrating this consensus mechanism's potential. Launched initially in December 2020 via its Beacon Chain upgrade—the first phase towards Ethereum 2.0—the transition aimed at addressing scalability issues while significantly reducing energy consumption associated with mining activities.
The milestone event called "The Merge," completed in 2023 after years of development effort by Ethereum developers worldwide—including extensive testing—marked Ethereum’s full switch from energy-intensive mining toward an eco-friendly staking model. This shift not only enhances sustainability but also paves the way for future upgrades focused on increasing transaction throughput through sharding techniques integrated into Eth2 architecture.
Future Outlook & Adoption Trends
As major cryptocurrencies adopt proof-of-stake mechanisms—including Cardano (ADA), Solana (SOL), Polkadot (DOT), among others—the landscape is witnessing rapid growth driven by both technological advancements and environmental considerations. Stakeholder interest continues rising due primarily to benefits like reduced operational costs and improved scalability prospects which appeal both investors seeking returns via staking rewards—and developers aiming for robust decentralized applications capable of handling mass adoption scenarios efficiently.
However, widespread adoption also brings regulatory scrutiny; authorities worldwide are beginning scrutinizing staking practices concerning investor protections and compliance frameworks—a factor that could influence future development directions within this space significantly.
Key Takeaways About Proof-of-Stake
To summarize what makes proof-of-stake distinct:
- Validators participate by locking up tokens instead of performing resource-heavy computations.
- It offers superior energy efficiency compared with proof-of-work.
- Security relies heavily on economic incentives; misbehavior results in financial penalties.
- Major networks like Ethereum have successfully transitioned or plan transitions towards PoS models.
Understanding these core aspects helps users evaluate whether adopting or supporting proof-based blockchain projects aligns with their goals—whether it's investing safely or developing scalable decentralized solutions.
Addressing User Concerns & Trustworthiness
For users considering involvement in staking activities—or simply wanting clarity about how these systems operate—it’s crucial first understanding security measures involved such as slashing conditions designed specifically against malicious actions—and how decentralization efforts aim at preventing undue influence by large stakeholders alone.
Furthermore,
- Look into reputable platforms offering staking services,
- Review governance structures ensuring transparency,
- Stay updated about ongoing protocol improvements addressing vulnerabilities,
are essential steps toward engaging confidently within evolving proof-based ecosystems.
Final Thoughts
Proof-of-stake has emerged as an innovative alternative that addresses many limitations inherent in traditional blockchain consensus mechanisms while promoting sustainability through reduced energy use—and fostering scalability necessary for mainstream adoption today’s digital economy demands increasingly efficient infrastructure solutions rooted firmly in trustworthiness backed by transparent governance models.


JCUSER-WVMdslBw
2025-05-11 10:39
What is proof-of-stake?
What Is Proof-of-Stake (PoS)?
Proof-of-Stake (PoS) is a consensus mechanism used in blockchain technology to validate transactions and secure the network. Unlike the traditional Proof-of-Work (PoW), which relies on miners solving complex mathematical puzzles through energy-intensive computations, PoS selects validators based on the amount of cryptocurrency they "stake" or lock up as collateral. This approach aims to create a more efficient, scalable, and environmentally friendly way of maintaining blockchain integrity.
How Does Proof-of-Stake Work?
In a PoS system, participants known as validators are chosen to create new blocks based on their stake in the network. The more coins a validator commits, the higher their chances of being selected to validate transactions and add new blocks to the chain. This process involves several key steps:
- Staking: Validators lock up a specific amount of cryptocurrency as collateral.
- Validator Selection: The network randomly or deterministically selects validators based on factors like stake size and sometimes other criteria such as coin age.
- Validation: Selected validators verify transactions within proposed blocks.
- Reward & Penalties: Successful validation earns rewards; misbehavior results in penalties like slashing—where part or all of their staked coins are forfeited.
This method ensures that those with more at stake have greater incentive to act honestly since malicious activity can lead to significant financial loss.
Advantages of Proof-of-Stake
Proof-of-Stake offers several benefits over traditional PoW systems:
Energy Efficiency
One of PoS's most significant advantages is its lower energy consumption. Since it eliminates the need for computationally intensive mining operations, it reduces electricity usage drastically—making blockchain networks more sustainable and environmentally friendly.
Scalability
PoS allows for faster transaction processing times and higher throughput compared to PoW networks. This scalability makes it suitable for applications requiring high-speed data validation without compromising security.
Security Features
While no system is entirely immune from attacks, well-designed PoS protocols incorporate mechanisms like slashing penalties that discourage malicious behavior. Additionally, because validators risk losing their staked assets if they act dishonestly, this creates economic incentives aligned with honest participation.
Challenges & Risks Associated With Proof-of-Stake
Despite its advantages, PoS faces certain challenges that developers and stakeholders must address:
Nothing-at-Stake Problem
In some early implementations of PoS, validators could vote for multiple conflicting chains without penalty—a situation called "nothing-at-stake." To mitigate this risk, modern protocols implement slashing conditions where misbehavior leads to penalties severe enough to deter such actions.
Centralization Concerns
Since larger stakeholders have increased influence over block creation probabilities, there's potential for wealth concentration leading to centralization risks—where power becomes concentrated among few large holders rather than distributed evenly across participants.
Security Considerations
Although generally considered secure when properly implemented, emerging attack vectors specific to staking systems require ongoing research and protocol improvements. Continuous updates help maintain resilience against threats like long-range attacks or validator collusion.
Ethereum’s Transition From Proof-of-Work To Proof-of-Stake
Ethereum’s move from proof-of-work (PoW) toward proof-of-stake (PoS) represents one of the most prominent real-world applications demonstrating this consensus mechanism's potential. Launched initially in December 2020 via its Beacon Chain upgrade—the first phase towards Ethereum 2.0—the transition aimed at addressing scalability issues while significantly reducing energy consumption associated with mining activities.
The milestone event called "The Merge," completed in 2023 after years of development effort by Ethereum developers worldwide—including extensive testing—marked Ethereum’s full switch from energy-intensive mining toward an eco-friendly staking model. This shift not only enhances sustainability but also paves the way for future upgrades focused on increasing transaction throughput through sharding techniques integrated into Eth2 architecture.
Future Outlook & Adoption Trends
As major cryptocurrencies adopt proof-of-stake mechanisms—including Cardano (ADA), Solana (SOL), Polkadot (DOT), among others—the landscape is witnessing rapid growth driven by both technological advancements and environmental considerations. Stakeholder interest continues rising due primarily to benefits like reduced operational costs and improved scalability prospects which appeal both investors seeking returns via staking rewards—and developers aiming for robust decentralized applications capable of handling mass adoption scenarios efficiently.
However, widespread adoption also brings regulatory scrutiny; authorities worldwide are beginning scrutinizing staking practices concerning investor protections and compliance frameworks—a factor that could influence future development directions within this space significantly.
Key Takeaways About Proof-of-Stake
To summarize what makes proof-of-stake distinct:
- Validators participate by locking up tokens instead of performing resource-heavy computations.
- It offers superior energy efficiency compared with proof-of-work.
- Security relies heavily on economic incentives; misbehavior results in financial penalties.
- Major networks like Ethereum have successfully transitioned or plan transitions towards PoS models.
Understanding these core aspects helps users evaluate whether adopting or supporting proof-based blockchain projects aligns with their goals—whether it's investing safely or developing scalable decentralized solutions.
Addressing User Concerns & Trustworthiness
For users considering involvement in staking activities—or simply wanting clarity about how these systems operate—it’s crucial first understanding security measures involved such as slashing conditions designed specifically against malicious actions—and how decentralization efforts aim at preventing undue influence by large stakeholders alone.
Furthermore,
- Look into reputable platforms offering staking services,
- Review governance structures ensuring transparency,
- Stay updated about ongoing protocol improvements addressing vulnerabilities,
are essential steps toward engaging confidently within evolving proof-based ecosystems.
Final Thoughts
Proof-of-stake has emerged as an innovative alternative that addresses many limitations inherent in traditional blockchain consensus mechanisms while promoting sustainability through reduced energy use—and fostering scalability necessary for mainstream adoption today’s digital economy demands increasingly efficient infrastructure solutions rooted firmly in trustworthiness backed by transparent governance models.
Disclaimer:Contains third-party content. Not financial advice.
See Terms and Conditions.
How Can Gap Strategies Be Optimized for Earnings Gaps?
Understanding Gap Strategies in Financial Markets
Gap strategies are a set of trading techniques designed to exploit price discrepancies, or "gaps," that occur between the previous closing price and the current market price. These gaps often emerge during significant market events, especially around earnings announcements when companies release their quarterly or annual financial results. Investors and traders leverage these gaps to generate profits by predicting whether prices will continue in the direction of the initial move or revert back.
Earnings Announcements as Catalysts for Price Gaps
Earnings reports are among the most influential catalysts for market gaps. When a company releases its earnings, it provides critical insights into its financial health, profitability, and future outlook. If actual results surpass expectations—known as an earnings surprise—the stock may gap higher; if they fall short, it might gap lower. These sudden movements can be swift and substantial due to investor reactions to new information.
To capitalize on these movements effectively, traders analyze historical patterns of how stocks react post-earnings and monitor upcoming reports closely. The key is identifying whether a gap signifies a genuine trend continuation or an overreaction that could reverse.
Technical Analysis Tools for Gap Identification
Technical analysis plays a vital role in optimizing gap strategies. Several indicators help traders spot potential gaps before they happen or confirm their presence once they occur:
- Bollinger Bands: Measure volatility; widening bands can signal increased likelihood of price gaps.
- Moving Averages: Help identify trend directions; crossing points may precede significant moves.
- Relative Strength Index (RSI): Indicates overbought or oversold conditions that could lead to reversals following a gap.
By combining these tools with candlestick patterns and volume analysis, investors can improve their chances of entering trades at optimal points relative to earnings-driven gaps.
Leveraging Quantitative Models and Data Analytics
Beyond traditional technical indicators, advanced quantitative models enhance prediction accuracy regarding earnings gaps:
- Regression Analysis: Examines historical relationships between financial metrics and stock movements.
- Machine Learning Algorithms: Use vast datasets—including sentiment analysis from news sources—to forecast potential price jumps around earnings dates.
These models require robust data inputs but offer significant advantages by providing probabilistic assessments rather than relying solely on subjective interpretation.
Risk Management Techniques in Gap Trading
While opportunities abound with gap strategies, managing risk remains paramount due to inherent volatility:
- Stop-Loss Orders: Limit potential losses if the trade moves against expectations.
- Hedging Strategies: Use options like puts or calls to protect positions during volatile periods.
Implementing disciplined risk controls ensures that investors do not suffer disproportionate losses from unpredictable market swings following earnings releases.
Recent Technological Advancements Enhancing Gap Strategy Optimization
The landscape of trading has evolved dramatically with technological innovations:
- Algorithmic Trading Systems: Automate real-time detection of potential gaps based on predefined criteria—speeding up decision-making processes significantly.
- Big Data Analytics: Aggregate vast amounts of financial news, social media sentiment, economic indicators—all contributing factors influencing earning surprises—and incorporate them into predictive models.
- Artificial Intelligence (AI): Continually learn from new data streams to refine predictions about when and how large an earning-related gap might be.
These advancements have made it possible for both institutional investors and retail traders alike to implement more precise timing strategies around earning events.
Potential Risks Associated With Gap Strategies
Despite technological progress improving prediction capabilities, risks persist:
Market Volatility — Frequent large gaps can increase overall market turbulence which might deter conservative investors but attract high-risk traders seeking quick gains.
Information Asymmetry — Not all participants have access to equally timely information; insider trading remains illegal but highlights disparities that can influence pricing anomalies during earnings seasons.
Systemic Risks — Overreliance on similar algorithms across multiple players could amplify systemic instability if many execute similar trades simultaneously during volatile periods like post-earnings announcements.
Staying Informed About Regulatory Changes & Market Trends
Regulatory environments continually evolve—particularly within cryptocurrency markets where recent policy shifts have led to increased volatility—and impact how effectively traders can deploy gap strategies safely within legal boundaries. Staying updated through reputable sources ensures compliance while maximizing strategic advantage.
Applying Best Practices To Optimize Earnings Gap Strategies
To maximize success when employing gap-based trading tactics around corporate disclosures:
- Conduct thorough fundamental analysis alongside technical signals—understanding why a particular company’s results differ from expectations adds context beyond mere chart patterns.
- Use quantitative tools combined with real-time news monitoring systems—this integrated approach enhances predictive accuracy regarding upcoming earning surprises causing sizable price gaps.
- Implement strict risk management protocols—including stop-loss orders—and avoid overleveraging positions which could magnify losses amid unexpected adverse moves post-announcement.
- Keep abreast of regulatory developments affecting markets you trade—in particular digital assets like cryptocurrencies—to adapt your strategy accordingly.
The Future Outlook for Earnings-Based Gap Trading
As technology continues advancing—with AI becoming more sophisticated—the ability for individual investors as well as institutions will improve further in predicting when substantial earning-related gabs will occur—and how best to profit from them while controlling downside risks effectively.
In summary,
Optimizing gap strategies around earnings involves integrating technical analysis tools with advanced data analytics models while maintaining disciplined risk management practices—all supported by staying informed about evolving regulations and market trends . This comprehensive approach enables smarter decision-making aimed at capitalizing on one of the most dynamic aspects of modern investing—the rapid movement triggered by corporate disclosures.
By continuously refining these methods through technological innovation and rigorous research, investors can better navigate volatile markets driven by quarterly reporting cycles—turning potential pitfalls into profitable opportunities within their investment portfolios


JCUSER-F1IIaxXA
2025-05-09 11:08
How can gap strategies be optimized for earnings gaps?
How Can Gap Strategies Be Optimized for Earnings Gaps?
Understanding Gap Strategies in Financial Markets
Gap strategies are a set of trading techniques designed to exploit price discrepancies, or "gaps," that occur between the previous closing price and the current market price. These gaps often emerge during significant market events, especially around earnings announcements when companies release their quarterly or annual financial results. Investors and traders leverage these gaps to generate profits by predicting whether prices will continue in the direction of the initial move or revert back.
Earnings Announcements as Catalysts for Price Gaps
Earnings reports are among the most influential catalysts for market gaps. When a company releases its earnings, it provides critical insights into its financial health, profitability, and future outlook. If actual results surpass expectations—known as an earnings surprise—the stock may gap higher; if they fall short, it might gap lower. These sudden movements can be swift and substantial due to investor reactions to new information.
To capitalize on these movements effectively, traders analyze historical patterns of how stocks react post-earnings and monitor upcoming reports closely. The key is identifying whether a gap signifies a genuine trend continuation or an overreaction that could reverse.
Technical Analysis Tools for Gap Identification
Technical analysis plays a vital role in optimizing gap strategies. Several indicators help traders spot potential gaps before they happen or confirm their presence once they occur:
- Bollinger Bands: Measure volatility; widening bands can signal increased likelihood of price gaps.
- Moving Averages: Help identify trend directions; crossing points may precede significant moves.
- Relative Strength Index (RSI): Indicates overbought or oversold conditions that could lead to reversals following a gap.
By combining these tools with candlestick patterns and volume analysis, investors can improve their chances of entering trades at optimal points relative to earnings-driven gaps.
Leveraging Quantitative Models and Data Analytics
Beyond traditional technical indicators, advanced quantitative models enhance prediction accuracy regarding earnings gaps:
- Regression Analysis: Examines historical relationships between financial metrics and stock movements.
- Machine Learning Algorithms: Use vast datasets—including sentiment analysis from news sources—to forecast potential price jumps around earnings dates.
These models require robust data inputs but offer significant advantages by providing probabilistic assessments rather than relying solely on subjective interpretation.
Risk Management Techniques in Gap Trading
While opportunities abound with gap strategies, managing risk remains paramount due to inherent volatility:
- Stop-Loss Orders: Limit potential losses if the trade moves against expectations.
- Hedging Strategies: Use options like puts or calls to protect positions during volatile periods.
Implementing disciplined risk controls ensures that investors do not suffer disproportionate losses from unpredictable market swings following earnings releases.
Recent Technological Advancements Enhancing Gap Strategy Optimization
The landscape of trading has evolved dramatically with technological innovations:
- Algorithmic Trading Systems: Automate real-time detection of potential gaps based on predefined criteria—speeding up decision-making processes significantly.
- Big Data Analytics: Aggregate vast amounts of financial news, social media sentiment, economic indicators—all contributing factors influencing earning surprises—and incorporate them into predictive models.
- Artificial Intelligence (AI): Continually learn from new data streams to refine predictions about when and how large an earning-related gap might be.
These advancements have made it possible for both institutional investors and retail traders alike to implement more precise timing strategies around earning events.
Potential Risks Associated With Gap Strategies
Despite technological progress improving prediction capabilities, risks persist:
Market Volatility — Frequent large gaps can increase overall market turbulence which might deter conservative investors but attract high-risk traders seeking quick gains.
Information Asymmetry — Not all participants have access to equally timely information; insider trading remains illegal but highlights disparities that can influence pricing anomalies during earnings seasons.
Systemic Risks — Overreliance on similar algorithms across multiple players could amplify systemic instability if many execute similar trades simultaneously during volatile periods like post-earnings announcements.
Staying Informed About Regulatory Changes & Market Trends
Regulatory environments continually evolve—particularly within cryptocurrency markets where recent policy shifts have led to increased volatility—and impact how effectively traders can deploy gap strategies safely within legal boundaries. Staying updated through reputable sources ensures compliance while maximizing strategic advantage.
Applying Best Practices To Optimize Earnings Gap Strategies
To maximize success when employing gap-based trading tactics around corporate disclosures:
- Conduct thorough fundamental analysis alongside technical signals—understanding why a particular company’s results differ from expectations adds context beyond mere chart patterns.
- Use quantitative tools combined with real-time news monitoring systems—this integrated approach enhances predictive accuracy regarding upcoming earning surprises causing sizable price gaps.
- Implement strict risk management protocols—including stop-loss orders—and avoid overleveraging positions which could magnify losses amid unexpected adverse moves post-announcement.
- Keep abreast of regulatory developments affecting markets you trade—in particular digital assets like cryptocurrencies—to adapt your strategy accordingly.
The Future Outlook for Earnings-Based Gap Trading
As technology continues advancing—with AI becoming more sophisticated—the ability for individual investors as well as institutions will improve further in predicting when substantial earning-related gabs will occur—and how best to profit from them while controlling downside risks effectively.
In summary,
Optimizing gap strategies around earnings involves integrating technical analysis tools with advanced data analytics models while maintaining disciplined risk management practices—all supported by staying informed about evolving regulations and market trends . This comprehensive approach enables smarter decision-making aimed at capitalizing on one of the most dynamic aspects of modern investing—the rapid movement triggered by corporate disclosures.
By continuously refining these methods through technological innovation and rigorous research, investors can better navigate volatile markets driven by quarterly reporting cycles—turning potential pitfalls into profitable opportunities within their investment portfolios
Disclaimer:Contains third-party content. Not financial advice.
See Terms and Conditions.
📣 JuCoin Weekly Report | August 04 – August 10. 📊
💚 5 new tokens listed on Jucoin Spot. 💚 7 new campaigns launched this week. 💚 Platform token $JU up over 31.77% 🚀
👉 Stay with #JuCoin to not miss any updates! 👉Register for JuCoin now: https://bit.ly/3BVxlZ2
💬 Comment the project you want to be listed this week 👇
#Jucoin #JucoinVietnam #JuCoinInsights #JU #WeeklyReport #Crypto #DeFi #Web3 #Blockchain


Lee Jucoin
2025-08-19 06:40
📣 JuCoin Insights | JuCoin Weekly Report | August 04 – August 10. 📊
Disclaimer:Contains third-party content. Not financial advice.
See Terms and Conditions.
Does Coinbase Pro Support OCO Orders?
Understanding the various order types available on trading platforms is essential for traders aiming to optimize their strategies and manage risk effectively. One such advanced order type is the OCO (One Cancels the Other) order, which allows traders to set two conditional orders simultaneously. This article explores whether Coinbase Pro supports OCO orders, how they work, and their significance in cryptocurrency trading.
What Are OCO Orders?
OCO orders are a sophisticated tool used by traders to automate trade execution based on specific price conditions. Essentially, an OCO combines two separate orders—typically a stop-loss and a take-profit—linked together so that when one of these orders gets executed, the other is automatically canceled. This setup helps traders manage risk while also locking in potential gains without needing constant manual oversight.
For example, suppose you hold Bitcoin (BTC) at $30,000. You might want to sell if it drops to $28,000 (stop-loss) or if it rises to $32,000 (take-profit). Setting an OCO order allows you to specify both these levels simultaneously; if BTC hits $28,000 first, your stop-loss executes and cancels the take-profit order. Conversely, if it reaches $32,000 first, your profit target triggers while canceling the stop-loss.
How Do OCO Orders Function on Trading Platforms?
The core principle behind an OCO order involves linking two conditional orders so that only one can execute at any given time. When placing an OCO:
- You define a stop-loss price where you want your position sold if prices decline.
- You set a take-profit level where you aim to secure gains.
- The platform monitors both conditions concurrently.
Once either condition is met:
- The corresponding order executes.
- The other linked order automatically cancels.
This mechanism ensures efficient trade management by reducing manual intervention and preventing overlapping or conflicting trades from executing simultaneously.
Is Coinbase Pro Compatible with OCO Orders?
Coinbase Pro does support advanced trading features aimed at professional traders who require more control over their trades. Among these features is support for OCO orders, making it possible for users to implement complex strategies involving risk mitigation and profit maximization within a single interface.
While Coinbase Pro’s user interface may not explicitly label this feature as “OCO,” its platform architecture accommodates such conditional ordering functionalities through its advanced trading tools or API integrations designed for algorithmic trading strategies.
It’s important for users interested in utilizing this feature to verify current platform capabilities directly through Coinbase Pro’s official documentation or customer support channels since features may evolve over time with updates or new releases.
Benefits of Using OCO Orders on Coinbase Pro
Implementing OCO orders offers several advantages:
Risk Management: Protect profits by setting automatic exit points when prices decline beyond acceptable levels.
Profit Lock-in: Secure gains once targets are reached without constantly monitoring markets.
Efficiency: Automate complex trade setups that would otherwise require multiple manual entries.
Market Volatility Handling: In highly volatile markets like cryptocurrencies, quick reaction times provided by automated orders can be crucial in avoiding losses or capturing gains swiftly.
Given Coinbase Pro's reputation as a professional-grade exchange offering robust tools suited for active traders and institutions alike — supporting features like margin trading and API access — integrating options like OCO aligns well with its overall strategic focus on providing comprehensive trading solutions.
Limitations & Considerations
Despite their usefulness, there are some considerations when using Oco orders:
Platform Compatibility: Not all exchanges offer native support for true integrated oco functionality via their web interfaces; some rely heavily on APIs which require technical knowledge.
Order Fees: Placing multiple linked orders might incur additional fees depending on the asset class and fee structure of Coinbase Pro.
Market Conditions: During extreme volatility or rapid price swings typical of crypto markets — especially around news events — linked conditional orders may trigger unexpectedly or fail due to slippage issues.
User Familiarity: Properly setting up effective oco strategies requires understanding market dynamics; improper configuration could lead to unintended outcomes such as premature exits or missed opportunities.
It remains crucial for users—especially those new to advanced order types—to educate themselves thoroughly before deploying such strategies live in volatile environments like cryptocurrencies.
How To Place an Order Similar To An Actual EOC Order On Coinbase Pro
While direct support might vary depending on updates and interface changes,
- Use limit/stop-limit combined with API scripting
- Or manually place two separate but related limit/stop-limit instructions
- Monitor closely until fully automated oco functionality becomes officially supported
Always consult official resources before attempting complex setups.
Impact of Advanced Order Types Like Oco On Cryptocurrency Markets
The introduction of sophisticated tools such as oco into platforms like Coinbase Pro influences market behavior significantly:
- It encourages more strategic planning among retail investors who previously lacked access
- It increases overall liquidity due to higher activity driven by automation
- It potentially amplifies volatility during rapid market moves because many participants execute similar risk management tactics simultaneously
Such developments underscore how technological enhancements shape not just individual trader success but also broader market dynamics within digital asset ecosystems.
Final Thoughts
Coinbase Pro's support—or potential future integration—of advanced order types like One Cancels the Other reflects its commitment toward catering professionals' needs while empowering retail traders with powerful tools traditionally reserved for institutional players. Understanding how these mechanisms work enables users not only better risk management but also more strategic participation in cryptocurrency markets’ often unpredictable environment.
By staying informed about available features—and continuously educating oneself about best practices—traders can leverage tools like oco effectively while navigating risks inherent in digital asset investments confidently.
Note: Always verify current platform capabilities directly from official sources before executing complex trades involving conditional order types such as oco.orders


kai
2025-05-26 13:51
Do Coinbase Pro order types include OCO?
Does Coinbase Pro Support OCO Orders?
Understanding the various order types available on trading platforms is essential for traders aiming to optimize their strategies and manage risk effectively. One such advanced order type is the OCO (One Cancels the Other) order, which allows traders to set two conditional orders simultaneously. This article explores whether Coinbase Pro supports OCO orders, how they work, and their significance in cryptocurrency trading.
What Are OCO Orders?
OCO orders are a sophisticated tool used by traders to automate trade execution based on specific price conditions. Essentially, an OCO combines two separate orders—typically a stop-loss and a take-profit—linked together so that when one of these orders gets executed, the other is automatically canceled. This setup helps traders manage risk while also locking in potential gains without needing constant manual oversight.
For example, suppose you hold Bitcoin (BTC) at $30,000. You might want to sell if it drops to $28,000 (stop-loss) or if it rises to $32,000 (take-profit). Setting an OCO order allows you to specify both these levels simultaneously; if BTC hits $28,000 first, your stop-loss executes and cancels the take-profit order. Conversely, if it reaches $32,000 first, your profit target triggers while canceling the stop-loss.
How Do OCO Orders Function on Trading Platforms?
The core principle behind an OCO order involves linking two conditional orders so that only one can execute at any given time. When placing an OCO:
- You define a stop-loss price where you want your position sold if prices decline.
- You set a take-profit level where you aim to secure gains.
- The platform monitors both conditions concurrently.
Once either condition is met:
- The corresponding order executes.
- The other linked order automatically cancels.
This mechanism ensures efficient trade management by reducing manual intervention and preventing overlapping or conflicting trades from executing simultaneously.
Is Coinbase Pro Compatible with OCO Orders?
Coinbase Pro does support advanced trading features aimed at professional traders who require more control over their trades. Among these features is support for OCO orders, making it possible for users to implement complex strategies involving risk mitigation and profit maximization within a single interface.
While Coinbase Pro’s user interface may not explicitly label this feature as “OCO,” its platform architecture accommodates such conditional ordering functionalities through its advanced trading tools or API integrations designed for algorithmic trading strategies.
It’s important for users interested in utilizing this feature to verify current platform capabilities directly through Coinbase Pro’s official documentation or customer support channels since features may evolve over time with updates or new releases.
Benefits of Using OCO Orders on Coinbase Pro
Implementing OCO orders offers several advantages:
Risk Management: Protect profits by setting automatic exit points when prices decline beyond acceptable levels.
Profit Lock-in: Secure gains once targets are reached without constantly monitoring markets.
Efficiency: Automate complex trade setups that would otherwise require multiple manual entries.
Market Volatility Handling: In highly volatile markets like cryptocurrencies, quick reaction times provided by automated orders can be crucial in avoiding losses or capturing gains swiftly.
Given Coinbase Pro's reputation as a professional-grade exchange offering robust tools suited for active traders and institutions alike — supporting features like margin trading and API access — integrating options like OCO aligns well with its overall strategic focus on providing comprehensive trading solutions.
Limitations & Considerations
Despite their usefulness, there are some considerations when using Oco orders:
Platform Compatibility: Not all exchanges offer native support for true integrated oco functionality via their web interfaces; some rely heavily on APIs which require technical knowledge.
Order Fees: Placing multiple linked orders might incur additional fees depending on the asset class and fee structure of Coinbase Pro.
Market Conditions: During extreme volatility or rapid price swings typical of crypto markets — especially around news events — linked conditional orders may trigger unexpectedly or fail due to slippage issues.
User Familiarity: Properly setting up effective oco strategies requires understanding market dynamics; improper configuration could lead to unintended outcomes such as premature exits or missed opportunities.
It remains crucial for users—especially those new to advanced order types—to educate themselves thoroughly before deploying such strategies live in volatile environments like cryptocurrencies.
How To Place an Order Similar To An Actual EOC Order On Coinbase Pro
While direct support might vary depending on updates and interface changes,
- Use limit/stop-limit combined with API scripting
- Or manually place two separate but related limit/stop-limit instructions
- Monitor closely until fully automated oco functionality becomes officially supported
Always consult official resources before attempting complex setups.
Impact of Advanced Order Types Like Oco On Cryptocurrency Markets
The introduction of sophisticated tools such as oco into platforms like Coinbase Pro influences market behavior significantly:
- It encourages more strategic planning among retail investors who previously lacked access
- It increases overall liquidity due to higher activity driven by automation
- It potentially amplifies volatility during rapid market moves because many participants execute similar risk management tactics simultaneously
Such developments underscore how technological enhancements shape not just individual trader success but also broader market dynamics within digital asset ecosystems.
Final Thoughts
Coinbase Pro's support—or potential future integration—of advanced order types like One Cancels the Other reflects its commitment toward catering professionals' needs while empowering retail traders with powerful tools traditionally reserved for institutional players. Understanding how these mechanisms work enables users not only better risk management but also more strategic participation in cryptocurrency markets’ often unpredictable environment.
By staying informed about available features—and continuously educating oneself about best practices—traders can leverage tools like oco effectively while navigating risks inherent in digital asset investments confidently.
Note: Always verify current platform capabilities directly from official sources before executing complex trades involving conditional order types such as oco.orders
Disclaimer:Contains third-party content. Not financial advice.
See Terms and Conditions.
What Are Hardware Wallets and How Secure Are They?
Understanding Hardware Wallets
Hardware wallets are physical devices designed specifically for storing cryptocurrencies securely. Unlike software wallets, which are applications or online platforms vulnerable to hacking, hardware wallets keep private keys offline, significantly reducing the risk of cyberattacks. These devices typically connect to computers or smartphones via USB or Bluetooth, providing a user-friendly interface for managing digital assets without exposing sensitive information to online threats.
The core purpose of a hardware wallet is to safeguard private keys—the cryptographic codes that grant access to your cryptocurrency holdings. By isolating these keys from internet-connected devices, hardware wallets act as a form of cold storage—an offline method that offers enhanced security compared to hot wallets stored on exchanges or software apps.
Key Components and Features
A typical hardware wallet comprises several essential components:
- Secure Private Key Storage: The device's primary function is to store private keys securely within a protected environment.
- Offline Storage: Keys are kept offline at all times unless explicitly used for transactions.
- User Interface: Most models feature small screens and buttons allowing users to verify transaction details directly on the device.
- Backup & Recovery Options: To prevent loss due to damage or theft, many hardware wallets offer seed phrases—mnemonic recovery phrases enabling users to restore access if the device is lost.
These features collectively contribute toward creating an environment where cryptocurrencies can be managed with minimal exposure risk.
Security Advantages of Hardware Wallets
Hardware wallets provide multiple layers of security that make them highly resistant against common cyber threats:
- Offline Storage (Cold Storage): Since private keys never leave the device in an unencrypted form during normal operation, they remain insulated from hacking attempts targeting online systems.
- Physical Security Measures: Many devices incorporate tamper-evident seals and secure elements—specialized chips designed for cryptographic operations—to prevent unauthorized access.
- Two-Factor Authentication (2FA): Some models integrate biometric verification like fingerprint scanning or facial recognition for added protection during transactions.
- Encryption & Firmware Security: Data stored within these devices is encrypted; regular firmware updates patch vulnerabilities and enhance security features over time.
This combination ensures that even if your computer becomes compromised by malware or phishing attacks, your funds remain protected as long as you do not physically lose the device.
Limitations and Risks
Despite their robust security features, hardware wallets are not entirely foolproof. Several risks should be considered:
Physical Loss or Theft: If someone gains physical possession of your wallet along with your seed phrase backup, they could potentially access your funds unless additional safeguards like PIN codes are in place.
Software Vulnerabilities & Firmware Flaws: Occasionally, vulnerabilities may exist within the firmware code of certain models; however, reputable manufacturers regularly release updates addressing such issues promptly.
Human Error & User Practices: Users must exercise caution when handling seed phrases—storing them securely offline—and avoid sharing sensitive information with others. Mistakes such as entering recovery phrases into malicious websites can compromise security.
While these risks exist, proper usage practices significantly mitigate potential threats associated with hardware wallet ownership.
Recent Innovations in Hardware Wallet Technology
The landscape of cryptocurrency storage continues evolving rapidly through technological advancements:
Market Expansion
Major brands like Ledger Nano X, Trezor Model T, and KeepKey have expanded their product lines amid rising demand driven by increased awareness about digital asset safety among investors worldwide.
Cutting-edge Features
Recent developments include:
Quantum-resistant algorithms: As quantum computing advances threaten traditional cryptography methods in future years—a handful of newer models now incorporate algorithms designed specifically against quantum attacks.
Biometric Authentication: Devices integrating fingerprint scanners or facial recognition provide an extra layer beyond PIN codes during transaction approval processes.
Smart Contract Compatibility: Some modern hardware wallets support interactions with decentralized applications (dApps) directly from the device interface—streamlining complex transactions involving smart contracts on blockchain networks like Ethereum.
Regulatory Impact
As governments worldwide tighten regulations around cryptocurrency custody and compliance standards grow stricter—including Know Your Customer (KYC) requirements—the design and operation protocols for hardware wallets adapt accordingly ensuring legal adherence while maintaining user privacy protections.
Timeline: Milestones in Hardware Wallet Development
Understanding key dates helps contextualize how far this technology has come:
- 2008 – The concept emerged alongside Bitcoin’s rise; early ideas focused on secure key management outside online environments
- 2012 – Ledger launched its first product: Ledger Vault
- 2014 – Trezor introduced its first model—the Trezor One
- 2017 – Market boom fueled by surging crypto prices led many new entrants into space
- 2020 – Pandemic accelerated adoption due to increased interest in digital assets
- 2022 – Introduction of advanced features including biometric authentication and quantum-resistant algorithms became mainstream
Future Outlook: Adoption Trends & Challenges Ahead
As cryptocurrencies become more mainstream investment vehicles globally,
- Expect continued growth* in demand for reliable cold storage solutions like hardware wallets will drive innovation further—from integrating multi-signature capabilities to enhancing user experience through seamless interfaces compatible across various platforms.
However,
- Regulatory pressures* might impose stricter operational standards affecting availability across regions,and emerging cybersecurity threats could challenge even sophisticated devices requiring ongoing updates,patches,and vigilance from both manufacturers and users alike.
How Secure Are Hardware Wallets?
Hardware wallets stand out as one of the most secure options available today for storing cryptocurrencies thanks primarily to their offline nature combined with advanced encryption measures — making them resilient against most cyberattacks targeting hot-wallet solutions connected directly online.. Nonetheless,
they require responsible handling regarding seed phrase management,physical safeguarding,and timely firmware updates.. When used correctly within best practices frameworks,hardware wallets offer peace-of-mind assurance suitable even for institutional-grade custody needs while supporting individual investors seeking robust protection against thefts and hacks alike.


Lo
2025-05-14 07:15
What are hardware wallets, and how secure are they?
What Are Hardware Wallets and How Secure Are They?
Understanding Hardware Wallets
Hardware wallets are physical devices designed specifically for storing cryptocurrencies securely. Unlike software wallets, which are applications or online platforms vulnerable to hacking, hardware wallets keep private keys offline, significantly reducing the risk of cyberattacks. These devices typically connect to computers or smartphones via USB or Bluetooth, providing a user-friendly interface for managing digital assets without exposing sensitive information to online threats.
The core purpose of a hardware wallet is to safeguard private keys—the cryptographic codes that grant access to your cryptocurrency holdings. By isolating these keys from internet-connected devices, hardware wallets act as a form of cold storage—an offline method that offers enhanced security compared to hot wallets stored on exchanges or software apps.
Key Components and Features
A typical hardware wallet comprises several essential components:
- Secure Private Key Storage: The device's primary function is to store private keys securely within a protected environment.
- Offline Storage: Keys are kept offline at all times unless explicitly used for transactions.
- User Interface: Most models feature small screens and buttons allowing users to verify transaction details directly on the device.
- Backup & Recovery Options: To prevent loss due to damage or theft, many hardware wallets offer seed phrases—mnemonic recovery phrases enabling users to restore access if the device is lost.
These features collectively contribute toward creating an environment where cryptocurrencies can be managed with minimal exposure risk.
Security Advantages of Hardware Wallets
Hardware wallets provide multiple layers of security that make them highly resistant against common cyber threats:
- Offline Storage (Cold Storage): Since private keys never leave the device in an unencrypted form during normal operation, they remain insulated from hacking attempts targeting online systems.
- Physical Security Measures: Many devices incorporate tamper-evident seals and secure elements—specialized chips designed for cryptographic operations—to prevent unauthorized access.
- Two-Factor Authentication (2FA): Some models integrate biometric verification like fingerprint scanning or facial recognition for added protection during transactions.
- Encryption & Firmware Security: Data stored within these devices is encrypted; regular firmware updates patch vulnerabilities and enhance security features over time.
This combination ensures that even if your computer becomes compromised by malware or phishing attacks, your funds remain protected as long as you do not physically lose the device.
Limitations and Risks
Despite their robust security features, hardware wallets are not entirely foolproof. Several risks should be considered:
Physical Loss or Theft: If someone gains physical possession of your wallet along with your seed phrase backup, they could potentially access your funds unless additional safeguards like PIN codes are in place.
Software Vulnerabilities & Firmware Flaws: Occasionally, vulnerabilities may exist within the firmware code of certain models; however, reputable manufacturers regularly release updates addressing such issues promptly.
Human Error & User Practices: Users must exercise caution when handling seed phrases—storing them securely offline—and avoid sharing sensitive information with others. Mistakes such as entering recovery phrases into malicious websites can compromise security.
While these risks exist, proper usage practices significantly mitigate potential threats associated with hardware wallet ownership.
Recent Innovations in Hardware Wallet Technology
The landscape of cryptocurrency storage continues evolving rapidly through technological advancements:
Market Expansion
Major brands like Ledger Nano X, Trezor Model T, and KeepKey have expanded their product lines amid rising demand driven by increased awareness about digital asset safety among investors worldwide.
Cutting-edge Features
Recent developments include:
Quantum-resistant algorithms: As quantum computing advances threaten traditional cryptography methods in future years—a handful of newer models now incorporate algorithms designed specifically against quantum attacks.
Biometric Authentication: Devices integrating fingerprint scanners or facial recognition provide an extra layer beyond PIN codes during transaction approval processes.
Smart Contract Compatibility: Some modern hardware wallets support interactions with decentralized applications (dApps) directly from the device interface—streamlining complex transactions involving smart contracts on blockchain networks like Ethereum.
Regulatory Impact
As governments worldwide tighten regulations around cryptocurrency custody and compliance standards grow stricter—including Know Your Customer (KYC) requirements—the design and operation protocols for hardware wallets adapt accordingly ensuring legal adherence while maintaining user privacy protections.
Timeline: Milestones in Hardware Wallet Development
Understanding key dates helps contextualize how far this technology has come:
- 2008 – The concept emerged alongside Bitcoin’s rise; early ideas focused on secure key management outside online environments
- 2012 – Ledger launched its first product: Ledger Vault
- 2014 – Trezor introduced its first model—the Trezor One
- 2017 – Market boom fueled by surging crypto prices led many new entrants into space
- 2020 – Pandemic accelerated adoption due to increased interest in digital assets
- 2022 – Introduction of advanced features including biometric authentication and quantum-resistant algorithms became mainstream
Future Outlook: Adoption Trends & Challenges Ahead
As cryptocurrencies become more mainstream investment vehicles globally,
- Expect continued growth* in demand for reliable cold storage solutions like hardware wallets will drive innovation further—from integrating multi-signature capabilities to enhancing user experience through seamless interfaces compatible across various platforms.
However,
- Regulatory pressures* might impose stricter operational standards affecting availability across regions,and emerging cybersecurity threats could challenge even sophisticated devices requiring ongoing updates,patches,and vigilance from both manufacturers and users alike.
How Secure Are Hardware Wallets?
Hardware wallets stand out as one of the most secure options available today for storing cryptocurrencies thanks primarily to their offline nature combined with advanced encryption measures — making them resilient against most cyberattacks targeting hot-wallet solutions connected directly online.. Nonetheless,
they require responsible handling regarding seed phrase management,physical safeguarding,and timely firmware updates.. When used correctly within best practices frameworks,hardware wallets offer peace-of-mind assurance suitable even for institutional-grade custody needs while supporting individual investors seeking robust protection against thefts and hacks alike.
Disclaimer:Contains third-party content. Not financial advice.
See Terms and Conditions.
🔥 Over 100 KOLs and 100,000 new users joined the #JuCoin ecosystem in this event!
✨ A big thank you to all participants for your enthusiastic support! 💚
👉 Register for JuCoin now: https://bit.ly/3BVxlZ2
This is just the beginning — the journey ahead will be even more explosive! 🚀
#Jucoin #JucoinVietnam #Airdrop #CryptoCommunity #Crypto #DeFi #Web3 #Blockchain


Lee Jucoin
2025-08-19 06:42
📣 JuCoin Million Airdrop has successfully concluded! 🎉
Disclaimer:Contains third-party content. Not financial advice.
See Terms and Conditions.
She thinks I’m thinking about other girls… but it’s the BTC bullrun. 📈 I’ve got one shot to retire my entire bloodline - emotionally unavailable until new all-time highs. BTC is king 👑
Check out our YouTube Channel 👉
#BullRun #CryptoMeme #CryptoSkits #CryptoComedy


JuCoin Media
2025-08-06 11:29
🐂 BTC Bullrun – This Is Bigger Than Me, Babe
Disclaimer:Contains third-party content. Not financial advice.
See Terms and Conditions.
Asseto is committed to building a compliant bridge that brings traditional financial assets into the decentralized world. Through smart contracts and multi-stage approval processes, it achieves high security and liquidity, supporting tokenization of stocks, bonds, and other traditional assets. Here are the platform's core highlights:
💰 Three-Layer Architecture:
-
Off-Chain Compliance Layer: KYC/AML verification, fiat settlement, multi-sig custody for asset security
On-Chain Smart Contract Layer: Token issuance/transfer, oracle real-time pricing
Cross-Chain Bridging Layer: Support for Ethereum, BSC, and other multi-chain asset free flow
Modular Governance: Token holders vote to adjust compliance parameters and fee structures
🎯 Privacy & Security Guarantees: 1️⃣ Trusted Execution Environment (TEE): Encrypted user data storage, dedicated audit nodes 2️⃣ Zero-Knowledge Proofs (ZKP): Verify KYC results without exposing sensitive information on-chain 3️⃣ Multi-Signature Timelock: Cross-chain asset transfers remain fully controlled 4️⃣ Third-Party Security Audits: Regular smart contract audits and penetration testing
🏆 Asset Tokenization Process:
-
Asset Custody: Regulated custodians safeguard traditional assets
Contract Minting: On-chain mint transactions generate 1:1 pegged tokens (aStock, aBond)
Cross-Chain Distribution: Bridge tokens to target networks via cross-chain bridge
Redemption & Settlement: Users burn tokens to request redemption, off-chain releases corresponding assets
💡 $ASO Token Economics (100M Total Supply):
-
Rewards & Bribes 60%: Liquidity mining, governance proposal rewards, and "bribe" mechanisms
Public Sale (LBP) 12%: Public offering, initial liquidity foundation
Core Team 11.6%: 3-month lockup, 2-year linear vesting
Protocol Growth 10%: Ecosystem incubation, partner incentives, R&D grants
Community Incentives 4%: Early user airdrops, community activity rewards
Initial Liquidity 2.4%: Trading pair depth support
🔐 Incentive Mechanisms:
-
Staking Yield: Participate in network security verification, earn base APY
Revenue Distribution: Protocol revenues buy back ASO and distribute to stakers
Liquidity Mining: Provide liquidity in designated trading pairs for additional rewards
Governance Voting: Participate in protocol governance, "bribe" mechanism increases voting power
🌟 Dual Yield Model:
-
DeFi Yield: Participate in protocol interest sharing and liquidity mining
Traditional Yield: Connect to traditional asset dividends and coupon payments
Principal Protection: Compliance fund and multi-sig custody emergency compensation mechanism
Community Governance: ASO holders decide asset types, fee adjustments
📱 Supported Asset Types:
-
Current: Stocks, corporate bonds, government bonds, money-market instruments
Planned: Fund shares, commodities expansion
🔮 Participation Process: Complete KYC/AML verification → Deposit funds to compliant custodian account → Mint asset tokens on-chain → DeFi ecosystem applications
⚡ Redemption Service:
-
Standard Redemption: 3-5 business days
Expedited Redemption: 1-2 business days (additional fees)
🛡️ Risk Prevention:
-
Multi-entity custody for risk distribution
Regular audits for transparent operations
Off-chain redundancy backup
Compliance fund emergency mechanisms
Asseto enables traditional financial assets to seamlessly access DeFi ecosystems through innovative compliance architecture, providing investors with "fiat + crypto" composite yields while maintaining regulatory compliance, potentially accelerating traditional asset digitization.
Read the complete compliance mechanism analysis: 👇 https://blog.jucoin.com/asseto-defi-compliance/?utm_source=blog
#Asseto #ASO #CrossChain #KYC



JU Blog
2025-08-05 10:34
🏦 Asseto: Compliant Bridge Between Traditional Assets and DeFi Revolution!
Disclaimer:Contains third-party content. Not financial advice.
See Terms and Conditions.
What Are Layer-2 Scaling Solutions?
Layer-2 scaling solutions are innovative technologies designed to improve the capacity and efficiency of blockchain networks, especially Ethereum. As blockchain technology has gained widespread adoption, the limitations of its underlying architecture have become more apparent. These solutions operate on top of the main blockchain (Layer 1) to handle transactions off-chain or in a more scalable manner, thereby alleviating congestion and reducing transaction costs.
In essence, Layer-2 solutions aim to process many transactions outside the main chain while still maintaining security and decentralization. This approach allows users to enjoy faster transaction speeds and lower fees without compromising the integrity of the network. They are crucial for enabling mainstream adoption of decentralized applications (dApps), DeFi platforms, and other blockchain-based services that require high throughput.
Why Are Layer-2 Solutions Necessary for Blockchain Networks?
Blockchain networks like Ethereum face inherent scalability challenges due to their design. The core issue stems from how transactions are processed on Layer 1—every transaction must be validated by all nodes in the network before being added to a block. As user activity increases, this process causes network congestion, leading to slower processing times and higher gas fees.
High transaction costs can make using blockchain applications prohibitively expensive for everyday users or small-scale developers. For instance, during periods of high demand, gas fees on Ethereum can spike dramatically, making simple transfers or interactions with smart contracts costly.
Layer-2 solutions address these issues by shifting most transactional load off-chain or onto secondary layers that can process multiple transactions simultaneously before settling them back onto Layer 1 periodically. This not only reduces congestion but also enhances user experience by providing faster confirmation times and significantly lower costs—key factors for broader adoption.
Types of Layer-2 Scaling Solutions
There are several distinct approaches within layer-2 scaling strategies:
Off-Chain Transactions
State Channels
State channels enable participants to conduct numerous transactions privately without broadcasting each one individually on the main chain. Only opening and closing balances need on-chain validation; all intermediate steps occur off-chain within a secure channel established between parties.
Payment Channels
A subset focused specifically on transferring funds efficiently between two parties through an off-chain channel—examples include Lightning Network for Bitcoin or Raiden Network for Ethereum.
Sidechains
Sidechains are independent blockchains linked securely with their parent chain via bridges or two-way pegs. They operate separately but periodically synchronize with the main chain through cryptographic proofs or validators’ consensus mechanisms. Sidechains allow developers flexibility in customizing features such as consensus algorithms while processing transactions independently from Ethereum’s mainnet.
Rollups
Rollups represent a promising class of layer-2 solutions that bundle multiple transactions into a single batch before submitting it back onto Layer 1:
- Optimistic Rollups: Assume transactions are valid unless challenged within a challenge period; they rely heavily on fraud proofs.
- ZK-Rollups (Zero-Knowledge Rollups): Use cryptographic proofs called zero-knowledge proofs to verify batches instantly without revealing individual transaction details—offering both scalability benefits and privacy enhancements.
Each type offers trade-offs regarding security guarantees, complexity, cost-efficiency, and privacy considerations—all vital factors influencing their suitability across different use cases.
Recent Developments in Layer-2 Technologies
The evolution of layer-2 solutions is closely tied with ongoing upgrades within Ethereum itself:
Transitioning to Proof-of-Stake (PoS)
Ethereum's move from proof-of-work (PoW) towards proof-of-stake aims at reducing energy consumption while improving scalability through shard chains combined with rollup integrations—a significant step toward sustainable growth alongside layer-two innovations.
Adoption Trends
Major projects like Optimism and Arbitrum have successfully implemented optimistic rollup frameworks that enable fast finality at low costs while maintaining strong security models aligned with Ethereum’s standards. Polygon has also emerged as an alternative sidechain solution offering fast settlement times suitable for gaming dApps or microtransactions due to its high throughput capabilities.
Regulatory Environment Impact
As governments worldwide develop clearer regulations around cryptocurrencies—and potential compliance requirements—the development landscape may shift accordingly: fostering innovation where regulatory clarity exists but potentially hindering progress where restrictions tighten around certain types of decentralized activities involving cross-border payments or privacy-preserving features offered by some layer-two protocols.
Challenges Facing Layer-Two Scaling Solutions
Despite their advantages, deploying effective layer-two systems involves overcoming several hurdles:
- Security Risks: While designed carefully, some implementations might introduce vulnerabilities if not properly audited—for example: compromised bridges connecting sidechains could threaten overall ecosystem safety.
- Interoperability Issues: Ensuring seamless communication among various layer-two protocols remains complex; fragmented ecosystems could hinder user experience if interoperability isn’t prioritized.
- User Adoption Barriers: For widespread acceptance beyond crypto enthusiasts—and into mainstream markets—layer-two tools must demonstrate clear benefits such as ease-of-use alongside tangible cost savings; otherwise skeptics may hesitate transitioning from traditional methods.
The Future Outlook for Blockchain Scalability
Layer-2 scaling solutions will continue evolving rapidly as part of broader efforts toward achieving mass adoption in decentralized finance (DeFi), non-fungible tokens (NFTs), gaming platforms—and beyond. Their success hinges not only on technological robustness but also regulatory support that fosters innovation while protecting consumers’ interests.
Emerging trends suggest increased integration between different types of second-layer protocols—for example: combining rollups with state channels—to optimize performance further across diverse application scenarios. Additionally, advancements in cryptography—including zero knowledge proofs—are likely to enhance privacy features alongside scalability improvements.
By addressing current limitations related to security risks and interoperability challenges through ongoing research & development efforts—and fostering clearer regulatory frameworks—the ecosystem can unlock new levels of efficiency necessary for mainstream acceptance.
This comprehensive overview underscores why layered scaling strategies are pivotal—not just technical upgrades but foundational enablers—to realize blockchain’s full potential at scale responsibly and securely.


JCUSER-F1IIaxXA
2025-05-22 09:39
What are layer-2 scaling solutions, and why are they necessary?
What Are Layer-2 Scaling Solutions?
Layer-2 scaling solutions are innovative technologies designed to improve the capacity and efficiency of blockchain networks, especially Ethereum. As blockchain technology has gained widespread adoption, the limitations of its underlying architecture have become more apparent. These solutions operate on top of the main blockchain (Layer 1) to handle transactions off-chain or in a more scalable manner, thereby alleviating congestion and reducing transaction costs.
In essence, Layer-2 solutions aim to process many transactions outside the main chain while still maintaining security and decentralization. This approach allows users to enjoy faster transaction speeds and lower fees without compromising the integrity of the network. They are crucial for enabling mainstream adoption of decentralized applications (dApps), DeFi platforms, and other blockchain-based services that require high throughput.
Why Are Layer-2 Solutions Necessary for Blockchain Networks?
Blockchain networks like Ethereum face inherent scalability challenges due to their design. The core issue stems from how transactions are processed on Layer 1—every transaction must be validated by all nodes in the network before being added to a block. As user activity increases, this process causes network congestion, leading to slower processing times and higher gas fees.
High transaction costs can make using blockchain applications prohibitively expensive for everyday users or small-scale developers. For instance, during periods of high demand, gas fees on Ethereum can spike dramatically, making simple transfers or interactions with smart contracts costly.
Layer-2 solutions address these issues by shifting most transactional load off-chain or onto secondary layers that can process multiple transactions simultaneously before settling them back onto Layer 1 periodically. This not only reduces congestion but also enhances user experience by providing faster confirmation times and significantly lower costs—key factors for broader adoption.
Types of Layer-2 Scaling Solutions
There are several distinct approaches within layer-2 scaling strategies:
Off-Chain Transactions
State Channels
State channels enable participants to conduct numerous transactions privately without broadcasting each one individually on the main chain. Only opening and closing balances need on-chain validation; all intermediate steps occur off-chain within a secure channel established between parties.
Payment Channels
A subset focused specifically on transferring funds efficiently between two parties through an off-chain channel—examples include Lightning Network for Bitcoin or Raiden Network for Ethereum.
Sidechains
Sidechains are independent blockchains linked securely with their parent chain via bridges or two-way pegs. They operate separately but periodically synchronize with the main chain through cryptographic proofs or validators’ consensus mechanisms. Sidechains allow developers flexibility in customizing features such as consensus algorithms while processing transactions independently from Ethereum’s mainnet.
Rollups
Rollups represent a promising class of layer-2 solutions that bundle multiple transactions into a single batch before submitting it back onto Layer 1:
- Optimistic Rollups: Assume transactions are valid unless challenged within a challenge period; they rely heavily on fraud proofs.
- ZK-Rollups (Zero-Knowledge Rollups): Use cryptographic proofs called zero-knowledge proofs to verify batches instantly without revealing individual transaction details—offering both scalability benefits and privacy enhancements.
Each type offers trade-offs regarding security guarantees, complexity, cost-efficiency, and privacy considerations—all vital factors influencing their suitability across different use cases.
Recent Developments in Layer-2 Technologies
The evolution of layer-2 solutions is closely tied with ongoing upgrades within Ethereum itself:
Transitioning to Proof-of-Stake (PoS)
Ethereum's move from proof-of-work (PoW) towards proof-of-stake aims at reducing energy consumption while improving scalability through shard chains combined with rollup integrations—a significant step toward sustainable growth alongside layer-two innovations.
Adoption Trends
Major projects like Optimism and Arbitrum have successfully implemented optimistic rollup frameworks that enable fast finality at low costs while maintaining strong security models aligned with Ethereum’s standards. Polygon has also emerged as an alternative sidechain solution offering fast settlement times suitable for gaming dApps or microtransactions due to its high throughput capabilities.
Regulatory Environment Impact
As governments worldwide develop clearer regulations around cryptocurrencies—and potential compliance requirements—the development landscape may shift accordingly: fostering innovation where regulatory clarity exists but potentially hindering progress where restrictions tighten around certain types of decentralized activities involving cross-border payments or privacy-preserving features offered by some layer-two protocols.
Challenges Facing Layer-Two Scaling Solutions
Despite their advantages, deploying effective layer-two systems involves overcoming several hurdles:
- Security Risks: While designed carefully, some implementations might introduce vulnerabilities if not properly audited—for example: compromised bridges connecting sidechains could threaten overall ecosystem safety.
- Interoperability Issues: Ensuring seamless communication among various layer-two protocols remains complex; fragmented ecosystems could hinder user experience if interoperability isn’t prioritized.
- User Adoption Barriers: For widespread acceptance beyond crypto enthusiasts—and into mainstream markets—layer-two tools must demonstrate clear benefits such as ease-of-use alongside tangible cost savings; otherwise skeptics may hesitate transitioning from traditional methods.
The Future Outlook for Blockchain Scalability
Layer-2 scaling solutions will continue evolving rapidly as part of broader efforts toward achieving mass adoption in decentralized finance (DeFi), non-fungible tokens (NFTs), gaming platforms—and beyond. Their success hinges not only on technological robustness but also regulatory support that fosters innovation while protecting consumers’ interests.
Emerging trends suggest increased integration between different types of second-layer protocols—for example: combining rollups with state channels—to optimize performance further across diverse application scenarios. Additionally, advancements in cryptography—including zero knowledge proofs—are likely to enhance privacy features alongside scalability improvements.
By addressing current limitations related to security risks and interoperability challenges through ongoing research & development efforts—and fostering clearer regulatory frameworks—the ecosystem can unlock new levels of efficiency necessary for mainstream acceptance.
This comprehensive overview underscores why layered scaling strategies are pivotal—not just technical upgrades but foundational enablers—to realize blockchain’s full potential at scale responsibly and securely.
Disclaimer:Contains third-party content. Not financial advice.
See Terms and Conditions.
